Last updated on 2 September 2025
Important or Recent Updates
| Historic Updates | Date |
|---|---|
| New DSM7.2 Container Manager Update (Beta/RC) | 26/04/2023 |
| Added watchtower labels to the compose to allow updates and changed the proxies to off by default | 06/05/2023 |
| Removed the Watchtower ‘Depends On’ Labels as they do not successfully update the GlueTUN container. Added an Exclusion label to the GlueTUN container, so it can just be manually updated. | 11/05/2023 |
| Update includes: Firewall Input Ports for when your provider offers port forwarding, also a note in relation to volumes and added PUID/PGID settings for GlueTUN | 14/06/2023 |
| Update for WireGuard Kernel Module Install which reduces overall CPU usage for WireGuard connections Please note if you previously followed this guide you can follow the new section to update your existing set-up. | 21/09/2023 |
| Added Health checks to dependent containers | 25/09/2023 |
| Added an addition element to the compose to restrict the container from gaining additional privileges and umask environment variable | 25/10/2023 |
| Updated with new steps to obtain and change WebUI password | 21/11/2023 |
| Issue with passwords has been fixed in 4.6.2 so removed tty line from yaml | 29/11/2023 |
| Swapped YAML to use WireGuard by default (Thanks Bob) (Thanks Andy for the original suggestion) | 22/01/2024 |
| Amended the start-up script folders to align with the changes made late November (Apologies) | 25/01/2024 |
| Added – UPDATER_PERIOD=24h variable in order to ensure the latest server lists for your provider all pulled once a day | 27/04/2024 |
| Reworded the Port Forwarding section and added a new docker mod for those using ProtonVPN to update the qBit port forwarding (listening port) automatically | 18/08/2024 |
| NATMAP for Proton removed from the guide as GSP is the better choice now | 19/08/2024 |
| Adjusted the GSP Mod for Proton (removed un-needed for the addresses) | 04/12/2024 |
| Added pre-configured settings for AirVPN and Proton VPN including steps to get the details for these providers | 21/12/2024 |
| General bits of re-write, added generic WireGuard and OpenVPN compose removed the qBittorrent path edits as its no longer required and working via the UI! | 27/12/2024 |
| Edited the ProtonVPN compose as I had the wrong lines for WireGuard in it, apologies. | 29/12/2024 |
| – Removed the depends_on for GlueTUN as it’s not required – Added GSP Mod directly into the ProtonVPN Compose – Layered in a new section for the upcoming changes to GlueTUN 3.41 Control Server Auth where required. – General layout and wording tweaks! | 07/01/2025 |
| Fixed my inability to copy and paste and moved the GSP mod back to the correct container (I put them in the GlueTUN section sorry!!) | 14/01/2025 |
| Further GSP mod changes – I think we may have nailed the config!! ready for GlueTUN 3.40 – Removed the volume mount for gluetun/auth – Removed the GSP_QBT_ADDR variable – Removed the “quotes” around the GSP_API_KEY | 21/01/2025 |
| Further ProtonVPN updates now that 3.40 GlueTUN has been released it now can use the default ProtonVPN Compose rather than a Custom compose. We are testing a further change that removes the need for GSPMod which will be a further update likely over this weekend. | 31/01/2025 |
| OK this should be the final update for Proton for a little while (I hope) GSP Mod is no longer required, replaced with a command. Thanks to the team on Discord for testing and sorting this out! | 03/02/2025 |
| While not really good for torrents I have added N0rdVPN (OpenVPN) compose as we get a lot of people stuck in long contracts with them looking for help on Discord | 07/04/2025 |
| Removed the ports for for the Shadowsocks and Proxy as they are rarely used and if you need them they are easily re-added, changed ProtonVPN compose to use Quad9 for DNS rather than Cloudflare as this has caused some issues with some Private trackers. | 20/06/2025 |
What are qBittorrent and GlueTUN?
qBittorrent is a torrent downloader and GlueTUN is the Docker container that has pre-configured VPN connections for numerous VPN providers.
Before you start check the GlueTUN Wiki to see if your provider is on the supported list.
Also, if you are yet to choose a provider I currently use AirVPN which has nice easy port forwarding and is P2P friendly. This is my affiliate link if you fancy signing up.
Useful external links for this guide
GlueTUN Wiki
GlueTUN Docker GitHub
Linuxserver qBittorrent Container GitHub
qBittorrent Forums
Let’s Begin
In this guide I will take you through the steps to get qBittorrent up and running in Docker and a separate GlueTUN VPN container. By having a separate container for the VPN connection we can use it in the future for other applications.
In order for you to successfully use this guide please complete the three preceding guides
- Docker Package, SSD and Memory Recommendations
- Step 1: Directory Setup Guide
- Step 2: Setting up a restricted Docker user
- Step 3: Setting up a Docker Bridge Network (synobridge)
Folder Setup
Let’s start by getting some folders set up for the containers to use. Open up File Station create the following.
/docker/projects/vpnproject-compose
/docker/gluetun
/docker/qbittorrent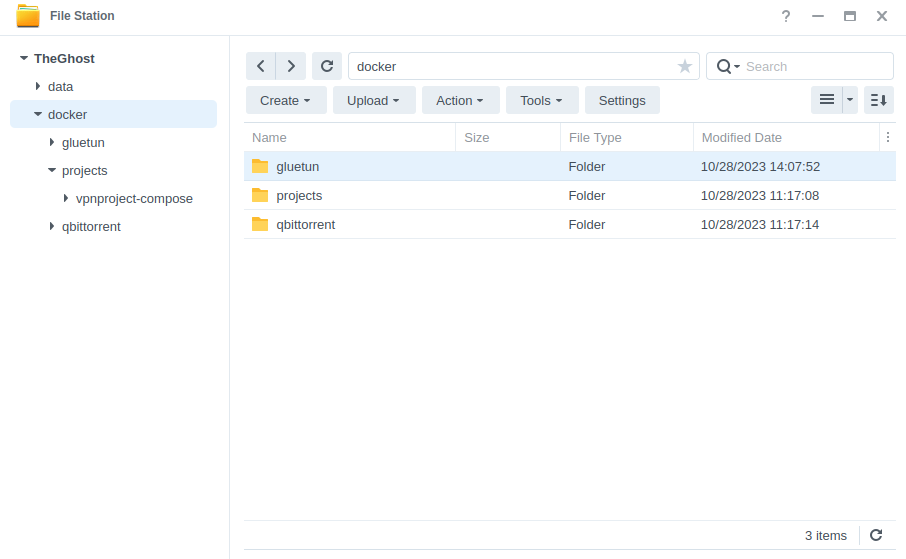
Setting up the TUN start up script
In order for the VPN connection to work we need to make sure the TUN Interface is available to make the connection to a VPN provider. In order to ensure it is available even after a reboot we will set up a small script.
Open up Control Panel and then click on Task Scheduler
Next click on Create, Triggered Task then User Defined Script.
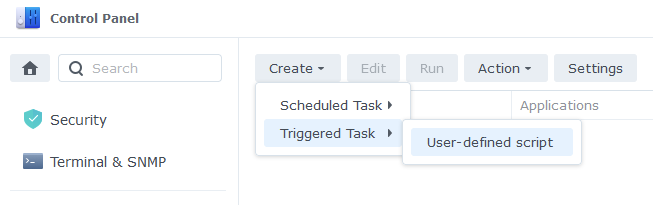
Enter the following:
| Section | Setting |
|---|---|
| Task: | VPNTUN |
| User: | root |
| Event: | Boot-up |
| Enabled | Tick |
On the Task Settings tab copy and paste the code below in the ‘User-Defined script’ section. It will look like screenshot.
#!/bin/sh -e
insmod /lib/modules/tun.ko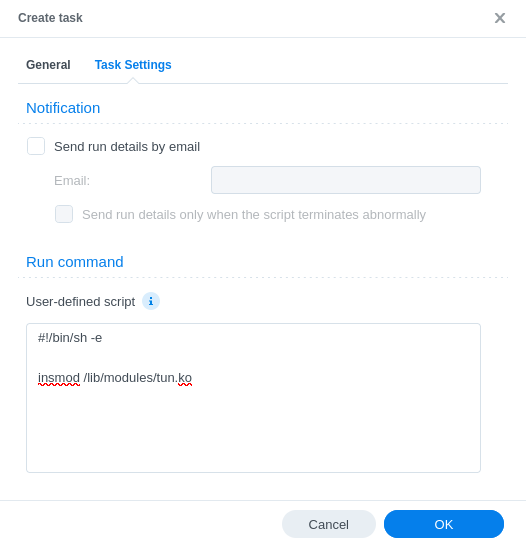
You can now press OK and agree to the warning message. Next run the script which will enable the TUN device.
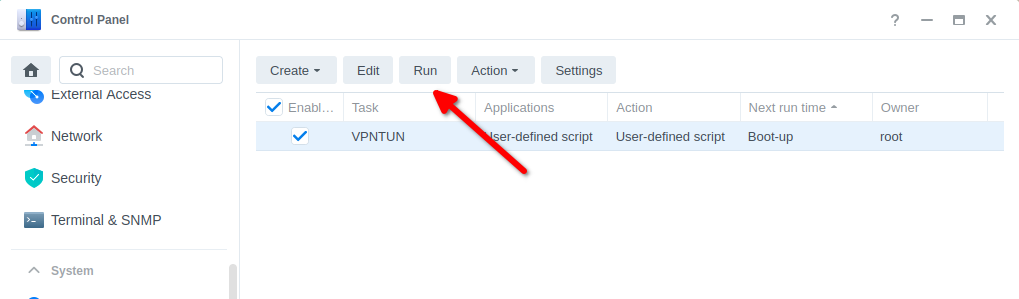
You can now move on to the next step.
WireGuard Kernel Module (not required for OpenVPN)
The default GlueTUN WireGuard setup uses the ‘Userspace’ implementation of WireGuard which requires higher CPU resources. For example a 40MiB/s download via qBittorrent uses up to 176% in CPU (1.7 Cores) on my 1821+.
By installing the appropriate Kernel Module this reduces down to 1 or 2% which frees up the CPU for other tasks.
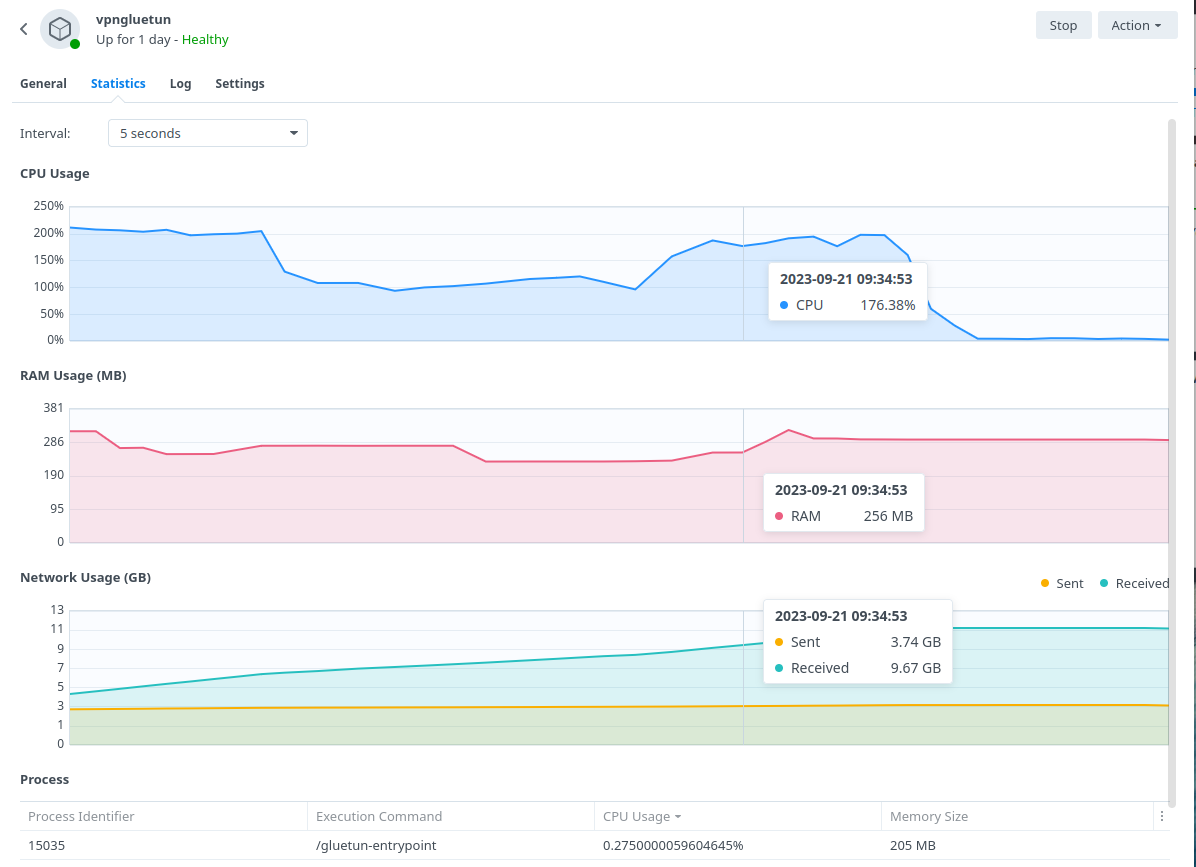
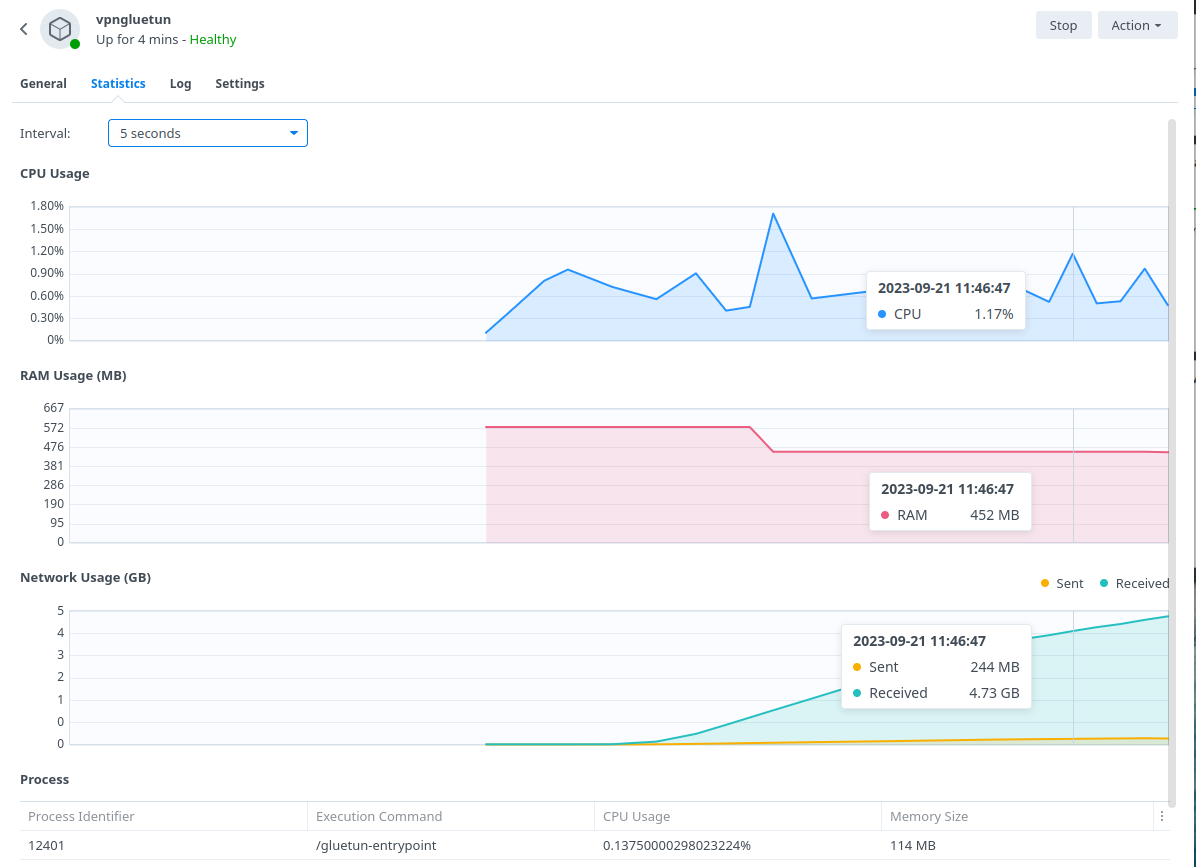
BlackVoid.club have put together a Kernel Module for Synology which allows Gluetun to use the lower level Kernel to perform Wireguard duties make sure you drop them a thanks as this would not be possible without them!
While on first glances it looks like a long installation process the page details a number of methods. I recommend having a read taking note of warnings and also if you want to build your own module it tells you how.
The TLDR is below.
- Find your model of NAS under the correct DSM version section (If you are following this guide it will be 7.2 or above) and download the pre compiled .spk file
- Head into Package Center and click ‘Manual Install’ on the top right and install the .spk file and untick the box to run after install
- Reboot
- SSH Into your NAS (Just like in the User Setup guide) and elevate yourself to root by typing
sudo -iand entering your password - Enter this command and press enter to start up the module
/var/packages/WireGuard/scripts/start
You should now be able to see the WireGuard package running in Package Center. Please note while I will try my best to support in relation to this module I may have to refer you on if it is a specific technical issue.
On to the next part.
Container Manager Project (aka Docker Compose)
Next we are going to set up a ‘Project’ in Container Manager, a project is used when you want multiple containers to all be loaded together and often rely on each other to function. In our case we want qBittorrent to load and talk to the GlueTUN VPN container.
Open up Container Manager and click on Project then on the right-hand side click ‘Create’
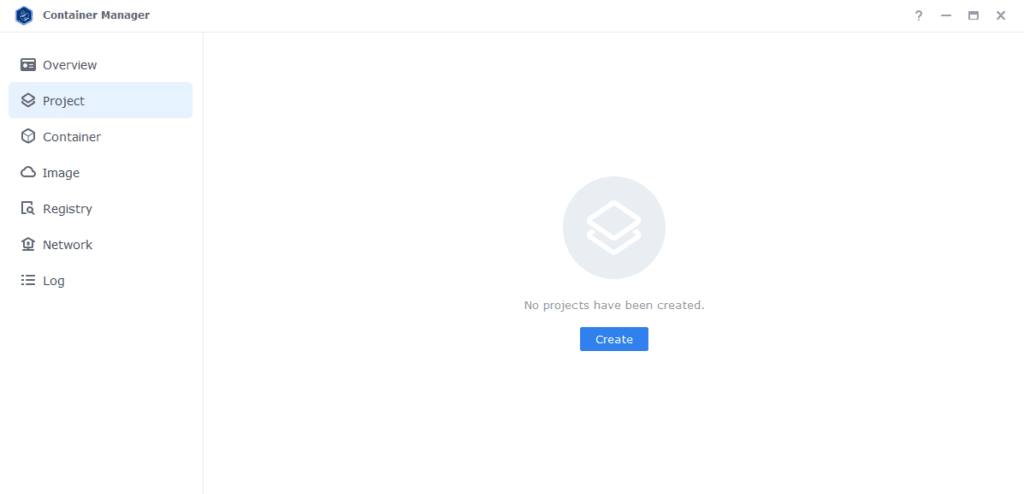
In the next screen we will set up our General Settings, enter the following:
| Section | Setting |
|---|---|
| Project Name: | vpn-project |
| Path: | /docker/projects/vpnproject-compose |
| Source: | Create docker-compose.yml |
OK we are now going to drop in our Docker Compose configuration (YAML) – You will find some presets below – A basic WireGuard or OpenVPN setup which covers the majority of providers, but I have also provided some standard WireGuard presets for AirVPN and ProtonVPN, select the one that is appropriate for you.
See the GlueTUN Wiki for your specific provider steps or amendments
Docker Compose Presets
Standard OpenVPN Preset
services:
gluetun:
image: qmcgaw/gluetun:latest
container_name: gluetun
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 8090:8090/tcp # port for qbittorrent
volumes:
- /volume1/docker/gluetun:/gluetun
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- VPN_SERVICE_PROVIDER=NAMEOFYOURPROVIDER
- VPN_TYPE=openvpn
- OPENVPN_USER=abc
- OPENVPN_PASSWORD=abc
- SERVER_COUNTRIES=VPNSERVERCOUNTRY #Change based on the Wiki
- HTTPPROXY=off #change to on if you wish to enable
- SHADOWSOCKS=off #change to on if you wish to enable
- FIREWALL_OUTBOUND_SUBNETS=172.20.0.0/16,192.168.0.0/24
# - FIREWALL_VPN_INPUT_PORTS=12345
- UPDATER_PERIOD=24h
network_mode: synobridge
labels:
- com.centurylinklabs.watchtower.enable=false
security_opt:
- no-new-privileges:true
restart: always
qbittorrent:
image: linuxserver/qbittorrent:latest
container_name: qbittorrent
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- WEBUI_PORT=8090
- UMASK=022
volumes:
- /volume1/docker/qbittorrent:/config
- /volume1/data/torrents:/data/torrents
network_mode: service:gluetun # run on the vpn network
security_opt:
- no-new-privileges:true
restart: alwaysStandard WireGuard Preset
services:
gluetun:
image: qmcgaw/gluetun:latest
container_name: gluetun
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 8090:8090/tcp # port for qbittorrent
volumes:
- /volume1/docker/gluetun:/gluetun
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- VPN_SERVICE_PROVIDER=NAMEOFYOURPROVIDER
- VPN_TYPE=wireguard
- WIREGUARD_PRIVATE_KEY=YOUR-PRIVATE-KEY
- WIREGUARD_PRESHARED_KEY
- WIREGUARD_ADDRESSES=10.x.x.x
- SERVER_COUNTRIES=VPNSERVERCOUNTRY #Change based on the Wiki
- HTTPPROXY=off #change to on if you wish to enable
- SHADOWSOCKS=off #change to on if you wish to enable
- FIREWALL_OUTBOUND_SUBNETS=172.20.0.0/16,192.168.0.0/24
# - FIREWALL_VPN_INPUT_PORTS=12345
- UPDATER_PERIOD=24h
network_mode: synobridge
labels:
- com.centurylinklabs.watchtower.enable=false
security_opt:
- no-new-privileges:true
restart: always
qbittorrent:
image: linuxserver/qbittorrent:latest
container_name: qbittorrent
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- WEBUI_PORT=8090
- UMASK=022
volumes:
- /volume1/docker/qbittorrent:/config
- /volume1/data/torrents:/data/torrents
network_mode: service:gluetun # run on the vpn network
security_opt:
- no-new-privileges:true
restart: alwaysAirVPN WireGuard Preset
How to obtain your Wireguard Details from AirVPN
- Login to your AirVPN account and go to the Client Area
- Click on
VPN Devicesand create a new device namedGlueTUN(you can name this anything) - Back in the Client Area select
Config Generatorand select the following- Linux
- Turn on WireGuard
- Choose the newly created
GlueTUNdevice (Note this will not show if you only have a single device created) - Select your preferred Server or Region
- Click Generate and download the config file.
From the downloaded config file use the following parts and populate them into the compose below.
- Address = 10.141.x.x/32 #Nothing after this part
- PrivateKey = uFdxxxxxxxxxxxxxxxx
- PresharedKey = 4s2xxxxxxxxxxxxxxxxxxxx
In addition, there are some extra variables you can add to tell GlueTUN to use a specific Country, Region, Server etc. See this on the GlueTUN wiki and add based on your preferences.
Next you will want to set up port forwarding, so back in the Client Area, select Manage Ports and request a random port ensuring you turn on P2P and then assign the port to your GlueTUN device.
You will now enter this port number into the section of the compose labelled Firewall VPN Input Ports, make a note of this port number as you will set it as the Listening Port for the torrent client during its setup process. You can now continue with the guide to make the other general edits.
services:
gluetun:
image: qmcgaw/gluetun:latest
container_name: gluetun
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 8090:8090/tcp # port for qbittorrent
volumes:
- /volume1/docker/gluetun:/gluetun
environment:
- VPN_SERVICE_PROVIDER=airvpn
- VPN_TYPE=wireguard
- WIREGUARD_PRIVATE_KEY=
- WIREGUARD_PRESHARED_KEY=
- WIREGUARD_ADDRESSES=
- TZ=Europe/London
- PUID=1234
- PGID=65432
- HTTPPROXY=off
- SHADOWSOCKS=off
- FIREWALL_OUTBOUND_SUBNETS=172.20.0.0/16,192.168.0.0/24
- FIREWALL_VPN_INPUT_PORTS=12345
- UPDATER_PERIOD=24h
network_mode: synobridge
labels:
- com.centurylinklabs.watchtower.enable=false
security_opt:
- no-new-privileges:true
restart: always
qbittorrent:
image: linuxserver/qbittorrent:latest
container_name: qbittorrent
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- WEBUI_PORT=8090
- UMASK=022
volumes:
- /volume1/docker/qbittorrent:/config
- /volume1/data/torrents:/data/torrents
network_mode: service:gluetun # run on the vpn network
security_opt:
- no-new-privileges:true
restart: alwaysProtonVPN WireGuard Preset
Please ensure you have a Paid subscription to ProtonVPN otherwise this compose will not function.
Thanks to Geebru on Discord for the settings and screenshots
- Use any name you like
- Select GNU/Linux
- Turn on the following
- Block malware only
- Moderate NAT
- NAT-PMP (Port Forwarding)
- VPN Accelerator
- Select a server that is physcially close to you and low usage
- Ensure its a P2P server (double left and right arrows)
You can then layer in the WireGuard details it provides you into the compose below.
(Note Proton Wireguard keys expire after 12 months so you will need to renew them after that period of time)
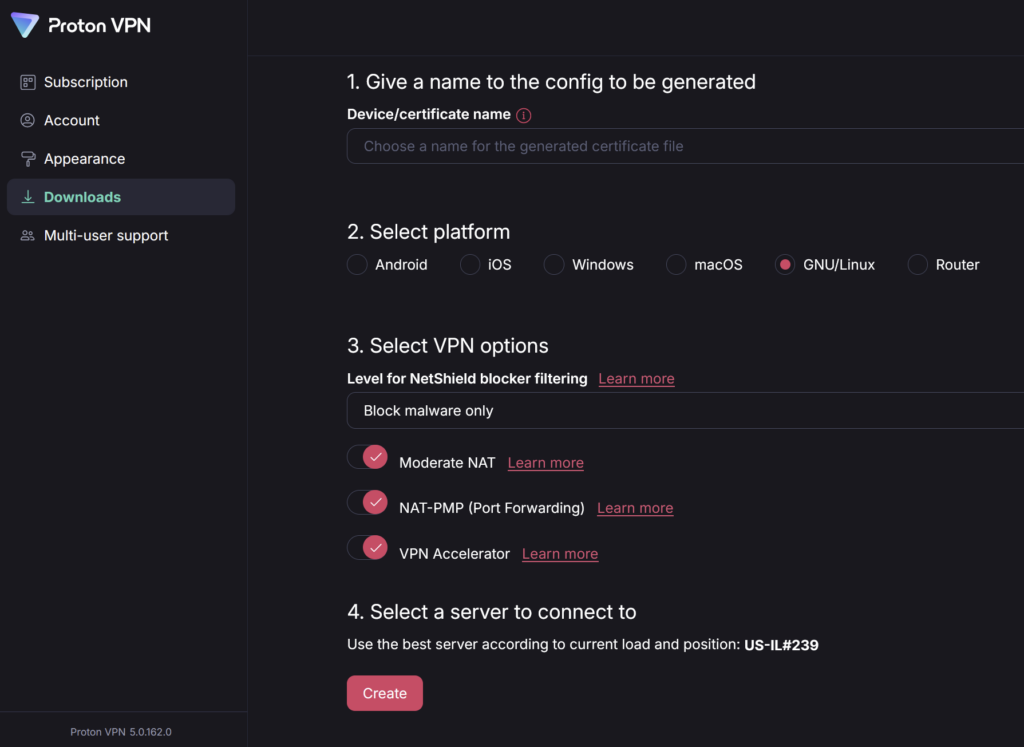
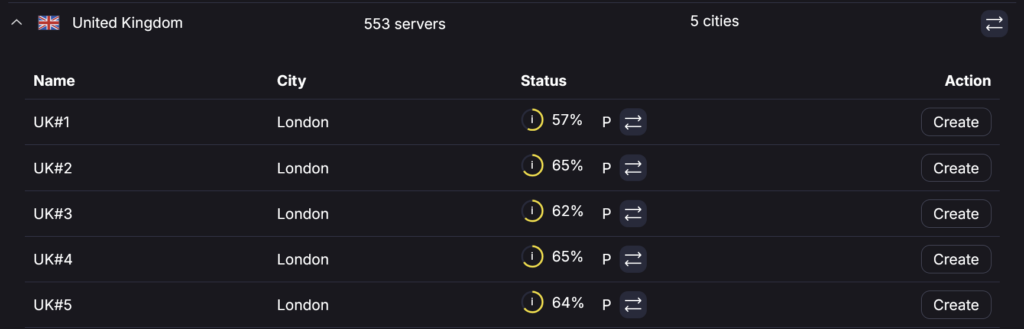
services:
gluetun:
image: qmcgaw/gluetun:latest
container_name: gluetun
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 8090:8090 # qBittorrent
volumes:
- /volume1/docker/gluetun:/gluetun
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- VPN_SERVICE_PROVIDER=protonvpn
- VPN_TYPE=wireguard
- WIREGUARD_PRIVATE_KEY= #Your Key
- SERVER_COUNTRIES= #Your Choice
- PORT_FORWARD_ONLY=on
- VPN_PORT_FORWARDING=on
- DOT_PROVIDERS=quad9
- VPN_PORT_FORWARDING_UP_COMMAND=/bin/sh -c 'wget -O- --retry-connrefused --post-data "json={\"listen_port\":{{PORTS}}}" http://172.20.0.1:8090/api/v2/app/setPreferences 2>&1'
- HTTPPROXY=off
- SHADOWSOCKS=off
- FIREWALL_OUTBOUND_SUBNETS=172.20.0.0/16,192.168.4.0/24
- UPDATER_PERIOD=24h
network_mode: synobridge
labels:
- com.centurylinklabs.watchtower.enable=false
security_opt:
- no-new-privileges:true
restart: always
qbittorrent:
image: linuxserver/qbittorrent:latest
container_name: qbittorrent
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- WEBUI_PORT=8090
- UMASK=022
volumes:
- /volume1/docker/qbittorrent:/config
- /volume1/data/torrents:/data/torrents
network_mode: service:gluetun # run on the vpn network
security_opt:
- no-new-privileges:true
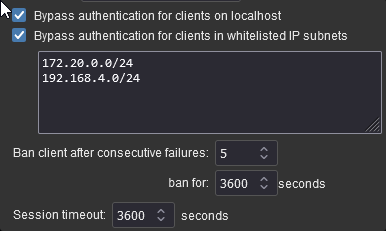
restart: alwaysOnce you have qBittorrent up and running you will need to add a couple of exceptions to its authentication settings to allow the command in the GlueTUN container to update the Listening port for you automatically.
As per the screenshot add an exception for our synobridge Docker Bridge. and also you may require for your local subnet. These are the same IPs you entered into the Firewall Outbound Subnets section of the compose (you do this shortly)
N0rdVPN OpenVPN Preset
The #1 advertiser for VPNs – If you are still within your cooling off period I would recommend getting a refund and use a VPN provider who offers port forwarding such as AirVPN or ProtonVPN. If you are stuck with them you will have limited connectivity and will not be able to use private trackers.
You need to create Service Credentials for the Username and Password elements on the compose from within your Account.
services:
gluetun:
image: qmcgaw/gluetun
container_name: gluetun
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 8090:8090 # qBittorrent
volumes:
- /volume1/docker/gluetun:/gluetun
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- VPN_SERVICE_PROVIDER=nordvpn
- OPENVPN_USER= #User and Pass are Service Credentials in your Nord account
- OPENVPN_PASSWORD=
- TZ=
- HTTPPROXY=off #change to on if you wish to enable
- SHADOWSOCKS=off #change to on if you wish to enable
- FIREWALL_OUTBOUND_SUBNETS=172.20.0.0/16,192.168.XX.XX/24 #change this in line with your subnet see note on guide.
network_mode: synobridge
labels:
- com.centurylinklabs.watchtower.enable=false
restart: unless-stopped
qbittorrent:
image: linuxserver/qbittorrent:latest
container_name: qbittorrent
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- WEBUI_PORT=8090
- UMASK=022
volumes:
- /volume1/docker/qbittorrent:/config
- /volume1/data/torrents:/data/torrents
network_mode: service:gluetun # run on the vpn network
security_opt:
- no-new-privileges:true
restart: always
Docker Compose General Edits
IDs and Timezone
First look for the lines below, they appear twice each, these control the containers access to our filesystem and also the user the containers run as.
| Variable | Value |
|---|---|
| PUID | (required) The UID you obtained in the user setup guide |
| PGID | (required) The GID you obtained in the user setup guide |
| TZ | (required) Your timezone wikipedia.org/wiki/List_of_tz_database_time_zones |
Ports and Proxies
In the top Gluetun section you will notice that we have some additional ports assigned for a http proxy and Shadowsocks Proxy – this means you can direct traffic from other devices or applications on your network through the container! If you want to use these change the following.
| Variable | Value |
|---|---|
| HTTPPROXY | off (default) on (enabled) |
| SHADOWSOCKS | off (default) on (enabled) |
Firewall Outbound Subnet
This section controls your ability to access the UIs of any containers running through the GlueTUN containers network.
- FIREWALL_OUTBOUND_SUBNETS=172.20.0.0/16,192.168.0.0/24The first part ‘172.20.0.0/16’ don’t edit as this is our ‘synobridge’ network and allows other containers such as Radarr to access the download client.
We need to change the second IP after the comma this allows us to access the WebUI and containers via out local network.
This IP address (subnet) is easy to figure out. If you NAS IP is 192.168.0.27 your subnet is 192.168.0.0/24 (notice I just changed the last number before the /24 to 0)
Firewall Input Ports (Port Forwarding)
This line is #commented out by default, if your VPN provider offers port forwarding remove the # from the start of the line and change the port number(s) in line with the ones provided to you. Make sure you also manually update the ‘Listening Port’ in qbit once you are running.
- FIREWALL_VPN_INPUT_PORTS=12345,56789Volumes
By default, I have assumed you have your config files stored on /volume1 if these are located on another volume amend these lines accordingly.
- /volume1/docker/gluetun:/gluetun
- /volume1/docker/qbittorrent:/config
- /volume1/data/torrents:/data/torrents Watchtower Exclusion
You don’t need to change this, I added a label to avoid Watchtower automatically updating the GlueTUN container as it will always break the overall project which can be inconvenient if you are not around to fix it. You can update the container using the mini guide on the left menu of the site.
labels:
- com.centurylinklabs.watchtower.enable=falseDocker Compose – Provider Specific Edits
This next bit is important and if you don’t pay attention to the details you will have a harder time connecting up to your VPN provider, if you used the pre-configured settings for AirVPN or ProtonVPN skip this section.
Open up the GlueTun Wiki and in the list find your provider.
Let’s use AirVPN as our example.
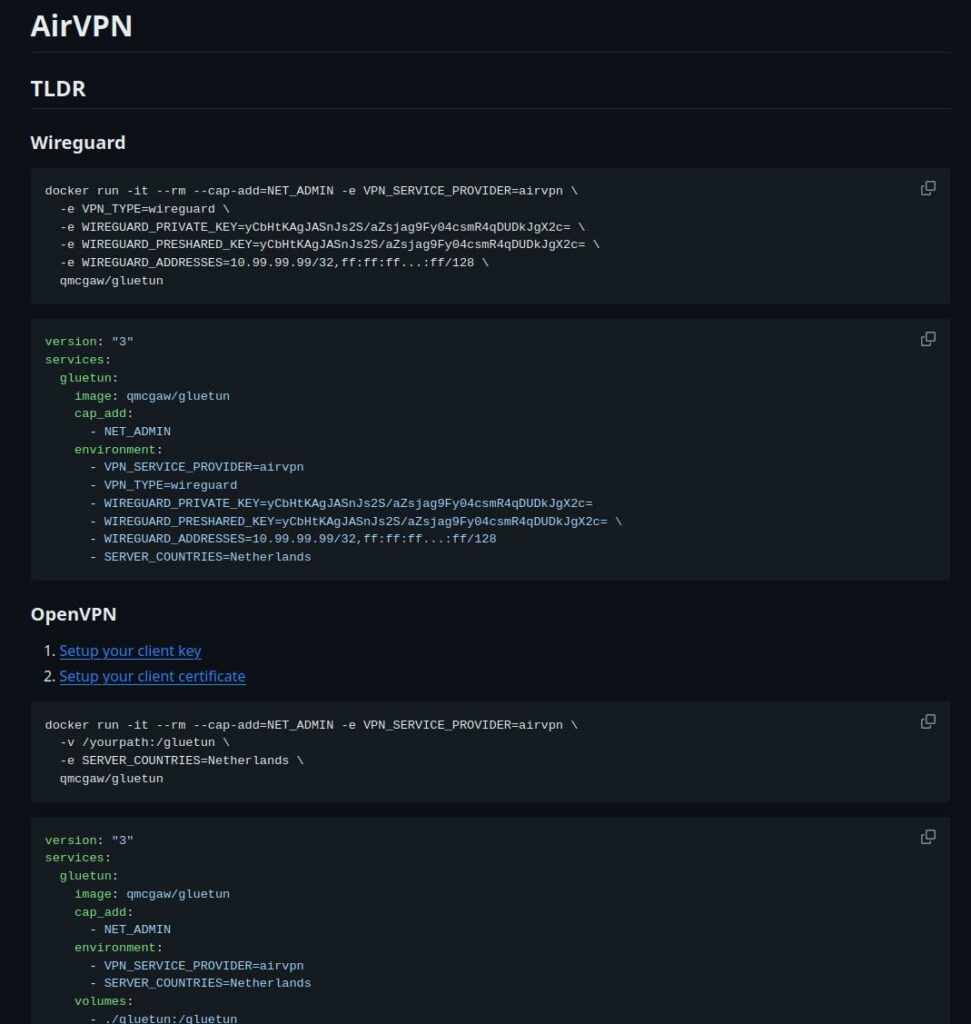
On the page you will see a number of key sections highlighting the variables that work with AirVPN.
Note ignore the ‘docker run’ code it’s not relevant for what we are doing.
Read the compose section and make note of what is shown for either WireGuard or OpenVPN dependent on what you are using to connect and then make the same amendments to the compose you copied earlier.
Key differences are generally the SERVER_COUNTRIES / SERVER_CITIES or what keys are required and IP addresses etc.
I have provided some common defaults in the compose for you, but you need to amend them in line with your providers page.
If your provider is not supported, you can make a request on GitHub to add it, or you can follow the custom providers guidance on GlueTUNs WIKI.
Once you have checked for your provider, make the appropriate edits to the compose accordingly.
That completes the edits to the compose!
Click ‘Next’
You do not need to enable anything on the ‘Web portal settings’ screen click ‘Next’ again
On the final screen click Done which will begin the download of the container images and once downloaded they will be launched!
The images will now be downloaded and extracted. You should see ‘Code 0’ when it has finished.
You will now see your vpn-project running both containers should have a green status on the left-hand side.
Firewall Exceptions
(Skip if you don’t have the Firewall configured)
If you have the Synology Firewall enabled please see this additional guide for further info on exceptions and correct set up.
Final qBittorrent Setup
Changing the default WebUI login and password
If you skip this step you won’t be able to log in.
Now the container has started open it in the Docker UI and go to the Log tab. Within the logs you will see the login details
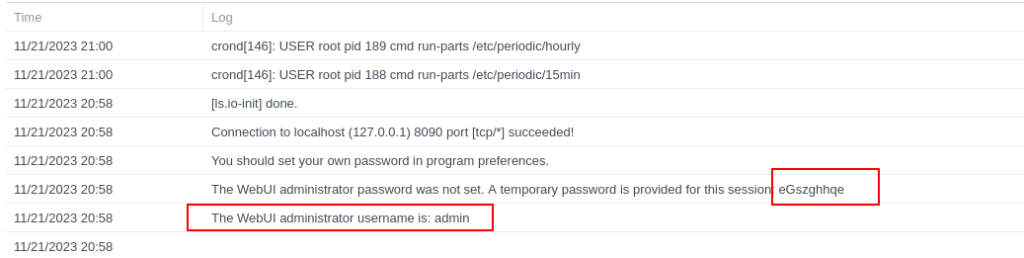
Now before doing any more of the guide go to the Web UI by going to the IP of your NAS followed by port 8090 and log in. Then on the WebUI tab change the defaults to your own and save them.
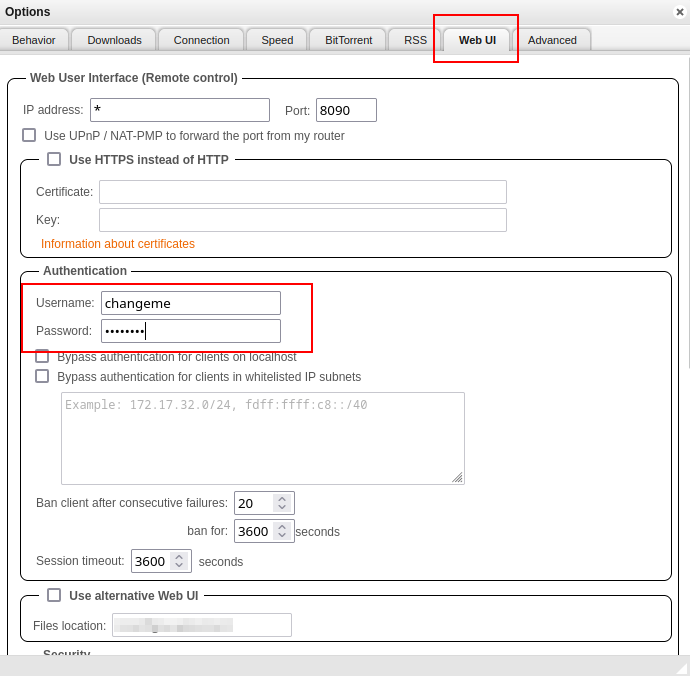
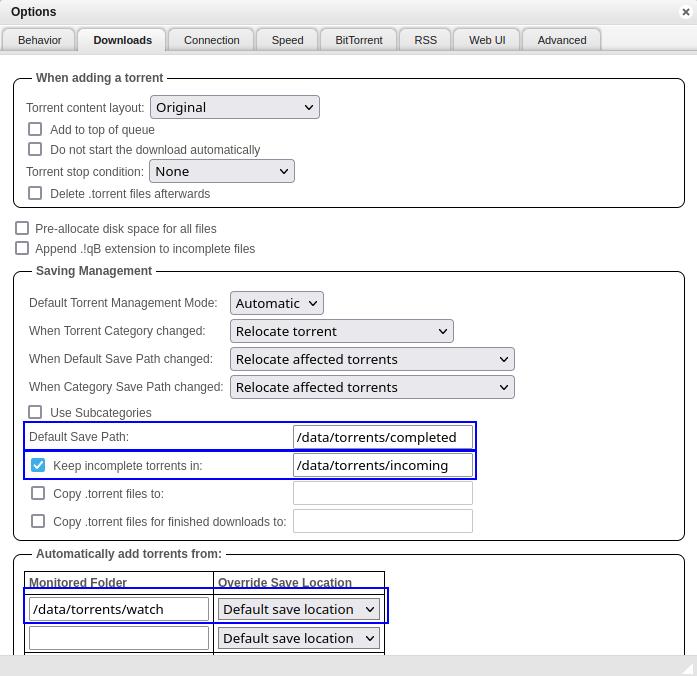
As we have used /data/torrents as the mount point for our downloads we need to make sure qBittorrent uses this same file path. Open the settings and edit the following paths and save.
| Option | Original Value | New Value |
|---|---|---|
| Default Save Path | /downloads | /data/torrents/completed |
| Keep incomplete torrents in | /downloads/incomplete | /data/torrents/incoming |
| Monitored Folder (optional) | blank | /data/torrents/watch |
In prior versions of this guide I had a command to unzip RAR and ZIP files, I have removed this as it is not reliable, check out Unpackerr from the menu.
Advanced Network Settings (Use the TUN Device)
The last step is to tell qBittorrent to only use the tun0 interface for its traffic, go to the Advanced tab then from the ‘Network Interfaces’ drop down select ‘tun0’ and click Apply, If this doesn’t appear the first time you may need to completely reboot your NAS.
I am not going to walk through all the other settings as you can customise these as you wish.
That’s it you are completely set up, you can now start up the Project again from the ‘Project’ tab.
I recommend having a quick read through the FAQ as it covers some questions you may have!
WARNING!
Do not port forward or set up a reverse proxy for qBittorrents WebUI so it directly faces the internet - we have seen 5 or 6 people with compromised instances running Crypto mining. Always use something like Tailscale or a direct WireGuard or OpenVPN connection into your network.
FAQs
Q: My GlueTUN is unhealthy what can I do?
A: The GlueTUN logs should be your first point of call, they will tell you if you have key issues with the configuration that are sometimes easily remedied. If you are still stuck leave a comment on this post, include the contents of your compose and also the log file (Use my PrivateBin https://paste.drfrankenstein.co.uk) remove passwords or WireGuard keys!
Or Join Discord for some more immediate help..
Q: How can I update the GlueTUN containers?
A: See the Updating Containers section on the menu.
Q: How can I be sure the VPN connection is working?
A: Go to the TorGuard Check My Torrent IP site, right-click on the Green banner and copy the link (it’s a Magnet link) Then add this link into qBittorrent and start the torrent. Keeping the site open after a few seconds the site will show the IP address of the connection it finds. This will be of the VPN provider not your home IP. (Please note the torrent doesn’t actually download anything it’s purely doing an IP check)
Q: I am getting the ‘errored’ status for all my torrents
This is very likely a permissions issue, go to the User and Group guide and see the permission fixes towards the bottom.
Q: Everything seems to be connected but nothing is downloading.
Try grabbing the Ubuntu torrent as that is a sure fire way of testing as generally it has over 3k seeds.
Are you using TorGuard – If so they block torrents on their US servers. Change to another country – Also while you are at it, you may need to configure port forwarding in your TorGuard account.
Q: My container doesn’t seem to start on a reboot even with the TUN script.
A: I have seen this a few times and usually relates to the VPN not completing its connection fast enough before containers using the VPN start. You can try setting an additional startup script by doing the following.
Head into Control Panel and go to Task Scheduler Click Create > Triggered Task > User Defined Task
| Section | Setting |
|---|---|
| Task Name | DockerVPNBootUp |
| User | Root |
| Event | Boot Up |
| Pre Task | Select the VPNTUN script from the drop-down that you created at the start of the guide |
In the ‘Task Settings’ tab enter the following and then click Save
sleep 120
docker-compose -p vpn-project -f /volume1/docker/projects/vpnproject-compose/compose.yaml down
wait
docker-compose -p vpn-project -f /volume1/docker/projects/vpnproject-compose/compose.yaml up -d(thanks gtavo in the commands for the improvement!)
Once added Save and Container Manager will rebuild the project with the mod enabled, you will see it working in the qBittorrent containers log.
Q: I tried to start Deluge / qBittorrent manually, and it says ‘Container must join at least one network’
A: This is due to the Synology Container Manager GUI not understanding that the container will be on the GlueTUN ‘network’. You will need to start the container via the Project as it is part of the overall Project compose.
Q: How can I add additional services to the VPN container?
See some of my other GlueTUN related guides as they show the steps required to add other containers to GlueTUN
Looking for some help, join our Discord community
If you are struggling with any steps in the guides or looking to branch out into other containers join our Discord community!
Buy me a beverage!
If you have found my site useful please consider pinging me a tip as it helps cover the cost of running things or just lets me stay hydrated. Plus 10% goes to the devs of the apps I do guides for every year.





Getting this error when trying to find the login info within the abittorrent log file:
“Could not create a required directory ‘/config/.cache/qBittorrent'”
I searched and found this:
https://discourse.linuxserver.io/t/log-error-could-not-create-required-directory-config-cache-qbittorrent/1953/5
Should I give more permissions to the dockergroup group?
On a separate note, do you have a recommended tutorial for setting up proper security on the synology? I want to use the “Firewall enabled” settings from your tutorials, but also want to properly configure the firewall and such to protect my NAS from attacks.
Thank you, sir.
On the first part double check your PGID and PUID values are correct. If they are then try deleting the /docker/qbittorrent folder and create it again in File station. You can even right click on it and change the owner to dockerlimited.
From a Firewall perspective I don’t have a guide personally however Wundertech has a nice one. https://www.wundertech.net/how-to-set-up-the-firewall-on-a-synology-nas/ rather than watch the video follow the steps in the guide.
-PGID and PUID are verified correct – gluetun is running and connected to PIA vpn (displays public IP in log) using the same IDs
-I deleted the “/docker/qbittorrent/” folder. Recreated it. Checked properties and had my username as the owner. Restarted the vpn-project and same error. However, after this run, verified it is changing the Owner of /docker/qbittorrent/” to dockerlimited. Also creating and subfolder and writing a config file: “/docker/qbittorrent/qBittorrent/qBittorrent.conf” file is created.
Within the log file and many lines for “Could not create a required directory ‘/config/.cache/qBittorrent’” is also the line:
“crond[168]: USER root pid 9296 cmd run-parts /etc/periodic/15min”
OK can you SSH into your NAS and run the following please this should fix the permission issue.
This assumes your docker share is on volume1, and you followed the user creation guide, if not please let me know, and I will email you directly.
Run these one at a time, you will see no output then try starting up the Project and qbit should be OK permission wise.
sudo chown -R dockerlimited:dockergroup /volume1/docker/qbittorrent
sudo chmod -R a=,a+rX,u+w,g+w /volume1/docker/qbittorrent
That worked! I have my temporary password now and can continue the guide. Thank you for these guides and your support.
Will I need to run the manual chown and chmod for every install if I get permission errors? Like plex for example:
2023/11/26 12:49:47 stderr /etc/s6-overlay/s6-rc.d/init-plex-claim/run: line 63: 136 Aborted (core dumped) s6-setuidgid abc /bin/bash -c ‘LD_LIBRARY_PATH=/usr/lib/plexmediaserver:/usr/lib/plexmediaserver/lib /usr/lib/plexmediaserver/Plex\ Media\ Server’
2023/11/26 12:49:45 stderr libc++abi: terminating with uncaught exception of type boost::filesystem::filesystem_error: boost::filesystem::create_directories: Permission denied [system:13]: “/config/Library/Application Support/Plex Media Server/Cache”, “/config/Library/Application Support/Plex Media Server/Cache”
It looks like the permissions for all your folders have not taken, do this it will fix the whole data and docker shares.
sudo chown -R dockerlimited:dockergroup /volume1/docker /volume1/data
sudo chmod -R a=,a+rX,u+w,g+w /volume1/docker /volume1/data
Hey Doc,
I have been using your scripts for months and they have worked flawlessly! Last night qBittorrent updated to 4.6.1 and for some reason the default password was changed. Since all the arrs used the default password, my local IP was getting autobanned. I shutdown the arrs dockers and tried to troubleshoot the password issue.
Occassionally the logs for the docker would say something along the lines “No default password use the following: *8AqnAj* (something random). But that password never worked. I checked the qbittorrent.conf and there is no a “webui/Password=” input. I have not seen this documented on qBittorrent github. Let me know if you are having a similar issue.
I have since reverted back to version 4.6.0 and it works flawlessly.
Hey – just discussing this on Discord – this is a qbittorrent update that auto revokes the old default password for security – which is a good thing. You will need to check the logs for qbittorent for your new password – I will be updating the guides shortly.
Thanks for the update! Just checked the open tickets on qBittorrent github and it looks like there is an open ticket for this issue:
Foreground depends on a tty, results in no session password being logged
https://github.com/qbittorrent/qBittorrent/issues/19984
Hopefully it gets resolved soon!
Perfect – guide update incoming…
Hi – the problem I have is the temporary password doesn’t show in the logs until I stop the qbittorent container and then it’s logged. This doesn’t help me because when I start up the container again there’s a new temporary password. Not sure how to see it while the container is running.
I have updated the guide. There is now a tty line in the yaml which triggers the password on start up.
hi, after recent update of qbittorrent i’m getting error: unable to bind to Ip and can’t access to webui, i’ve deleted containers and recreated project but getting the same error.
It may be Container Manager holding onto the Port try doing a reboot.
It didn’t help, it’s like if qbittorent isn’t part of any networks, or it isn’t supposed to be?
can I see your compose / yaml please
paste.drfrankenstein.co.uk and then paste the url here. Make sure you remove login details for your VPN everything else can stay
I’m having trouble with the two containers in vpn-project.
The gluetun container displays a warning: “[healthcheck] program has been unhealthy for 51s: restarting VPN (see https://github.com/qdm12/gluetun-wiki/blob/main/faq/healthcheck.md)”
And the qbittorrent container displays a popup: “Container must join at least one network.” I’ll note that the Network section of the General tab is mostly blank.
In case it helps, I also note that I have two connected Network interfaces: LAN 4 and VPN – ExpressVPN.
Hey, so first off, check the log of Gluetun it should tell you why the connection is unhealthy, so check that bit first. The qbit container will throw that error as it has to be started as part of the overall project as it relies on the network connection of the Gluetun container so it’s Network tab will be empty.
Hi, thanks for the starting point. It seems to me like I was using the wrong credentials for OpenVPN, so I got those from my VPN provider (ExpressVPN) account. Updating those credentials still gives me an error. Should I be doing referencing a .ovpn file? The pertinent parts of the log:
Your credentials might be wrong
ERROR [openvpn] AUTH: Received control message: AUTH_FAILED
INFO [openvpn] [Server-2674-1a] Peer Connection Initiated with [AF_INET]85.203.45.8:1195
WARN [openvpn] ‘comp-lzo’ is present in remote config but missing in local config, remote=’comp-lzo’
WARN [openvpn] ‘auth’ is used inconsistently, local=’auth [null-digest]’, remote=’auth SHA512′
WARN [openvpn] ‘link-mtu’ is used inconsistently, local=’link-mtu 1553′, remote=’link-mtu 1606′
INFO [openvpn] UDP link remote: [AF_INET]85.203.45.8:1195
INFO [openvpn] UDP link local: (not bound)
INFO [openvpn] TCP/UDP: Preserving recently used remote address: [AF_INET]85.203.45.8:1195
Thanks for your help!
If you are still receiving AUTH_FAILED the connection is taking place and ExpressVPN are rejecting either the username or password. The other warnings can be safely ignored. Can I see your yaml please remove the auth details as it could be something incorrectly formatted.
paste.drfrankenstein.co.uk and then paste the url here.
I got the Gluetun container running after fixing the vpn creds. But the qbittorrent is still failing with the same error as before: “Container must join at least one network.”
The yaml is here
https://paste.drfrankenstein.co.uk/?b70456bc63e53824#Gi3seFg1gdQndy5346m8gv1hHVAMjixwCKmgf4sMJsE8
Don’t try to start Qbit separate from the overall project. The container manager UI doesn’t understand that it is connected though GlueTUN. You have to go into the Project and click Action > Build
Thanks! That was the problem. I was able to get through the rest of your guide without a hitch and test it successfully.
Much gratitude, Doctor!
So I updated my qBittorrent container yesterday and now when I boot the project up qBittorrent boots but I get the error “Web UI: Unable to bind to IP: localhost, port: 8090. Reason: Unsupported socket operation”.
It has been working fine for the past 2 weeks.
Help please 🙂
Try stopping the whole project and using Action Build again see if that then works.
I don’t know if the update messed with the configuration files.
I ended up deleting all the files in the qBittorrent docker folder and rebuilding the project which did the trick.
Thanks for the help :).
OK sometimes strange things happen.
Glad it’s working again