Important or Recent Updates
| Historic Updates | Date |
|---|---|
| New DSM7.2 Container Manager Update | 22/04/2023 |
We are now going to set up a Docker Bridge Network, we are doing this for consistency across the guides here. It also allows us to have more control over the ports containers use in case we want to avoid certain port ranges that DSM uses.
While most containers will happily work without doing this step it is good practice to set up a specific Bridge rather than using the default bridge or Network Host mode.
Let’s Begin
Open up the Container Manager and go into the Network tab.
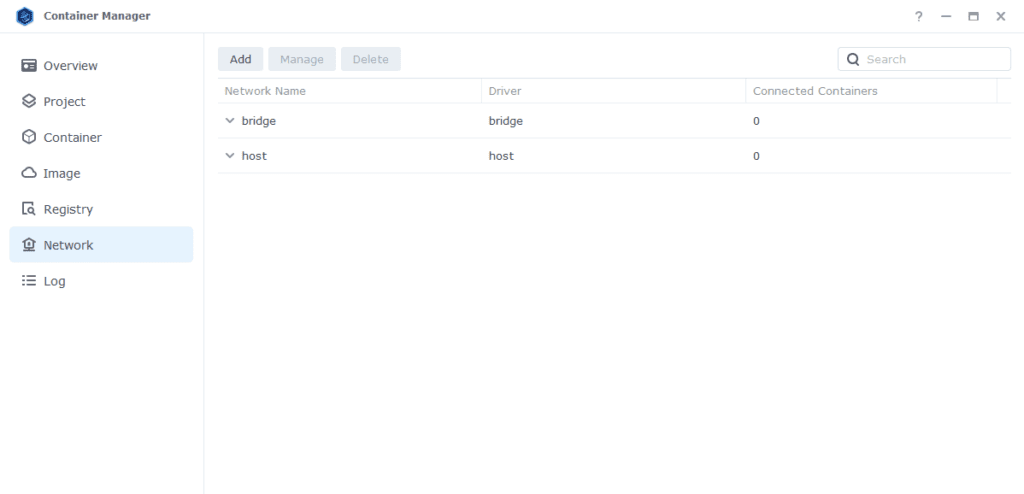
Next click on ‘Add’ which brings up the settings screen. In here we are going to specify the following values.
| Section | Setting |
|---|---|
| Network Name | synobridge (you can change this if you wish) |
| IPv4 Configuration | Manual |
| Subnet | 172.20.0.0/16 |
| network: iprange | 172.20.0.0/16 |
| Gateway | 172.20.0.1 |
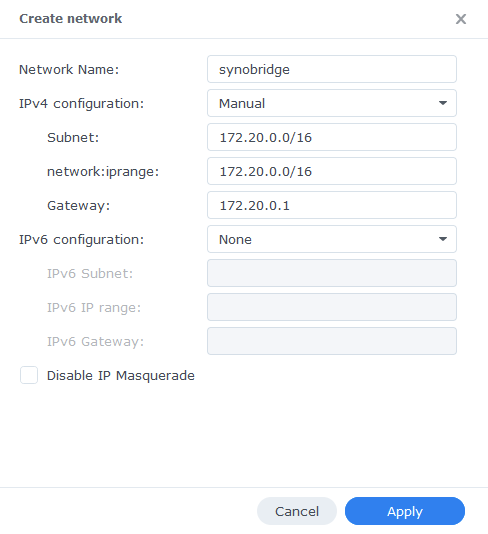
Now click ‘Apply’ which will take you back to the original screen.
That’s it the Bridge is now ready for containers to be attached to it. You can go back to the guide you were following.
Optional Steps if you have the Synology Firewall Enabled
If you have the Synology Firewall enabled and configured to block incoming or outgoing connections you will need to do this step. Otherwise, you will have issues with your containers being able to contact each other.
I have another page with some other info around the Firewall but its pretty high level see it here
Go into Control Panel > Security > Firewall
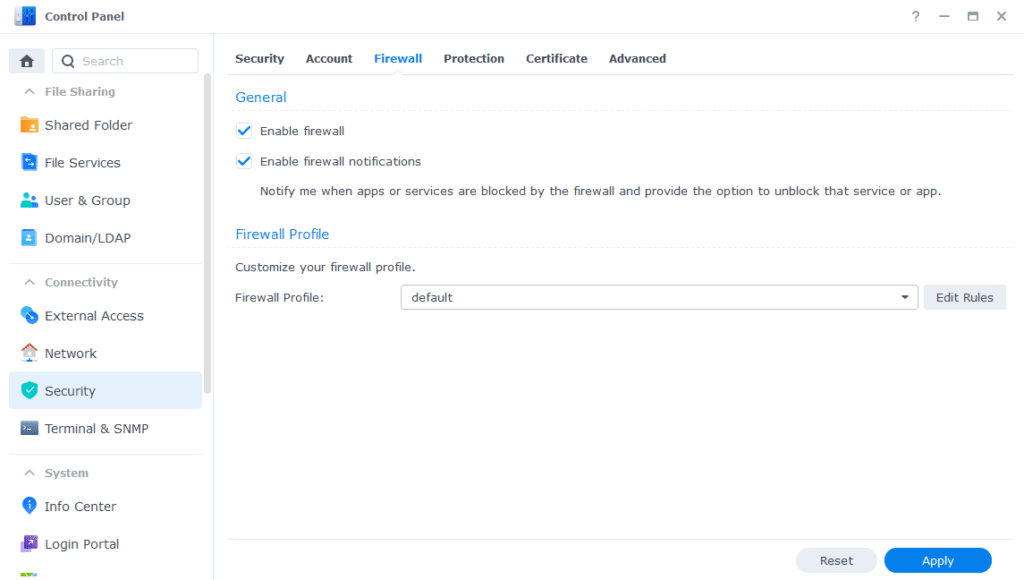
Click on Edit Rules and in the screen that appears click on ‘Create’
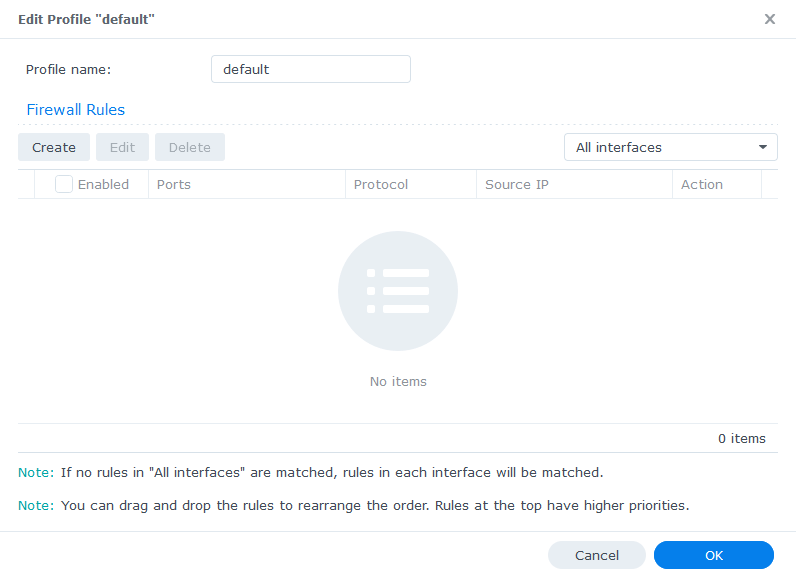
In the first screen select ‘All’ and ‘Specific IP’ then press ‘Select’
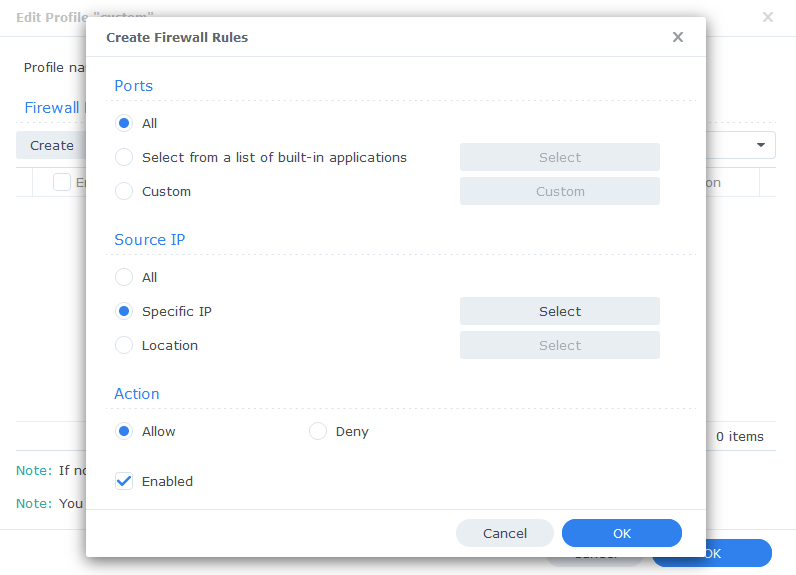
Then select ‘IP Range’ and enter ‘172.20.0.1’ in ‘From:’ and ‘172.20.255.254’ in ‘To:’
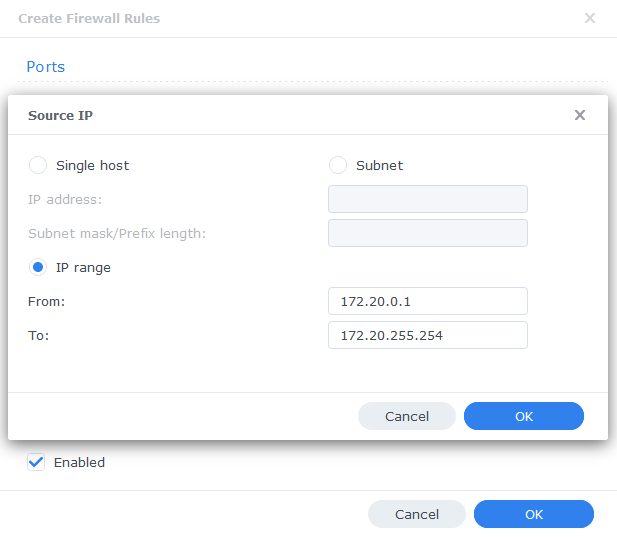
Press OK until you are back to the main Firewall screen and press Apply.
You can now go back to the guide you were following.

The firewall screenshot shows no rules
– I assume there should be something there as I see this page
https://drfrankenstein.co.uk/firewall-general-setup-and-exceptions/
shows a rule to deny everything, ok so I’ll add a deny all rule.
“Otherwise, you will have issues with your containers being able to contact each other” = is it missing a “not” = if (initially) everything is denied, then the containers can’t contact each other, right? Hence we are adding “allow” rule
Hey catching up on comments after a week away. I will add a sub-link to the other page so it’s clearer, as I assume you are following that step as you already got the Firewall in place..
Hello there, I set up the synobridge, but the 172.20.0.0/16 and 172.20.0.1 gateway is already taken by Paperless-ngx, so i changed the numbers to 172.19.0.0/16 and gateway to 172.19.0.1. What all do i need to change for this to work? I’m an amateur at this stuff but I have a lot to learn. Surely there is a fix for me, I just dont know what all I need to change to point the programs to the correct network
Hey – no issues with using alternative IPs – just whenever you see mention of 172.20 just use the one you used for the bridge 🙂