Last updated on 23 September 2025
Important or Recent Updates
| Historic Updates | Date |
|---|---|
| New DSM7.2 Container Manager Update (Beta/RC) | 30/04/2023 |
| Amended the devices mounted to the container as had reports of better performance with them. | 17/05/2023 |
| Added additional security option to the compose to restrict the container from gaining new privileges as well as umask variable | 25/10/2023 |
In this guide I am going to take you through the setup of Jellyfin in Container Manager using Docker Compose.
Does my Synology support Hardware Transcoding?
Before we do anything else, you need to make sure your model of Synology has hardware transcoding capabilities. You need to do a quick lookup via the linked Google Sheet below, this is updated by Plex however it’s perfectly relevant for Jellyfin.
If you find that your model does not support hardware transcoding you can jump back over to the standard guide.
Let’s Begin
As usual, it’s important you complete the three preceding guides which will get your folder structure and docker, user and bridge network setup.
- Docker Package, SSD and Memory Recommendations
- Step 1: Directory Setup Guide
- Step 2: Setting up a restricted Docker user
- Step 3: Setting up a Docker Bridge Network (synobridge)
Folder Setup
Let’s start by getting some folders set up for the container to use. Open up File Station create the following.
/docker/projects/jellyfin-compose
/docker/jellyfin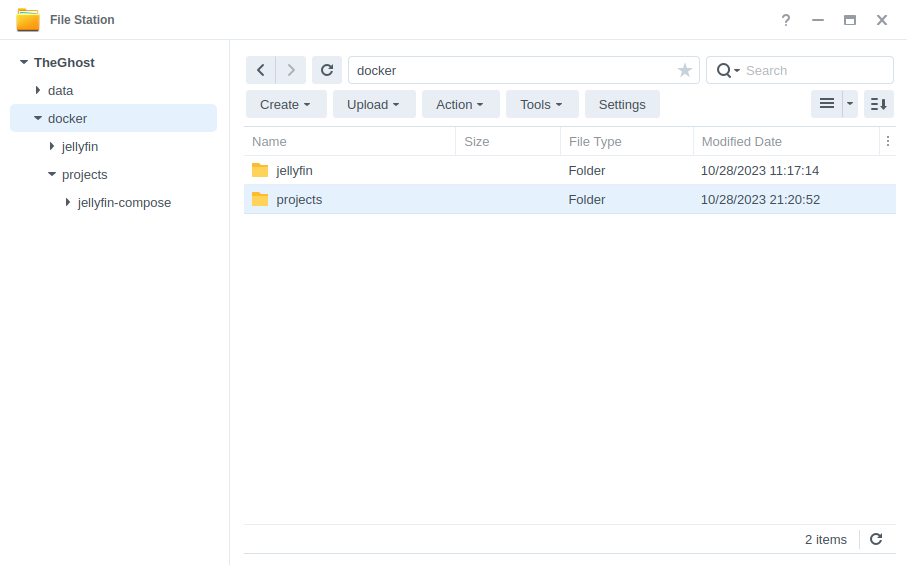
Container Manager
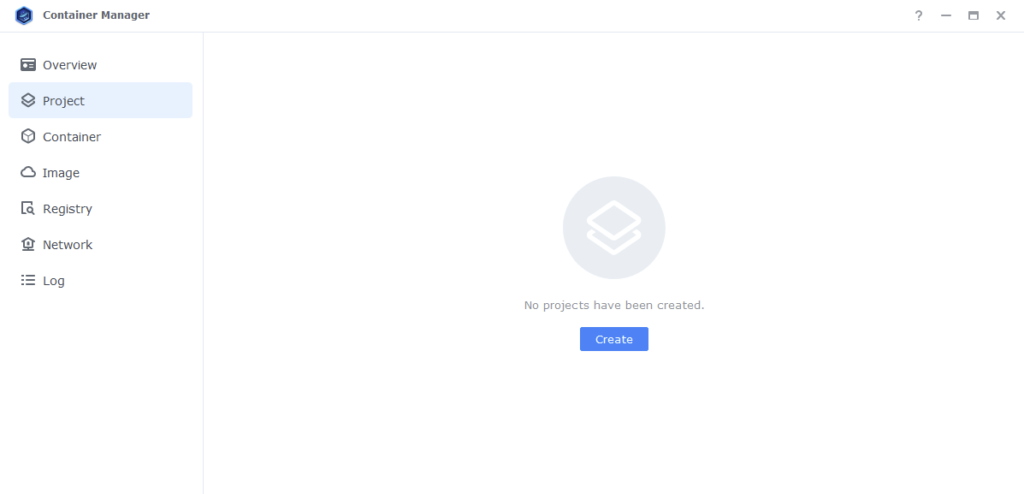
Next we are going to set up a ‘Project’ in Container Manager. Open up Container Manager and click on Project then on the right-hand side click ‘Create’.
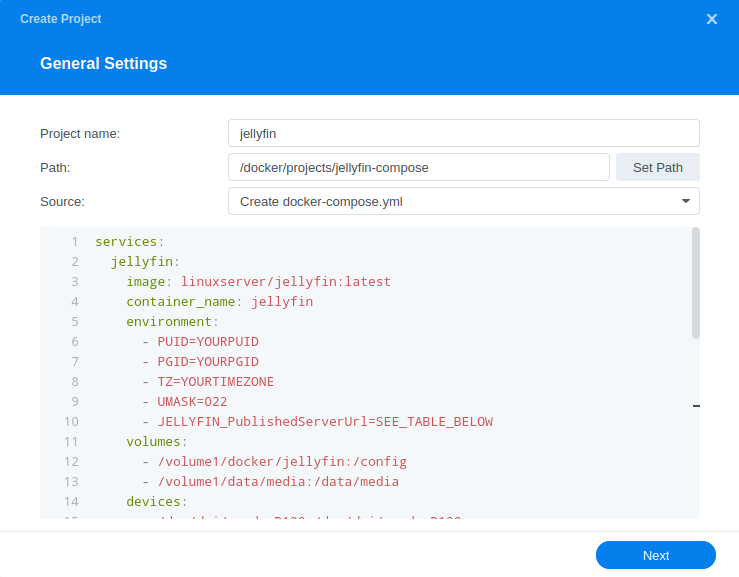
In the next screen we will set up our General Settings, enter the following:
| Section | Setting |
|---|---|
| Project Name: | jellyfin |
| Path: | /docker/projects/jellyfin-compose |
| Source: | Create docker-compose.yml |
Next we are going to drop in our docker compose configuration copy all the code in the box below and paste it into line ‘1’ just like the screenshot.
What on earth is a Docker Compose? Docker Compose allows us to define how Docker should set up one or more containers within a single configuration file. This file is yaml formatted and Container Manager uses the Projects feature to manage them.
services:
jellyfin:
image: linuxserver/jellyfin:latest
container_name: jellyfin
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- UMASK=022
- JELLYFIN_PublishedServerUrl=SEE_TABLE_BELOW
volumes:
- /volume1/docker/jellyfin:/config
- /volume1/data/media:/data/media
devices:
- /dev/dri/renderD128:/dev/dri/renderD128
- /dev/dri/card0:/dev/dri/card0
ports:
- 8096:8096/tcp #web port
- 8920:8920/tcp #optional
- 7359:7359/udp #optional
network_mode: synobridge
security_opt:
- no-new-privileges:true
restart: alwaysThe two optional ports in the above can be removed if you will not use them. 7359 is for automated discovery of Jellyfin by the apps, and 8920 is the HTTPS port which is useful if not using the reverse proxy later in the guide.
Environment Variables
We need to make some changes in order for the container to have the correct permissions to save its configuration files and to have access to your media.
| Variable | Value |
|---|---|
| PUID | (required) The UID you obtained in the user setup guide |
| PGID | (required) The GID you obtained in the user setup guide |
| TZ | (required) Your timezone wikipedia.org/wiki/List_of_tz_database_time_zones |
| JELLYFIN_PublishedServerUrl | This will be your NAS IP or if you are going to be accessing via your DDNS address use this. (You can change this later if you wish) |
Volumes
We can now pass through our file paths into the container they are mounted using the volume’s section of the compose file.
I have pre-filled this section to pass the correct paths, the only thing that you may need to change is the /volume1/ if your file paths are on a different volume.
Click ‘Next’
You do not need to enable anything on the ‘Web portal settings’ screen click ‘Next’ again.
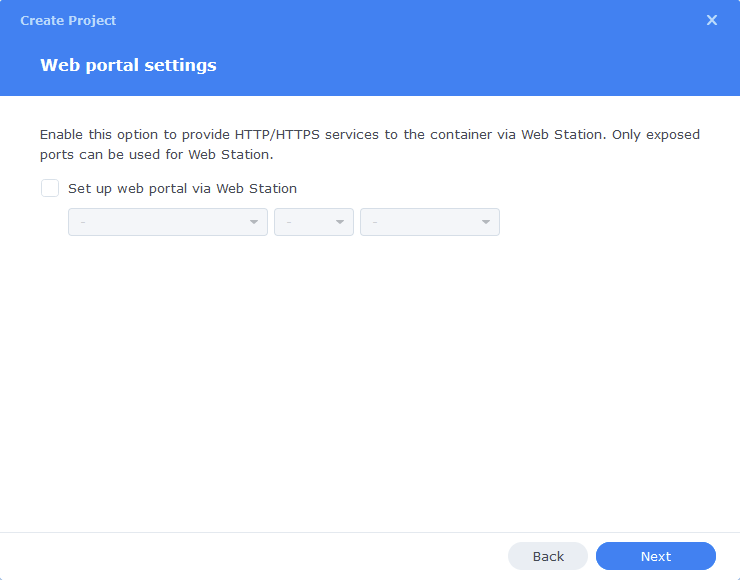
On the final screen click ‘Done’ which will begin the download of the container images and once downloaded they will be launched!
The image will now be downloaded and extracted. You should see ‘Code 0’ when it has finished.
You will now see your Jellyfin running and should have a green status on the left-hand side.
Firewall Exceptions
(Skip if you don’t have the Firewall configured)
If you have the Synology Firewall enabled please see this additional guide for further info on exceptions and correct set up.
Jellyfin Initial Setup
After a few minutes you should be able to access the server and go through the initial Jellyfin setup by going to the IP of your NAS in your browser followed by port 8096.
e.g. 192.168.0.30:8096
When adding movies or shows they will be located in the /data/media folder.
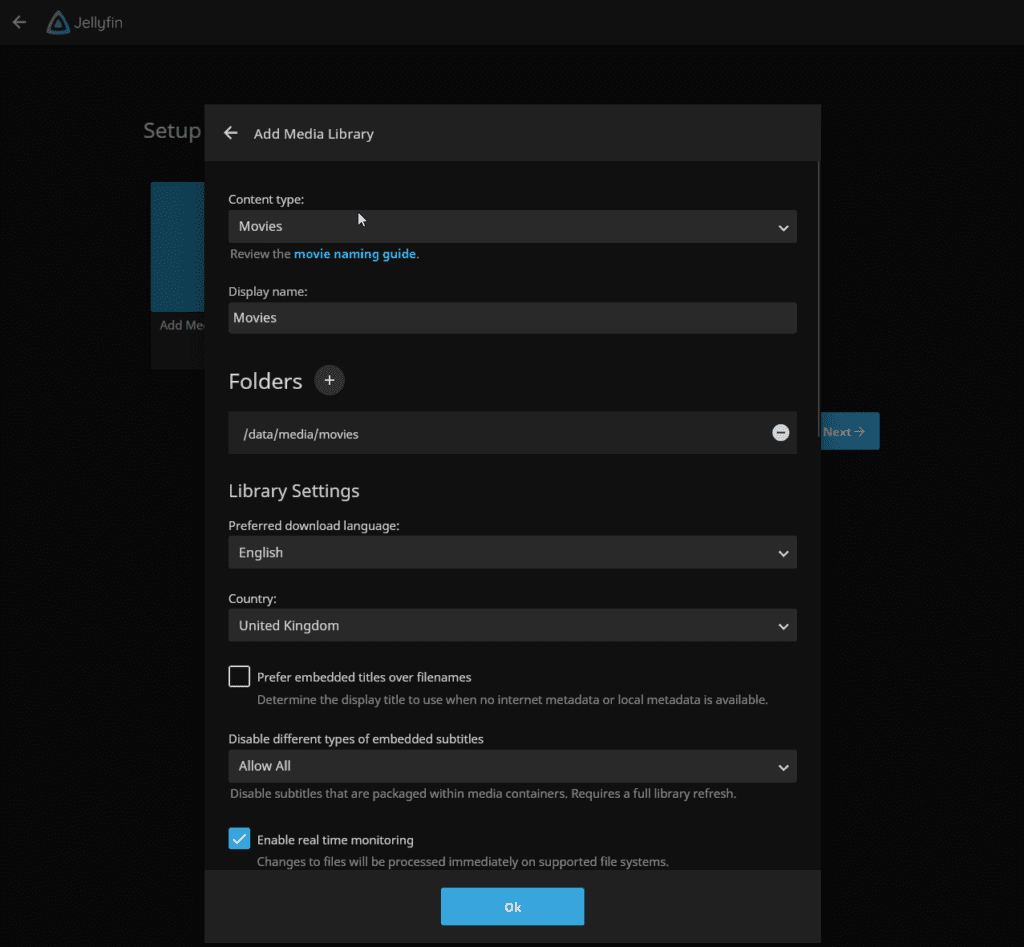
How to enable Hardware Transcoding
The last steps for initial set up are to enable the hardware transcode features for your NAS.
On the main Jellyfin homescreen, click on the hamburger menu on the top left and then ‘Dashboard’ in the ‘Administration’ section
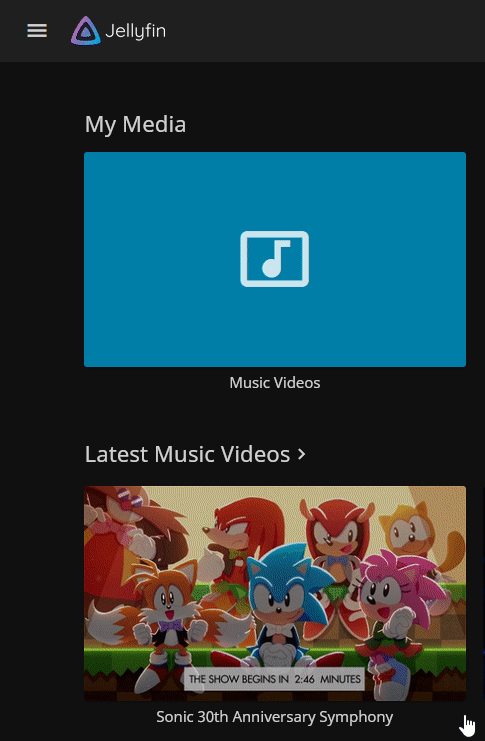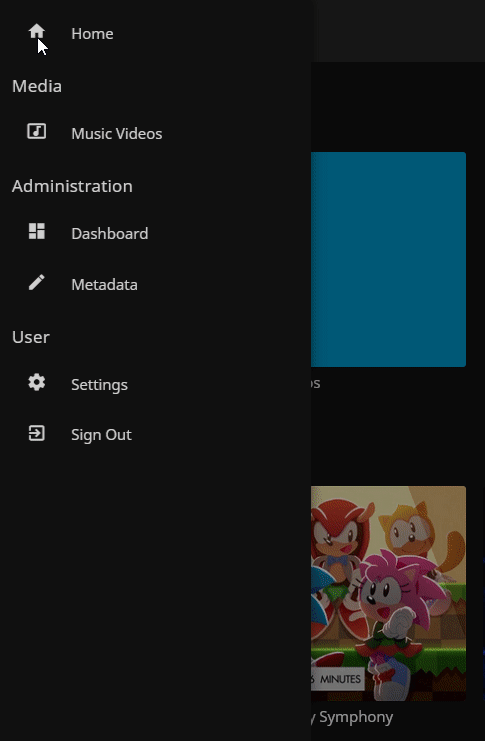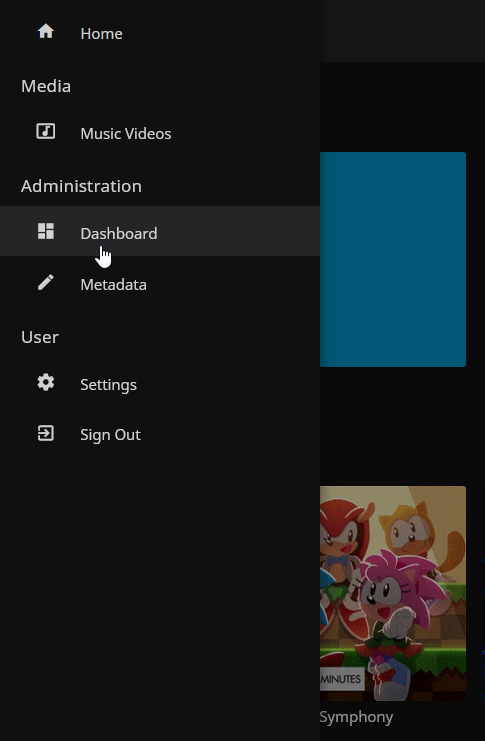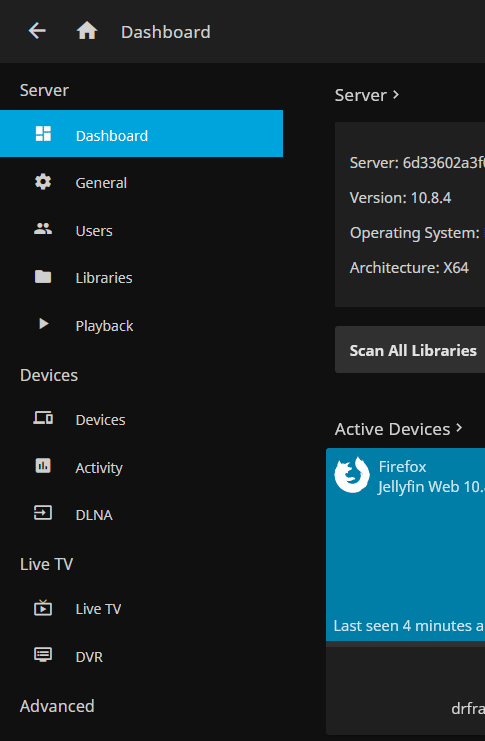
On the next screen select ‘Playback’ where you will now be able to select from the first drop-down from ‘None’ to ‘Intel QSV Video’, you do not need to enter anything into the QSV Device section that will appear.
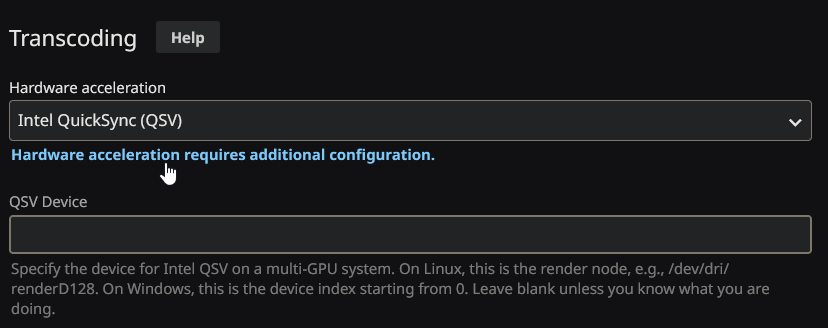
Below are the settings you would enable for a Gemini Lake based NAS such as the 920+/720+/420+/220+. You can cross-check between the Synology CPU list and the table on the QSV Wikipedia page as to the hardware functions your NAS supports.
Please note that I have included the items I changed from the default values – e.g. if the default item is turned off, and I turn it on then it appears in the table.
| Setting changed from the default. | Variable to use |
|---|---|
| H264 | Ticked |
| HEVC | Ticked |
| MPEG2 | Ticked |
| VC1 | Ticked |
| VP8 | Ticked |
| VP9 | Ticked |
| HEVC 10bit | Ticked |
| VP9 10bit | Ticked |
| Allow Encoding in HEVC format | Ticked |
| Enable VPP Tone Mapping | Ticked |
| Enable Tone Mapping | Unticked |
Once you have made the required change press ‘Save’ and you are now free to change any other settings you wish in relation to the server, make sure you check out the fantastic documentation from Jellyfin.
Remote Access
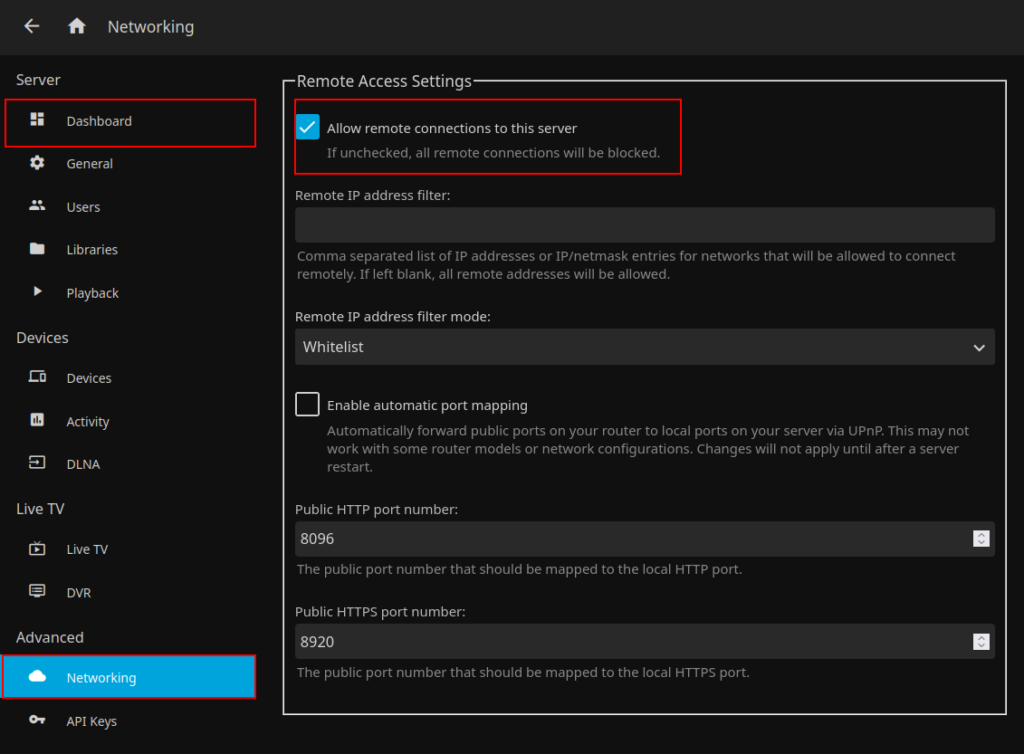
If you are going to be using your set-up outside your LAN you will also need to enable the following options to allow access and also to restrict bandwidth
- Allow remote connections to this server
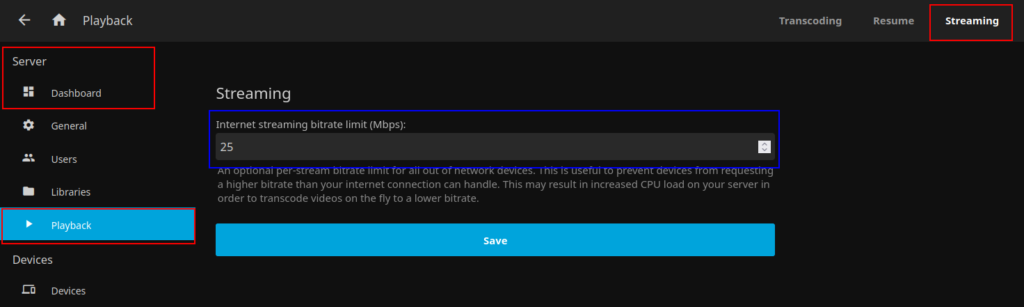
- Streaming
In order to limit upload bandwidth you can also set an overall limit for streams, this is useful if you or other users will be trying to play back files larger than your upload bandwidth can handle
External Access
You have some choices when it comes to making your new container accessible from outside your home network, these come with different levels of security and convenience. This mini section is generic but covers the basics of getting this guide up and running and is entirely optional.
- Synology’s DDNS (Dynamic Domain Name System) with a TLS Certificate and Reverse Proxy
This is useful if you have some family members or friends that need access to something like Overseerr or Jellyseer and is covered below. - Tailscale or Wireguard VPN
If just you or close family in your household are accessing these services, and you don’t want to expose them to the internet this would be the more secure choice. See my other separate guides. - Cloudflare Tunnels
I don’t currently use these, so I would recommend watching the Wundertech guide on how they work.
A note on Double NAT or CGNAT
Unfortunately more ISPs are moving to these methods of address allocation as the IPv4 address space is getting low on available addresses. If your ISP is doing this your choices are more limited.
You can test if this is the case by checking the WAN IP on your Router/Modem settings and then comparing it to the one shown on portchecker.co. If they are different you are likely Double NAT and will either need to see if you can pay your ISP for a standard IPv4 address or use Tailscale or Cloudflare Tunnels for access.
Using the built-in tools on DSM
The first step of this process is to forward port 443 on your Router to your NAS IP Address, how you do this will depend on your router model, so please refer to its manual.
Router (External):443 > NASIP (Internal):443
Next make sure you have registered for a Synology Account as we are going to be using their DDNS service. https://account.synology.com/en-uk/register/ If you already have this set up move to the next step.
DDNS (Dynamic Domain Name System)
A DDNS address allows you to get external access to your container via an address provided by Synology, this is useful on home internet connections where your ISP will change your IP address on a semi-regular basis.
In the DSM Control panel go to ‘External Access’ and then to the ‘DDNS’ tab
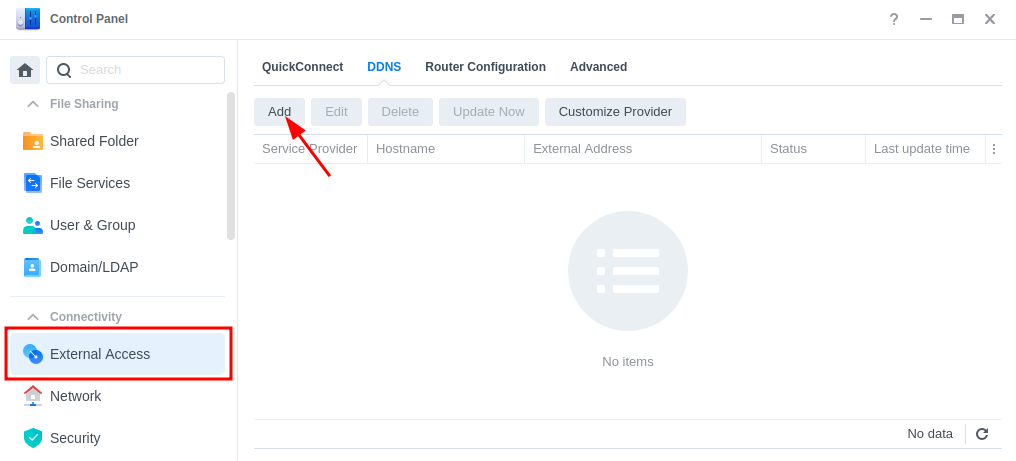
Click on ‘Add’, then fill out the following sections.
| Section | Value |
|---|---|
| Service Provider | Synology |
| Hostname | This will be the unique address just for you so keep the name generic. minecraft.synology.me = BAD myawesomenas.synology,me =GOOD |
| Email: | Log into your Synology account |
| External Address (IPv4) | This should be filled in automatically |
| External Address (IPv6) | This should be filled in automatically if your ISP is using IPv6 |
| Get a Cert from Let’s Encrypt | Tick this box |
| Enable Heartbeat | Tick this box |
Now press OK, DSM will apply your settings. It can take a few moments to set up and the DSM interface will refresh. You will likely receive a certificate error which you will need to accept to get back into DSM.
Reverse Proxy
We are going to set up a reverse proxy subdomain for the address you just register. This means you and your users can access the container without using a port number as it will route all traffic through the secure 443 port.
Go back into the Control Panel and access the ‘Login Portal’ then in the ‘Advanced’ tab click ‘Reverse Proxy’ and then click on ‘Create’.
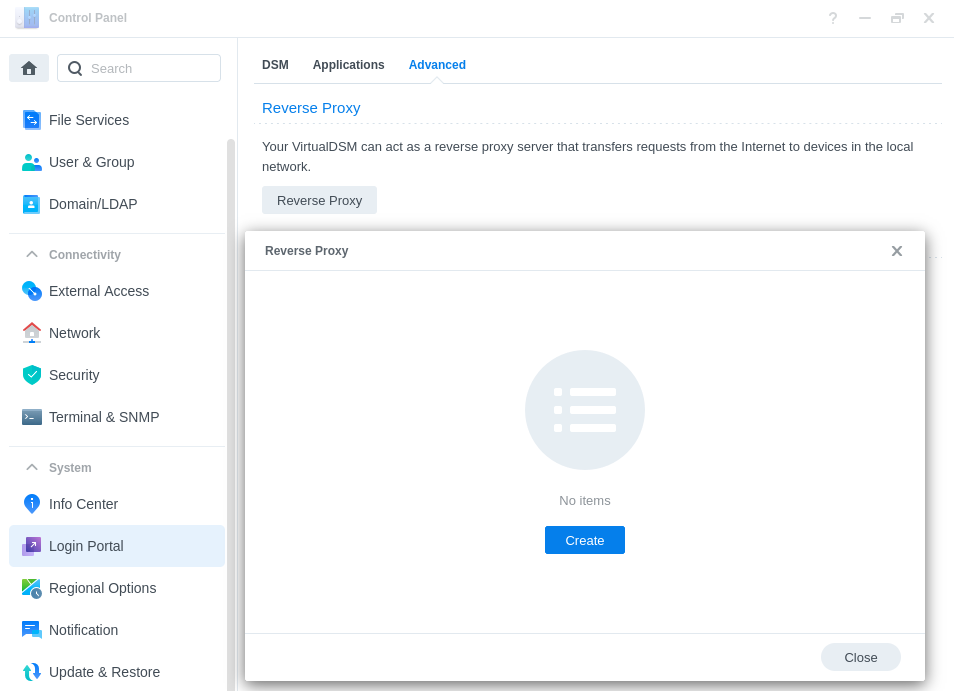
We are now going to enter some rules, so when you or your users access the URL specified the request will automatically be sent to the containers web UI.
Use the settings below, you will need to amend the Hostname sections in line with the hostname you registered earlier, and the IP of your NAS.
| Setting | Value |
|---|---|
| Reverse Proxy Name: | Give it a meaningful name in line with the container you are setting up. |
| Protocol: | HTTPS |
| Hostname: | containername.xxx.synology.me ‘containername‘ will be the name you want to use to access this container ‘.xxx.synology.me‘ will be the exact name you registered earlier |
| Port: | 443 |
| Protocol: | HTTP |
| Hostname: | ‘localhost’ or your NAS IP address |
| Port: | The UI Port Number from the yaml in the guide you are following |
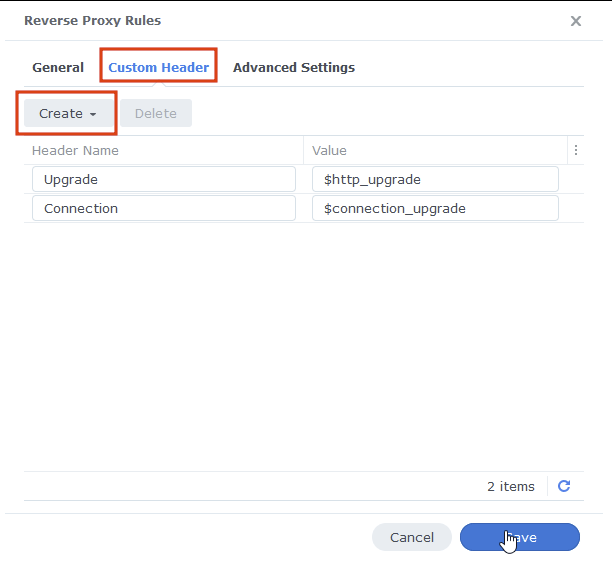
On the second tab ‘Custom Header’ click on Create then WebSocket, this will add two entries for WebSockets to function correctly, you can now press save.
You should now be able to access the web UI of the container by going to the address you just set up in the reverse proxy, it will be a secure connection, and you should have no certificate errors.
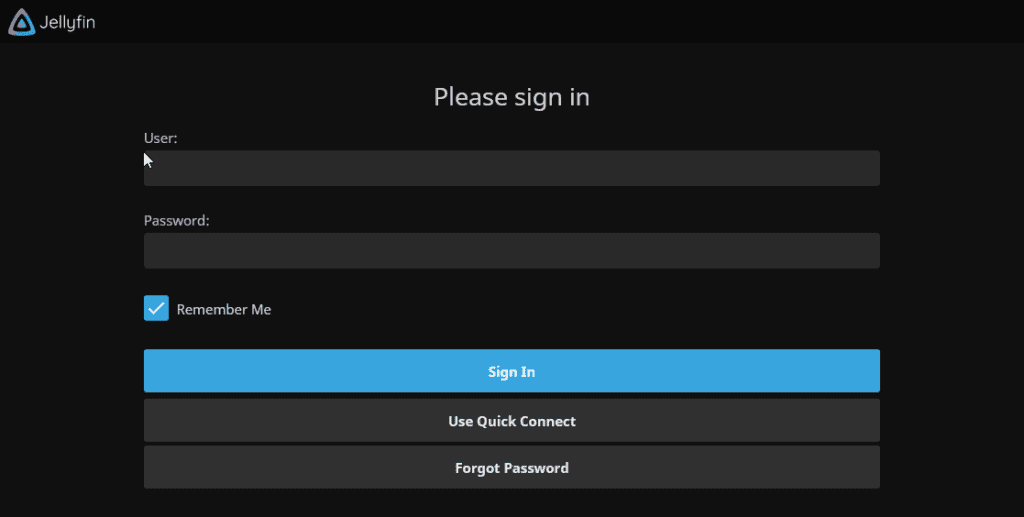
You can now log in with the username and password you created earlier, the same address is used in the Android and iPhone apps.
Looking for some help, join our Discord community
If you are struggling with any steps in the guides or looking to branch out into other containers join our Discord community!

Buy me a beverage!
If you have found my site useful please consider pinging me a tip as it helps cover the cost of running things or just lets me stay hydrated. Plus 10% goes to the devs of the apps I do guides for every year.


