Last updated on 6 April 2025
Please note if you are using DSM7.2 or higher you should use the Container Manager version of this guide from the menu.
If you are still using an older DSM version migrate to Dockge and you can use my new guides!
See the Dockge guide here to start migration!
This guide has reached the end of its updates
Important or Recent Updates
| Historic Updates | Date |
|---|---|
| New guide | 23/09/2022 |
| Fixed a typo in the yaml ‘vpngluetun’ to ‘gluetun’ | 26/09/2022 |
| Added the synobridge network to the VPN container | 07/10/2022 |
| Added depends_on to the compose file to help with the container stack coming online at boot. | 18/10/2022 |
| Removed requirement to use VPN Package | 06/11/2022 |
| Amended compose file for enabling or disabling the built-in proxy | 09/12/2022 |
| Added note to the FAQ about how to Update the containers | 06/01/2023 |
| Added additional step to force Deluge to use the tun0 interface | 06/02/2023 |
| Added firewall exception for network subnet | 22/02/2023 |
| Added firewall exception for ‘synobridge’ subnet as this seems to be yet another random thing that works for some and not others! | 31/03/2023 |
| Compose version number removed and image updated in line with amendment | 09/04/2023 |
| Amended the path to save the compose file – this is for security, so the container has no access to the file contents. | 14/04/2023 |
| Added watchtower labels to the compose to allow updates and changed the proxies to off by default | 06/05/2023 |
| Removed the Watchtower ‘Depends On’ Labels as they do not successfully update the GlueTUN container. Added an Exclusion label to the GlueTUN container, so it can just be manually updated. | 11/05/2023 |
| Update includes: Firewall Input Ports for when your provider offers port forwarding, also a note in relation to volumes and added PUID/PGID settings for GlueTUN | 14/06/2023 |
| Update for Wireguard Kernel Module Install which reduces overall CPU usage for Wireguard connections Please note if you previously followed this guide you can follow the new section to update your existing set-up. Added Health checks to dependent containers | 25/09/2023 |
What are Deluge and GlueTUN?
Deluge is a lightweight torrent downloader, it has a number of built-in plugins to help organise your downloads and a full web interface, GlueTUN is the Docker container that has pre-configured VPN connections for numerous VPN providers.
Before you start check the GlueTUN Wiki to see if your provider is on the supported list on the left-hand side.
Also, if you are yet to choose a provider have a look at the Reddit list of recommended suppliers as could save you a headache when trying to seed. I currently use AirVPN which has nice easy port forwarding unlike some others. This is my affiliate link if you fancy signing up.
Let’s Begin
In this guide I will take you through the steps to get Deluge up and running in Docker and a separate GlueTUN VPN container. By having a separate container for the VPN connection we can use it in the future for other applications such as Prowlarr, this is useful if you have torrent indexers blocked in your country.
As the Synology DSM GUI does not support some of the functions we need for this tutorial we will be using Docker Compose. This is not as complicated as it might seem!
In order for you to successfully use this guide please complete the three preceding guides
- Step 1: Directory Setup Guide
- Step 2: Setting up a restricted Docker user
- Step 3: Setting up a Docker Bridge Network
Folder Setup
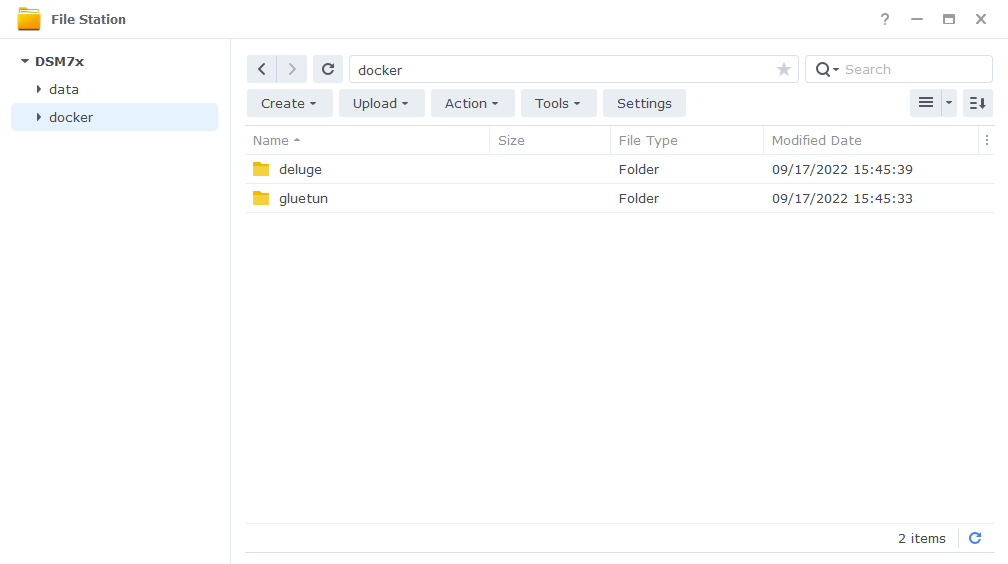
Let’s start by getting a couple of folders set up for the containers to use. Open up Filestation and within the /docker share create a folder called ‘deluge’ and one called ‘gluetun’
Setting up the start up script
Open up Control Panel and then click on Task Scheduler
Next click on Create, Triggered Task then User Defined Script.
Now enter a name for the script – you can call it anything you like. The User must be ‘root’ and ‘Boot-up’ for the Event.
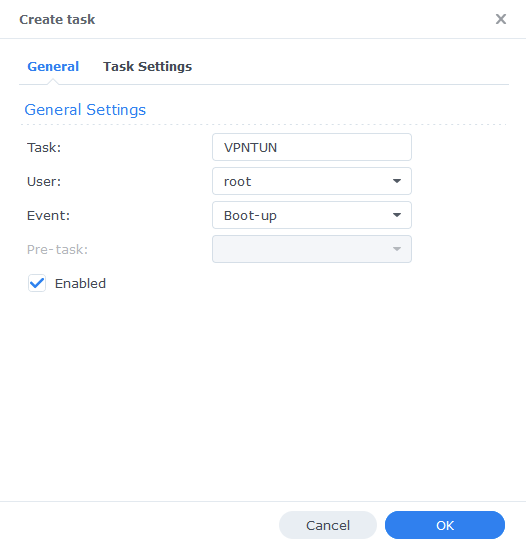
On the Task Settings tab copy and paste the code below in the ‘User-Defined script’ section. It will look like screenshot.
#!/bin/sh -e
insmod /lib/modules/tun.ko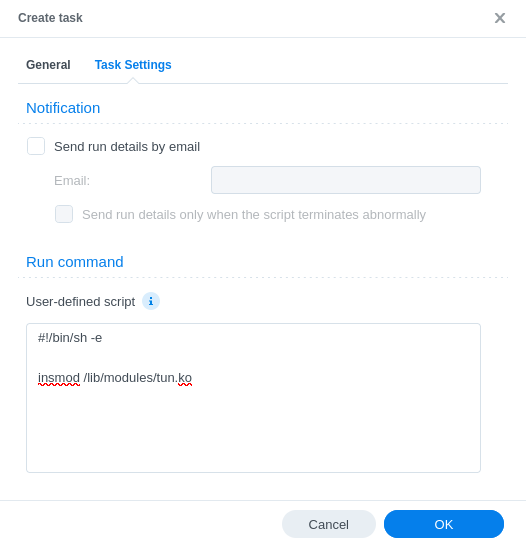
You can now press OK and agree to the warning message. Next run the script which will enable the TUN device.
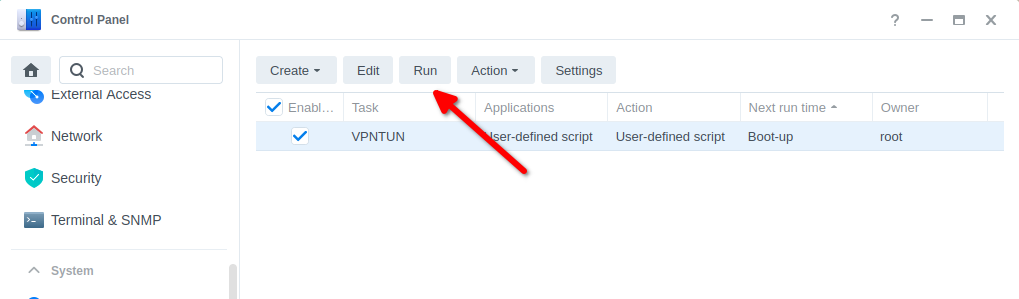
You can now move on to the next step.
Wireguard Kernel Module
(Recommended for Performance & Reduced CPU Resource)
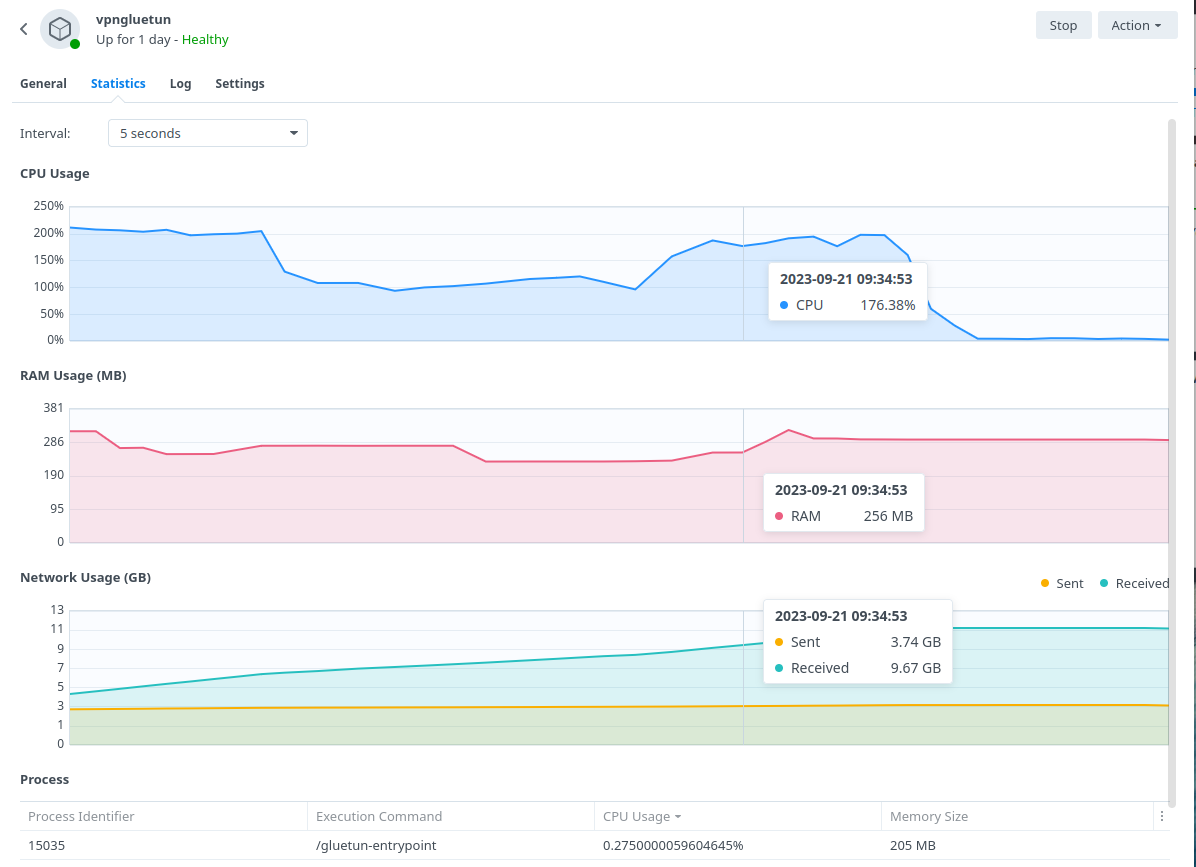
The default Gluetun Wireguard setup uses a ‘Userspace’ implementation of Wireguard which normally should not use much from a CPU resource perspective. However, on Synology it tends to require high CPU utilisation. For example a 40MiB download via qBittorrent uses up to 176% in CPU (1.7 Cores) on my 1821+.
By installing the appropriate Kernel Module this reduces down to 1 or 2% which over time would add up from an electric usage perspective and free up the CPU for other tasks.
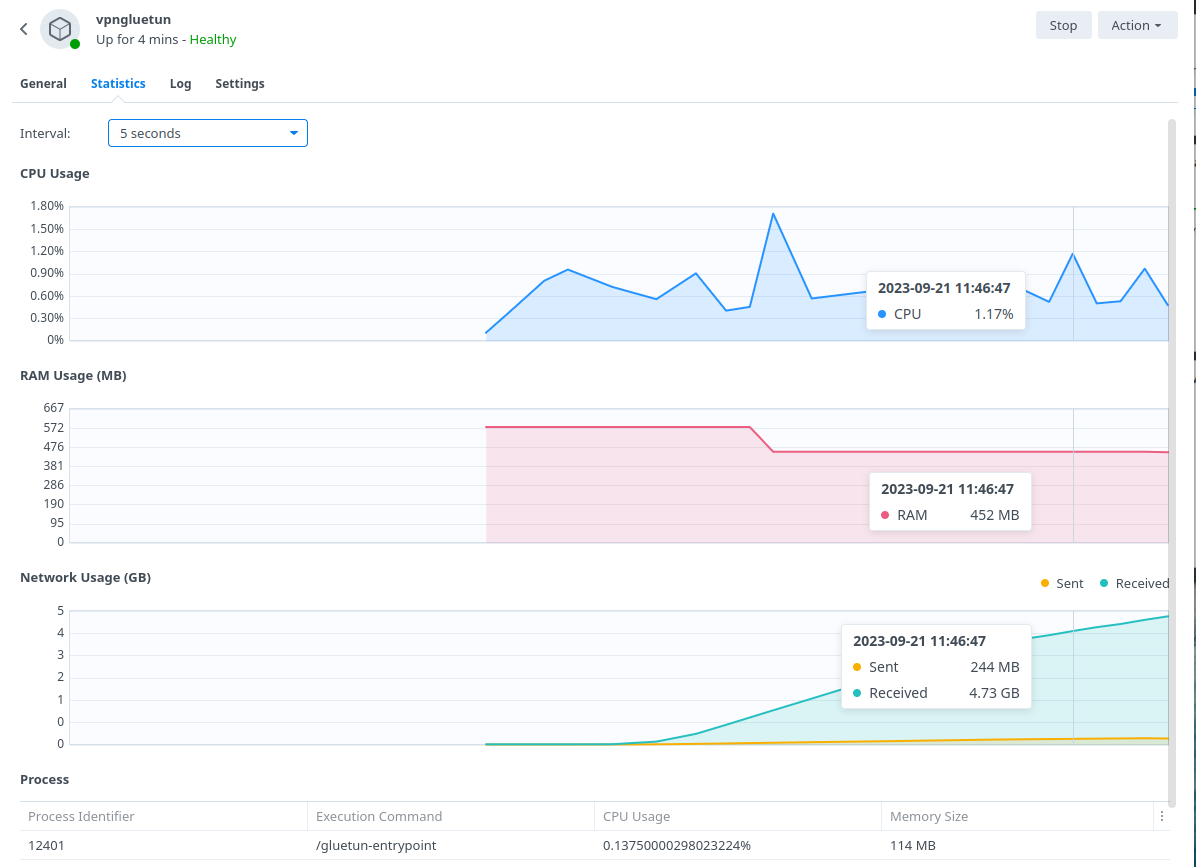
BlackVoid.club have put together a Kernel Module for Synology which allows Gluetun to use the lower level Kernel to perform Wireguard duties make sure you drop them a thanks as this would not be possible without them!
While on first glances it looks like a long installation process the page details a number of methods. I recommend having a read taking note of warnings and also if you want to build your own model it tells you how.
The TLDR is below.
Step 1 – Find your model of NAS under the correct DSM version section (If you are following this guide it will be 7.0/1) and download the pre compiled .spk file
Step 2 – Head into Package Manager and click ‘Manual Install’ on the top right and install the .spk file and untick the box to run after install
Step 3 – Reboot (Not always required for DSM7.1 and lower)
Step 4 – SSH Into your NAS (Just like in the User Setup guide) and elevate yourself to root by typing sudo -i and entering your password
Step 5 – Enter this command and press enter to start up the module /var/packages/WireGuard/scripts/start
You should now be able to see the WireGuard package running in Package Manager. Please note while I will try my best to support in relation to this module I may have to refer you on if it is a specific technical issue.
When you have GlueTUN running check the log for this line [wireguard] Using available kernelspace implementation, and you know it is working.
On to the next part.
Firewall (Optional Step if you have the Firewall Enabled)
If you have the Synology Firewall enabled and configured to block outgoing connections you will need to do this step. Otherwise, you will have issues with the VPN connecting to your provider. (please note the screenshot below does not show all the other rules you would normally have enabled)
Go into Control Panel > Security > Firewall
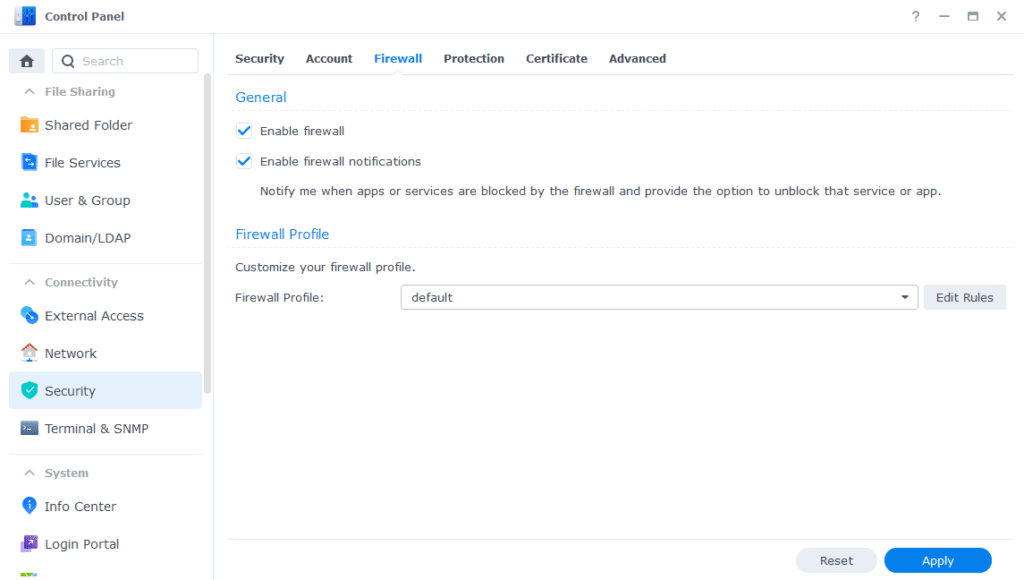
Click on Edit Rules and in the screen that appears click on ‘Create’
In the first screen select ‘Custom’
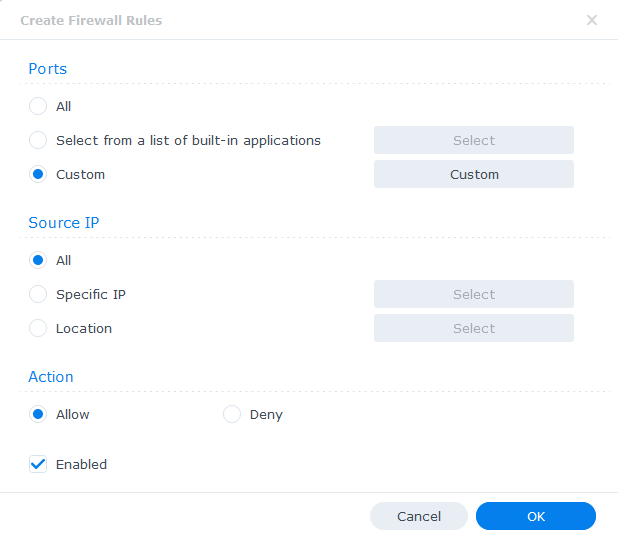
On the next screen we select the Type as ‘Destination Port’ and Protocol as ‘All’. In this example I am going to open up both 1194 and 1195 as some providers use UDP and some TCP and these are the most commonly used ports.
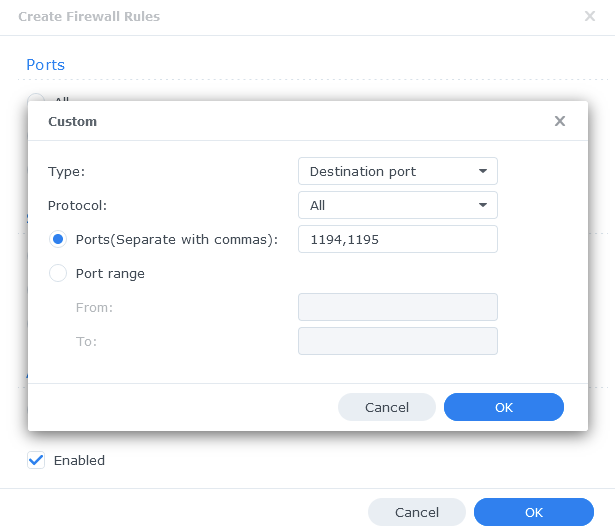
Click on OK and Apply the rule, and leave the ‘Source IP’ and ‘Action’ to their defaults on the original screen.
Docker Compose
Next we are going to create a Docker Compose file, this is used to tell Docker how to set up our container with all the variables we require that are not available in the DSM GUI.
You can edit this file in a number of ways, but to keep the guide OS-agnostic we will be using the Synology Text Editor package which can be installed via Package Center.
Open up Text Editor and create a new file, then copy and paste the information below into the file.
services:
gluetun:
image: qmcgaw/gluetun:latest
container_name: gluetun
cap_add:
- NET_ADMIN
devices:
- /dev/net/tun:/dev/net/tun
ports:
- 8888:8888/tcp # HTTP proxy
- 8388:8388/tcp # Shadowsocks
- 8388:8388/udp # Shadowsocks
- 8112:8112 # port for deluge
volumes:
- /volume1/docker/gluetun:/gluetun
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- VPN_SERVICE_PROVIDER=NAMEOFYOURPROVIDER
- VPN_TYPE=openvpn
- OPENVPN_USER=VPNUSERNAME
- OPENVPN_PASSWORD=VPNPASSWORD
- SERVER_COUNTRIES=VPNSERVERCOUNTRY
- HTTPPROXY=off #change to on if you wish to enable
- SHADOWSOCKS=off #change to on if you wish to enable
- FIREWALL_OUTBOUND_SUBNETS=172.20.0.0/16,192.168.0.0/24 #change this in line with your subnet see note on guide.
# - FIREWALL_VPN_INPUT_PORTS=12345 #uncomment this line and change the port as per the note on the guide
network_mode: synobridge
labels:
- com.centurylinklabs.watchtower.enable=false
restart: unless-stopped
linuxserver-deluge:
image: linuxserver/deluge:latest
container_name: deluge
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- DELUGE_LOGLEVEL=error #optional
volumes:
- /volume1/docker/deluge:/config
- /volume1/data/torrents:/data/torrents
network_mode: service:gluetun # run on the vpn network
depends_on:
gluetun:
condition: service_healthy
restart: unless-stoppedYou can change the formatting to YAML in the bottom right of the editor to make it easier to read.
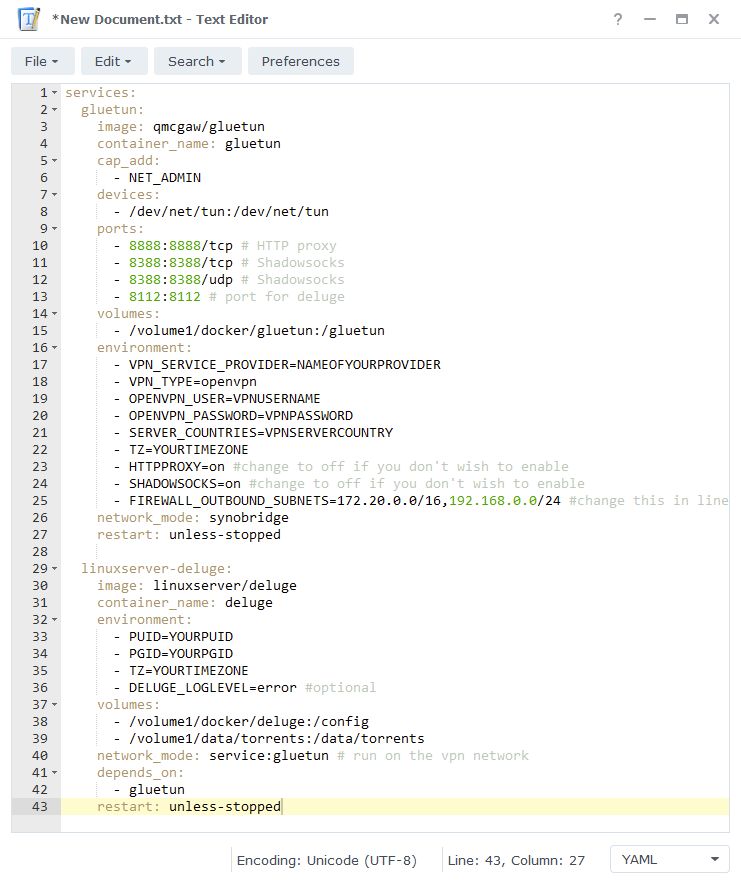
Firewall Subnet
You will see an environment variable in the yml file called FIREWALL_OUTBOUND_SUBNETS=172.20.0.0/16,192.168.0.0/24
The first part 172.20.0.0/16 don’t edit this, the second IP after the , change as per below.
This IP address is easy to figure out. If you NAS IP is 192.168.1.27 your subnet is 192.168.1.0/24 (notice I just changed the last number to 0) This variable allows any containers connected via the VPN access to your local network.
Firewall Input Ports
This part is # commented out by default, if your provider offers port forwarding remove the # from the start of the line and change the port number in line with the one provided to you. This will also be the port used within Deluge and will help overall connectivity. (Note if you are using Proton VPN see the FAQ for an important extra step now!)
Volumes
By default, I have assumed you have your config files stored on /volume1 if these are located on another volume amend this line accordingly.
Watchtower Exclusion
You don’t need to change this, I added a label to avoid Watchtower automatically updating the GlueTUN container as it will always break the overall project which can be inconvenient if you are not around to fix it. You can update the container using the mini guide on the left menu of the site.
labels:
- com.centurylinklabs.watchtower.enable=falseImportant – Provider Specific Edits
Next up we will need to make some edits to the Environment Variables section of the compose in line with what is required for your specific provider. Open up the GlueTun Wiki and in the list find your provider.
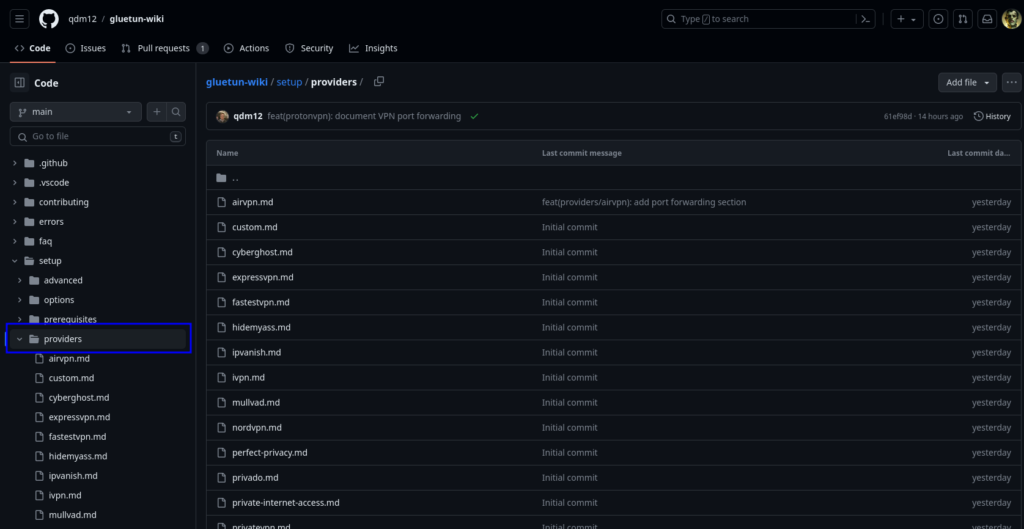
For example in the Privado section (screenshot below) it has the variables required to make a successful connection, The ‘Required environment variables’ section will get you connected to a random server of the containers choosing.
You can add the ‘Optional environment variables’ parameters in order to select a specific server or range of servers. These are found on the same page.
(Pay close attention to your providers amendments as often people are caught out by using the incorrect settings such as SERVER_COUNTRIES when it should be SERVER_REGIONS etc)
If your provider is not supported, you can make a request on GitHub to add it, I do not currently have custom providers covered in this guide, feel free to jump on Discord / email me for help here.
Also note that some providers don’t like you having special characters in the password you will generally spot this in the log with AUTH errors.
This will be very similar across all the providers built in with some slight variances.
Once you have checked for your provider, make the appropriate edits to the compose accordingly.
In addition to the edits we just made there are a couple more in the table below, do these in the sections I have pre-filled
| Variable | Value |
|---|---|
| PUID | (required) The UID you obtained in the user setup guide |
| PGID | (required) The GID you obtained in the user setup guide |
| TZ | (required) Your timezone wikipedia.org/wiki/List_of_tz_database_time_zones |
You can now save this compose file in /docker and call it delugevpn.yml
SSH and Docker-Compose
It’s time to get logged into you Diskstation via SSH, you can do this in the same way as when you obtained your IDs in the ‘Setting up a restricted Docker user‘ guide.
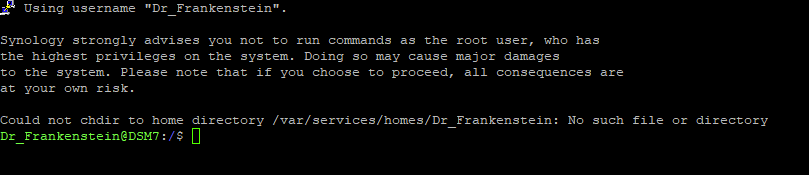
Once you have logged in you will need to give 2 commands, you can copy and paste these one at a time — you will need to enter your password for the command starting with ‘sudo’
First we are going to change directory to where the delugevpn.yml is located, type the below and then press enter.
cd /volume1/dockerThen we are going to instruct Docker Compose to read the file we created and complete the set-up of the container. Again type the below and press enter.
sudo docker-compose -f delugevpn.yml up -dWhen the command has completed you should be able to see both Deluge and the VPN container running in the list of containers in the Synology GUI.
Error: “gluetun is unhealthy”
At this stage if you receive an error relating to GlueTUN being unhealthy there is likely an error in the config file, this usually relates to the provider specific elements. If you check the logs for the GlueTUN container it will tell you why it couldn’t connect. If you get stuck drop me a comment with a copy of the logs via https://paste.drfrankenstein.co.uk.
Final Deluge Setup
As we have used /data/torrents as the mount point for our downloads we need to make sure Deluge uses this same file path.
We are going to do this by just changing the directory settings within Deluge.
Open a new browser tab and go to your NAS IP address on port 8112 (e.g. 192.168.0.46:8112)
Deluge by default has the password of ‘deluge’ to access the web UI, you can change or remove this later in the settings.
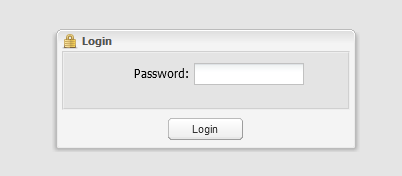
Next you will connect to the Deluge back end, just select the host and click connect, it will remember this going forward.
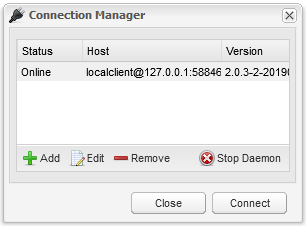
Now you are in the UI click on Preferences at the top of the screen, we are going to change the various folders to the settings shown in the screenshot/table below
| Option | From | To |
|---|---|---|
| Download to: | /root/Downloads | /data/torrents/incoming |
| Move complete to: | /root/Downloads | /data/torrents/completed |
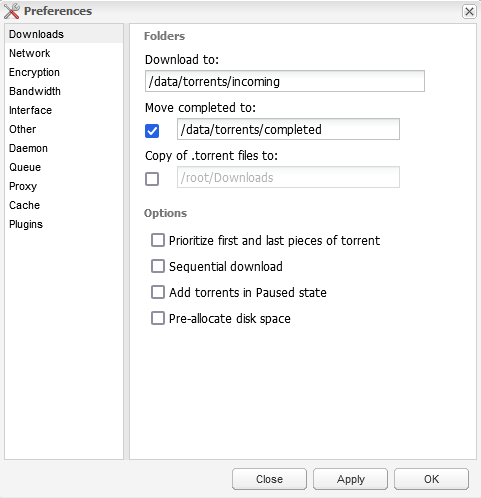
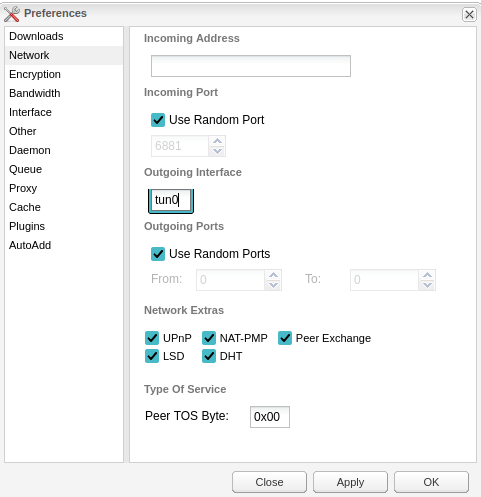
Network
To be sure that Deluge only uses the TUN interface you next need to go to the Network options (second one down) and within the ‘Outgoing Interface’ enter ‘tun0’
Plugins
There are a couple of plugins you will want to enable. (If you are looking for something to unpack torrents that are zipped then follow the Unpackerr guide)
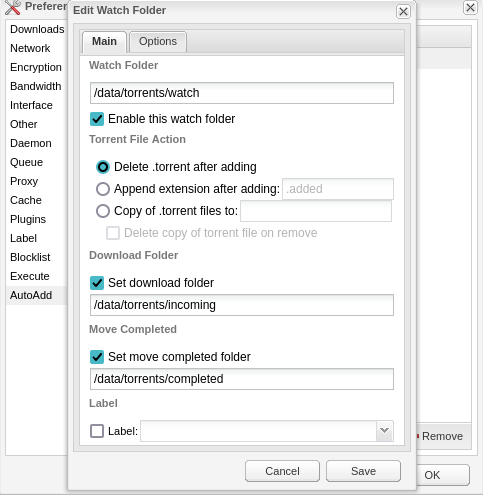
- Autoadd – This allows you to pull in any torrents in the watch directory
- Label – This allows Radarr/Sonarr to assigned labels and pull downloads into subdirectories – no additional configuration required for this plugin
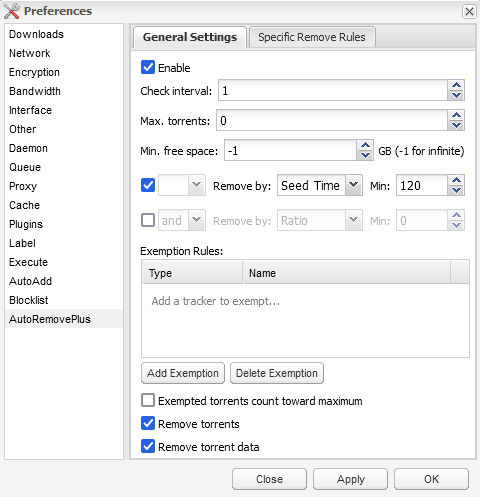
- Auto Remove Plus – Download the ‘AutoRemovePlus-2.0.0-py3.8.egg’ version from the Deluge forums and place it in the Plugins’ folder in /docker/deluge/plugins. It allows you to fine tune when to remove torrents and their associated data once downloaded. (You may need to stop and re-up the container for this to appear)
That’s it you are completely set up! I recommend having a quick read through the FAQ as it covers some questions you may have!
FAQs
Q: How can I update the GlueTUN containers?
A: See the Updating Containers section on the menu for a specific guide for GlueTUN
Q: How can I be sure the VPN connection is working?
A: Go to the TorGuard Check My Torrent IP site, right-click on the Green banner and copy the link (it’s a Magnet link) Then add this link into Deluge and start the torrent. Keeping the site open after a few seconds the site will show the IP address of the connection it finds. This will be of the VPN provider not your home IP. (Please note the torrent doesn’t actually download anything it’s purely doing an IP check)
Q: I tried to start Deluge / qBittorrent manually, and it says ‘Container must join at least one network’
A: This is due to the Synology Docker GUI not understanding that the container will be on the VPNs ‘network’. You will either need to start the container again via SSH or you can set up a manually triggered script via Task Scheduler you will only need to do use this if you ever stop the container.
Head into Control Panel and go to Task Scheduler, Click Create > Triggered Task > User Defined Task
| Section | Setting |
|---|---|
| Task Name | DockerVPNRestart |
| User | Root |
| Enabled | Leave Unticked |
In the ‘Task Settings’ tab enter the following and then click Save
docker-compose -f /volume1/docker/delugevpn.yml down
wait
docker-compose -f /volume1/docker/delugevpn.yml up -dQ: Everything seems to be connected but nothing is downloading.
Are you using TorGuard – If so they block torrents on their US servers. Change to another country – Also while you are at it, you may need to configure port forwarding in your TorGuard account.
Try grabbing the Ubuntu torrent as that is a sure fire way of testing as generally it has over 3k seeds.
Q: My container doesn’t seem to start on a reboot even with the TUN script.
A: I have seen this a few times and usually relates to the VPN not completing its connection fast enough before containers using the VPN start. You can try setting an additional startup script by doing the following.
Head into Control Panel and go to Task Scheduler Click Create > Triggered Task > User Defined Task
| Section | Setting |
|---|---|
| Task Name | DockerVPNBootUp |
| User | Root |
| Event | Boot Up |
| Pre Task | Select the TUN script from the drop-down |
In the ‘Task Settings’ tab enter the following and then click Save
sleep 120
docker-compose -f /volume1/docker/delugevpn.yml down
wait
docker-compose -f /volume1/docker/delugevpn.yml up -dProton VPN Port Forwarding Extra Step
Proton doesn’t allow you to choose your own port for port forwarding, so we need to add another container to the compose in order for this to be automatically updated for us. (Please note I am unable to test this personally it is based on Feedback via our Discord channel)
First don’t uncomment this line in the compose leave it disabled# - FIREWALL_VPN_INPUT_PORTS=40312
Next copy the code below to bottom of the compose file and then amend the following only leave the other options.
TZ= #ENTER YOUR TIMEZONEQBITTORRENT_SERVER= #ENTER YOUR NAS IP QBITTORRENT_USER=admin (change to the username you will be using later for qbit)QBITTORRENT_PASS=adminadmin (change to the password you will be using later for qbit)
Once added continue with the guide 🙂
qbittorrent-natmap:
# https://github.com/soxfor/qbittorrent-natmap
image: ghcr.io/soxfor/qbittorrent-natmap:latest
container_name: qbittorrent-natmap
restart: unless-stopped
volumes:
- /var/run/docker.sock:/var/run/docker.sock:ro
environment:
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
- QBITTORRENT_SERVER=
- QBITTORRENT_PORT=8090
- QBITTORRENT_USER=admin
- QBITTORRENT_PASS=adminadmin
# - VPN_GATEWAY=
# - VPN_CT_NAME=gluetun
# - VPN_IF_NAME=tun0
# - CHECK_INTERVAL=300
# - NAT_LEASE_LIFETIME=300
network_mode: service:gluetun
depends_on:
qbittorrent:
condition: service_started
gluetun:
condition: service_healthyQ: How can I add additional services to the VPN container?
A: Adding additional containers to the VPN network is very easy. As you can see in the example below I have added Prowlarr to the bottom of the compose. The only amendments are that the ‘network_mode’ uses the Gluetun container and the ports for Prowlarr have been moved up to the Gluetun containers ports section.
Also see the separate Prowlarr guide on the left menu for setting up FlareSolver (In the Extras section)
- 9696:9696 # add this to the ports section of GlueTUN
#add the below to the bottom of the compose
linuxserver-prowlarr:
image: linuxserver/prowlarr:latest
container_name: prowlarr
environment:
- PUID=1234 #CHANGE_TO_YOUR_UID
- PGID=65432 #CHANGE_TO_YOUR_GID
- TZ=Europe/London #CHANGE_TO_YOUR_TZ
volumes:
- /volume1/docker/prowlarr:/config
network_mode: service:gluetun # run on the vpn network
depends_on:
gluetun:
condition: service_healthy
restart: unless-stoppedQ: I Get a long error mentioning OCI when bringing up the containers.
A: Stop both the containers from the Docker UI and delete them, run the command again, and it should start up fine. If this still happens double check you have set your VPN providers settings correctly.
More will be added as questions come up
Looking for some help, join our Discord community
If you are struggling with any steps in the guides or looking to branch out into other containers join our Discord community!

Buy me a beverage!
If you have found my site useful please consider pinging me a tip as it helps cover the cost of running things or just lets me stay hydrated.