Last updated on 6 April 2025
Please note if you are using DSM7.2 or higher you should use the Container Manager version of this guide from the menu.
If you are still using an older DSM version migrate to Dockge and you can use my new guides!
See the Dockge guide here to start migration!
This guide has reached the end of its updates
| Update | Date |
|---|---|
| Amended the path to save the compose file – this is for security, so the container has no access to the file contents. | 14/04/2023 |
What is Overseerr
Overseerr is a web front end for the users of your Plex Server, it allows them to request new Movies and Shows which are then passed to Radarr and Sonarr for automated download.
Let’s Begin
In this guide I am going to take you through the steps to get Overseerr up and running in Docker on your Synology NAS.
In order for you to successfully use this guide please follow the two steps below first.
This guide contains two parts:
- Part 1 — Setting up the container via the DSM GUI
- Part 2 — Setting up DDNS, Reverse Proxy and SSL
Part 1 — Container Set up (DSM GUI)
Downloading the Overseerr Image
Open up Docker within DSM and navigate to the ‘Registry’ section and search for ‘overseerr’ in the search box and download the ‘LinuxServer/overseerr’ version
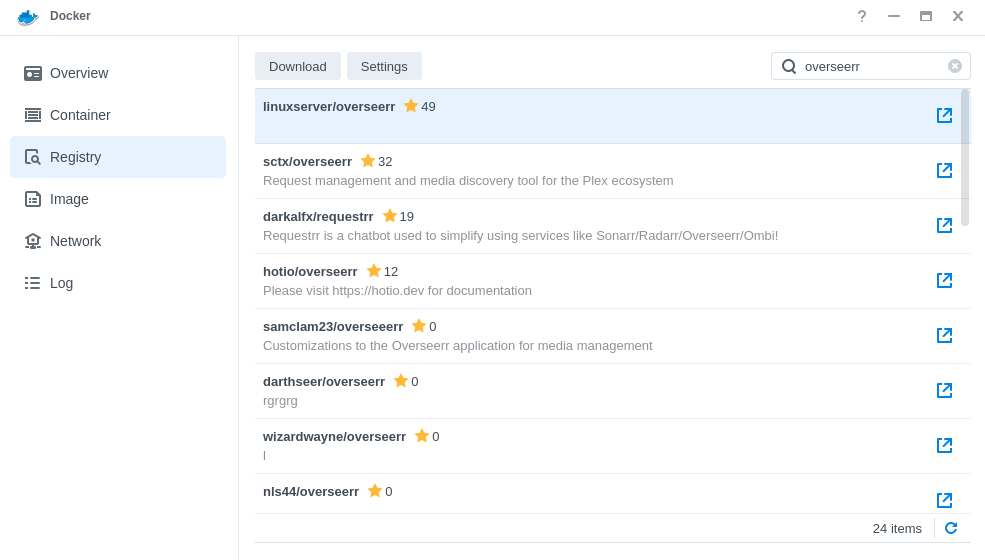
The pop-up box will ask which version you want to download, make sure you choose ‘Latest’ from the list of available versions.
You can check the status of the download over on the ‘Image’ tab.
Setting up the container
In Docker click on the ‘Image’ tab, in the list of your containers select the ‘Overseerr’ image and click on ‘Launch’
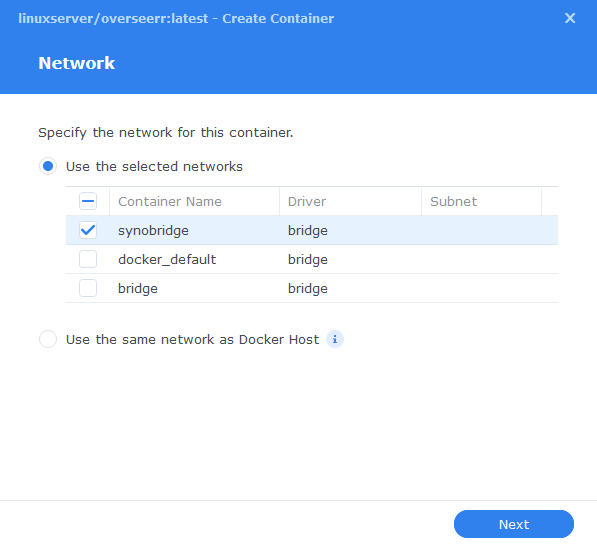
You will be greeted with the Network screen, we will be using the ‘synobridge’ network we created earlier select it from the list and click Next.
General Settings
Next you will be greeted with the General Settings screen, this is where you can start specifying some of your preferences.
You can change the name of the container to anything you like, and you may want to enable Auto Restart as this will ensure Overseerr starts automatically if you reboot your NAS.
You will also notice a Configure capabilities button — don’t change anything in here!
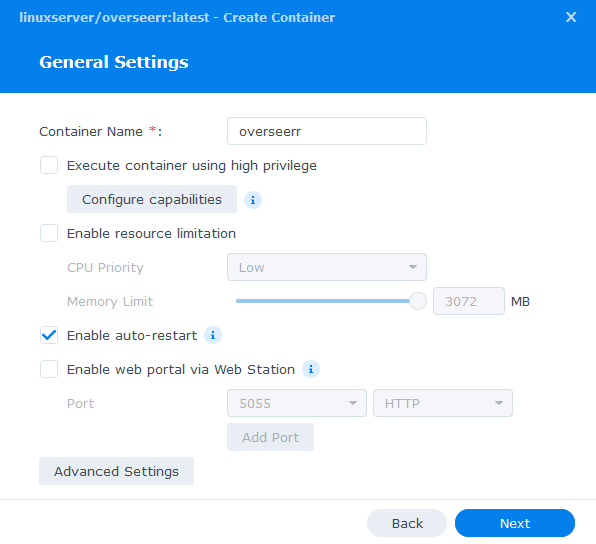
Next up we are going to click on the ‘Advanced Settings’ button, this will take you to a new window with a number of tabs which we are going to work through.
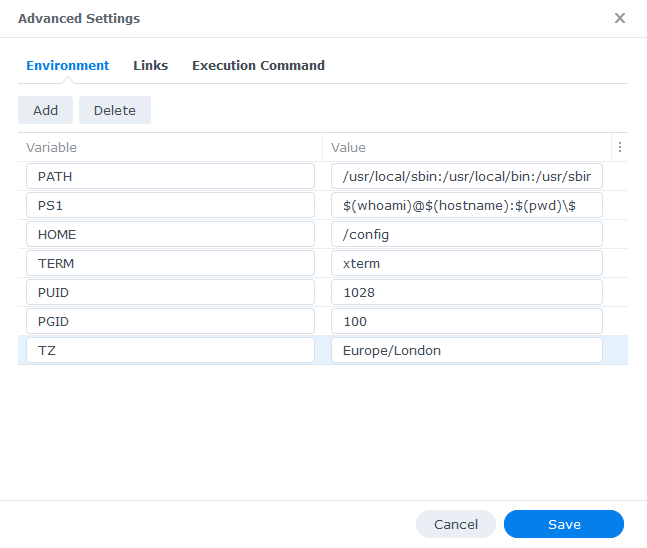
Environment Variables (PGID, PUID and Timezone)
Next we are going to set up a couple of environment variables that docker will use to allow the container access to our files and folders and also to tell it where we live in the world.
Click the Add button, and fill in the following details as per the table/screenshot.
| Variable | Value |
|---|---|
| PUID | The UID you obtained in the user setup guide |
| PGID | The GID you obtained in the user setup guide |
| TZ | Your timezone wikipedia.org/wiki/List_of_tz_database_time_zones |
Port Settings / Links
You do not need to set up anything on these tabs.
Press ‘Save’ to go back to the initial setup screen, then press ‘Next’
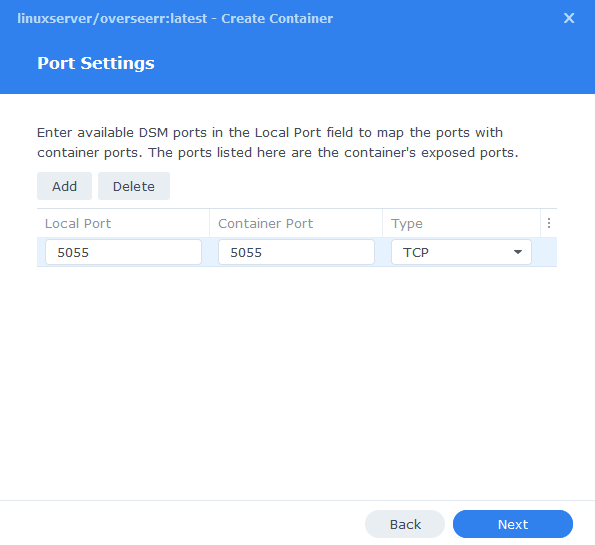
Port Settings
We won’t be changing any of the ports the container uses. You can repeat the ones shown on the right side of the settings page ‘Container Port’ onto the left side ‘Local Port’ once you have done this press ‘Next’.
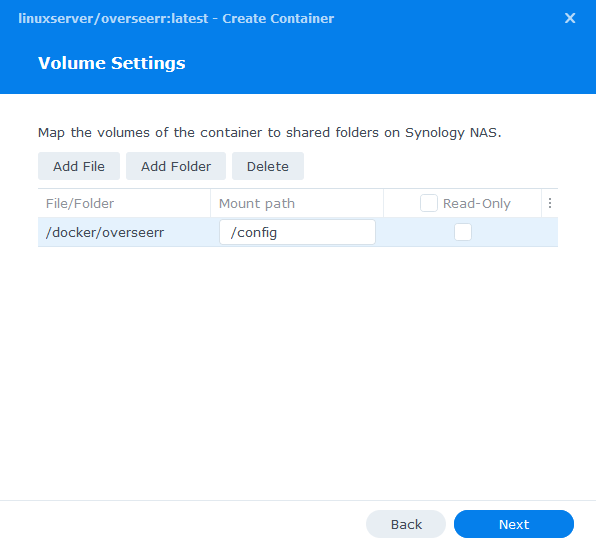
Volume Settings
We can now be specifying where Overseerr will store its configuration files.
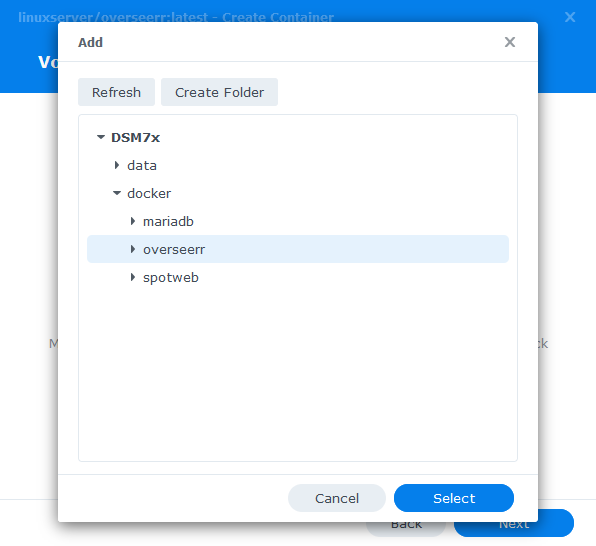
Click on Add Folder, select on the ‘docker’ share and create a new sub-folder called ‘overseerr’ select this folder and click ‘select’
In the Mount path section for this folder enter ‘/config’ it should now look like the screenshot below.
| File/Folder | Mount path |
|---|---|
| docker/overseerr | /config |
Click next to go to the final screen.
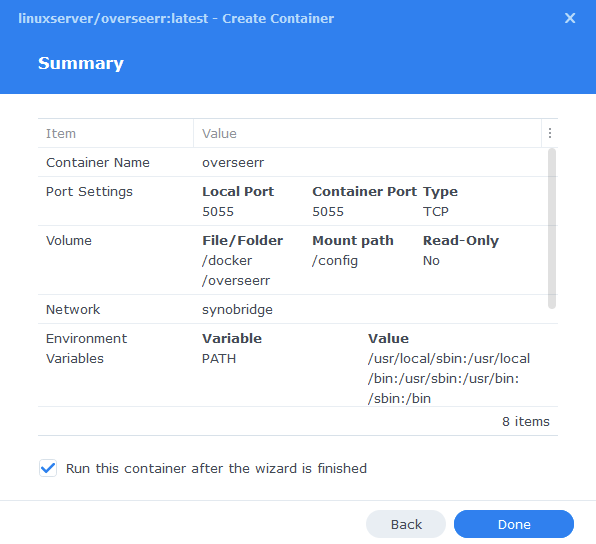
Summary
You have now completed the setup of the container.
You will be shown an overall summary of the settings we have specified, this is a good time to double-check everything is correct. Finally, click on Done and the container should start to boot.
You should now be able to access the web interface via the IP of your NAS followed by the port 5055
e.g. 192.168.0.40:5055

External Access
You have some choices when it comes to making your new container accessible from outside your home network, these come with different levels of security and convenience. This mini section is generic but covers the basics of getting this guide up and running and is entirely optional.
- Synology’s DDNS (Dynamic Domain Name System) with a TLS Certificate and Reverse Proxy
This is useful if you have some family members or friends that need access to something like Overseerr or Jellyseer and is covered below. - Tailscale or Wireguard VPN
If just you or close family in your household are accessing these services, and you don’t want to expose them to the internet this would be the more secure choice. See my other separate guides. - Cloudflare Tunnels
I don’t currently use these, so I would recommend watching the Wundertech guide on how they work.
A note on Double NAT or CGNAT
Unfortunately more ISPs are moving to these methods of address allocation as the IPv4 address space is getting low on available addresses. If your ISP is doing this your choices are more limited.
You can test if this is the case by checking the WAN IP on your Router/Modem settings and then comparing it to the one shown on portchecker.co. If they are different you are likely Double NAT and will either need to see if you can pay your ISP for a standard IPv4 address or use Tailscale or Cloudflare Tunnels for access.
Using the built-in tools on DSM
The first step of this process is to forward port 443 on your Router to your NAS IP Address, how you do this will depend on your router model, so please refer to its manual.
Router (External):443 > NASIP (Internal):443
Next make sure you have registered for a Synology Account as we are going to be using their DDNS service. https://account.synology.com/en-uk/register/ If you already have this set up move to the next step.
DDNS (Dynamic Domain Name System)
A DDNS address allows you to get external access to your container via an address provided by Synology, this is useful on home internet connections where your ISP will change your IP address on a semi-regular basis.
In the DSM Control panel go to ‘External Access’ and then to the ‘DDNS’ tab
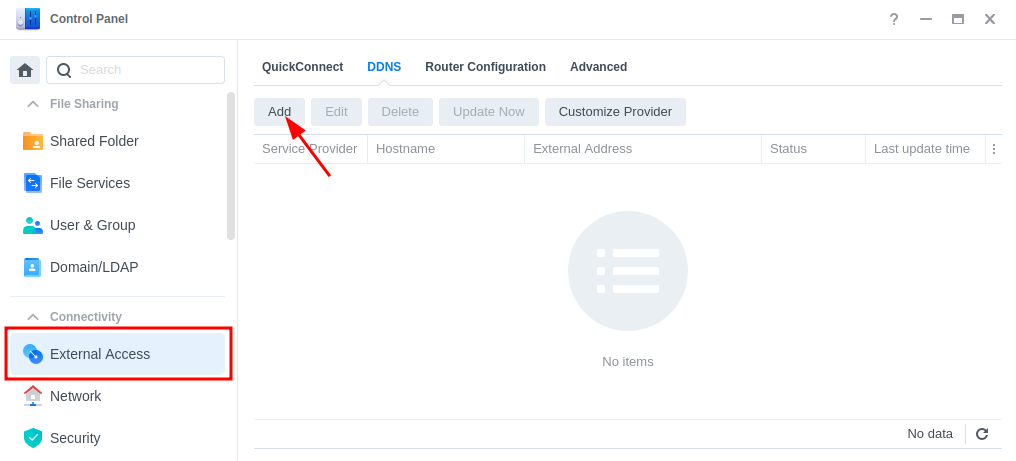
Click on ‘Add’, then fill out the following sections.
| Section | Value |
|---|---|
| Service Provider | Synology |
| Hostname | This will be the unique address just for you so keep the name generic. minecraft.synology.me = BAD myawesomenas.synology,me =GOOD |
| Email: | Log into your Synology account |
| External Address (IPv4) | This should be filled in automatically |
| External Address (IPv6) | This should be filled in automatically if your ISP is using IPv6 |
| Get a Cert from Let’s Encrypt | Tick this box |
| Enable Heartbeat | Tick this box |
Now press OK, DSM will apply your settings. It can take a few moments to set up and the DSM interface will refresh. You will likely receive a certificate error which you will need to accept to get back into DSM.
Reverse Proxy
We are going to set up a reverse proxy subdomain for the address you just register. This means you and your users can access the container without using a port number as it will route all traffic through the secure 443 port.
Go back into the Control Panel and access the ‘Login Portal’ then in the ‘Advanced’ tab click ‘Reverse Proxy’ and then click on ‘Create’.
We are now going to enter some rules, so when you or your users access the URL specified the request will automatically be sent to the containers web UI.
Use the settings below, you will need to amend the Hostname sections in line with the hostname you registered earlier, and the IP of your NAS.
| Setting | Value |
|---|---|
| Reverse Proxy Name: | Give it a meaningful name in line with the container you are setting up. |
| Protocol: | HTTPS |
| Hostname: | containername.xxx.synology.me ‘containername‘ will be the name you want to use to access this container ‘.xxx.synology.me‘ will be the exact name you registered earlier |
| Port: | 443 |
| Protocol: | HTTP |
| Hostname: | ‘localhost’ or your NAS IP address |
| Port: | The UI Port Number from the yaml in the guide you are following |
On the second tab ‘Custom Header’ click on Create then WebSocket, this will add two entries for WebSockets to function correctly, you can now press save.
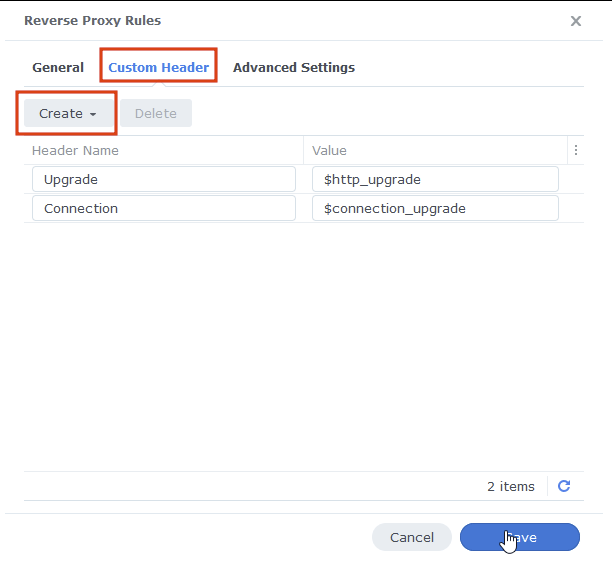
You should now be able to access the web UI of the container by going to the address you just set up in the reverse proxy, it will be a secure connection, and you should have no certificate errors.

As Overseerr has a really nice initial setup UI that takes you through the basics I won’t be covering this. The key part once completed will be to import your Plex users, so they can log in to the UI and begin making requests.
You are ready to roll 🙂
| Historic Updates | Date |
|---|---|
| New guide Published | 19/03/2022 |
| Updated with DSM7.1 Steps and Screenshots | 21/06/2022 |
| Added new port settings and Docker Bridge Network | 23/07/2022 |
| Compose version number removed and small wording amendments | 09/04/2023 |
Looking for some help, join our Discord community
If you are struggling with any steps in the guides or looking to branch out into other containers join our Discord community!
Buy me a beverage!
If you have found my site useful please consider pinging me a tip as it helps cover the cost of running things or just lets me stay hydrated. Plus 10% goes to the devs of the apps I do guides for every year.



Something strange is happening for me, I set it to the proper port in the reverse DNS and use overseerr.xx.synology.me (xx of course my own domain)- but every time I go to the domain it brings me to the same place as my xx.synology.me domain. I am doing something stupidly wrong here, what? That or it’s being buggy on me.
Try turning off auto redirects
For DSM 7.0 and above: Go to DSM Control Panel > Login Portal > DSM, untick Automatically redirect HTTP connection to HTTPS for DSM desktop and click Save.
The box unfortunately was already unticked. I tested it out a second time, making a new one, adding a different port – but unfortunately it always brings me back to the standard DSM login as if I entered port 5000. Any ideas?
For some reason I can’t see your original comment – have you tried specifically typing https://theoverseerraddress this will stop DSM hijacking the http:// connection.
Hi, this is a great resource, and I’ve learnt so much from here thanks to your really clear explanations.
I am still having a little difficulty though, hoping you can help. For setting up remote access to Overseerr I’ve had to go with noip since Synology won’t let me use their DDNS without a valid serial, and my Sky router has very limited options for DDNS. As such there was no SSL Certificate checkbos when registering the Reverse Proxy.
I’ve set everything up but still can’t access from outside my local network (inside is fine), and I wondered if it was an SSL certificate option, or if there are firewall rules that I should be allowing to enable this?
Hi! I’m having problems with the reverse proxy with Overseerr. Not having the same issues with any of my other containers. I set the source protocol to https, hostname to requests.mydomain.com (obviously not mydomain.com), port 443. For destination, I’ve set it to http, ip address of my nas, and lastly port 5055. I get a refused to connect error. Have you seen this with your setup? Is it related to
https://docs.overseerr.dev/extending-overseerr/reverse-proxy.
Any help would be appreciated as you seem to have the only example of Overseerr working with a synology reverse proxy.
Scratch that. I got it to work. I just didn’t set my internal ip address to the correct spot!
Nice one, I have a nice list of things to check that I will be adding to the FAQ very soon, as there are all sorts that cause this.
Hey, apologies for the late reply I am away for work at the moment.
Did you sort this if not I will ping you an email.
man this blog rocks, thank you for doing this. Learned a ton
Thanks glad it has helped
hiya. im trying to add a the sonarr server to overseerr and everything works but the root folder drop down is blank and i cannot go any further. can you tell me how to get this to populate? thank you
Hey – it could be that they are not connecting. Rather than the IP address of your NAS try using one of the following in the Hostname/IP section:
172.20.0.1 (synobridge gateway IP)
sonarr (yes just the word sonarr assuming your sonarr container is called that)