Last updated on 5 September 2025
Important or Recent Updates
| Historic Updates | Date |
|---|---|
| Updated guide for Container Manager and using Macvlan | 14/05/2023 |
| Added a new section to ensure DSM continues having network access. | 02/06/2023 |
| Guide updated so you can choose between Macvlan or Bridge mode | 12/08/2023 |
| Added additional security option to the compose to restrict the container from gaining new privileges | 25/10/2023 |
| Fixed issues I introduced with the recent changes in my mission to make things more secure. It was so secure I broke it! Added the appropriate permissions/capabilities at start up for the container. | 29/10/2023 |
| Removed the requirement for the synobridge as this container can just use its own bridge, and added the Host network mode, so all three are a choice. | 28/01/2024 |
| Removed the WEB_UID and WEB_GID from the config to avoid issues with ID’s conflicting inside the container. I will update again once I have some time to work around this. | 03/04/2024 |
| Some minor amends to sync up the information across this guide and the AdGuard one | 01/08/2024 |
| Removed two unneeded capabilities from the bridge version of the docker compose as they are not required. | 16/11/2024 |
| Guide updated for the all new v6 of Pi-hole (Note if you upgrade from v5 you effectively have to change all the compose settings in line with the new guide so might be worth just scrapping and starting fresh unless you really need stats etc Please note as recommended by the Pi-hole dev team I have added a Watchtower exclusion label to the compose so you can do manual updates. Automated ones could result in you losing internet access if a bad update takes place. Edited again today as I left in a variable that is not required in Host and Macvlan mode “DNSMASQ_LISTENING” sorry. | 20/02/2025 |
| Had a rethink of the Guide, and it has been rewritten to include an overdue request of including Unbound! | 24/02/2025 |
| Fixed my idiocracy adjusted the MACVLAN section to actually put Unbound on the same network.. Facepalm! | 16/03/2025 |
| I need to do some more testing of Unbound as part of the guide and I don’t currently have a lot of time so to avoid issues I have removed it from the guide for now. | 18/03/2025 |
| Added the NTP server port and environment variable so you can choose if you need it or not | 05/09/2025 |
What is Pi-hole?
If you are looking to get advertising and tracking blocked across all the devices on your network a Pi-hole will have you covered. It’s a locally hosted Domain Name Server and uses block lists to stop adverts.
This guide will get you set up with Pi-hole and cover some basic initial settings, I recommend checking out the documentation for all the various features available.
Host vs Bridge vs Macvlan Network Modes
You need to decide which mode of Networking you want to use, I have outlined the key points below in general order of preference.
Host:
Host mode uses your NAS underlying network to run the containers network services, so it will be reliant on the NAS not using any of the required ports for the container. However, this makes it easy to set up, but you need to make sure no other service is using the required ports. All your clients will appear correctly as independent devices and stats.
Bridge Mode:
The main benefit of Bridge Mode will be the ease of setup however you will find that all clients on your network will appear under the same IP as the Bridge 172.20.0.1. This won’t impact ad blocking, but it will mean you can’t apply device specific rules etc.
Macvlan:
This gives you the benefit of Pi-hole having its own IP address on your network, all clients appear with their real IP addresses allowing you to assign specific rules and give you some nicer stats. However, one downside is that your NAS will not be able to use Pi-hole for DNS, due to the additional security features of Macvlan and its communication with its host. This is generally not an issue unless you wanted to use your Ad blocking with Tailscale.
Please note if you have a bonded network connection (two LAN ports bonded into one) then try using ‘bond0’ in the network set up element of this guide.
Let’s Begin
In order for you to successfully use this guide you will need to check that your Router allows you to change your network DNS servers, this is usually found in the DHCP settings.
Please follow the initial guide below to get a restricted Docker user set up, then come back here.
Folder Setup
Let’s start by getting some folders set up for the container to use. Open up File Station create the following.
/docker/projects/pihole-compose
/docker/pihole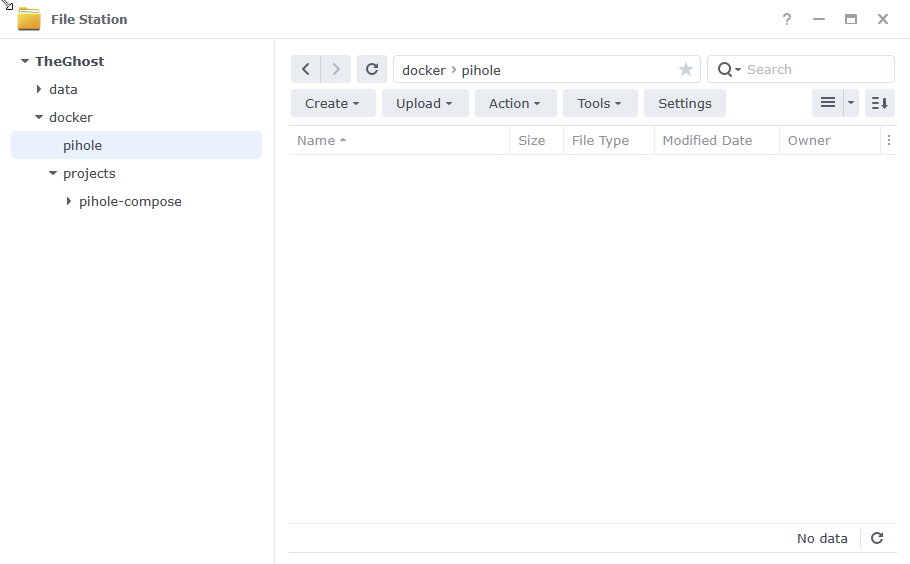
Container Manager
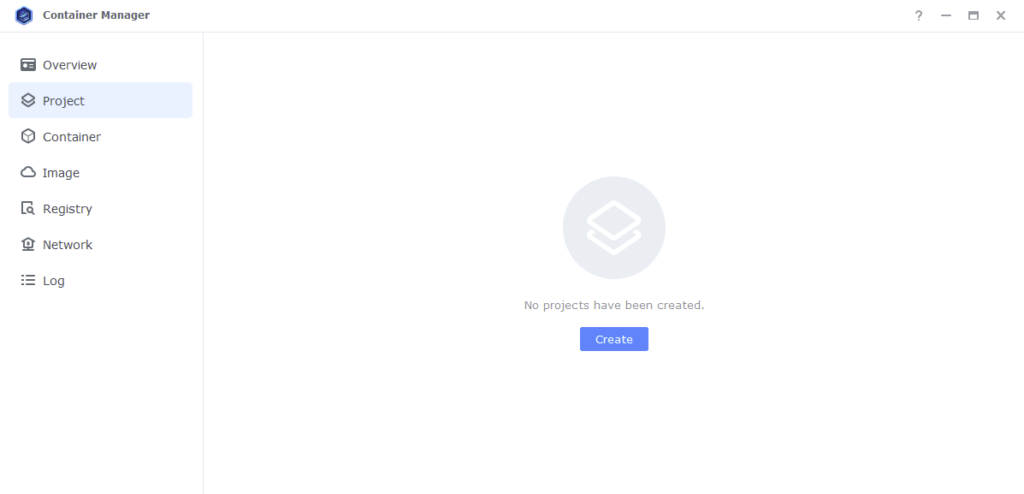
Next we are going to set up a ‘Project’ in Container Manager. Open up Container Manager and click on Project then on the right-hand side click ‘Create’.
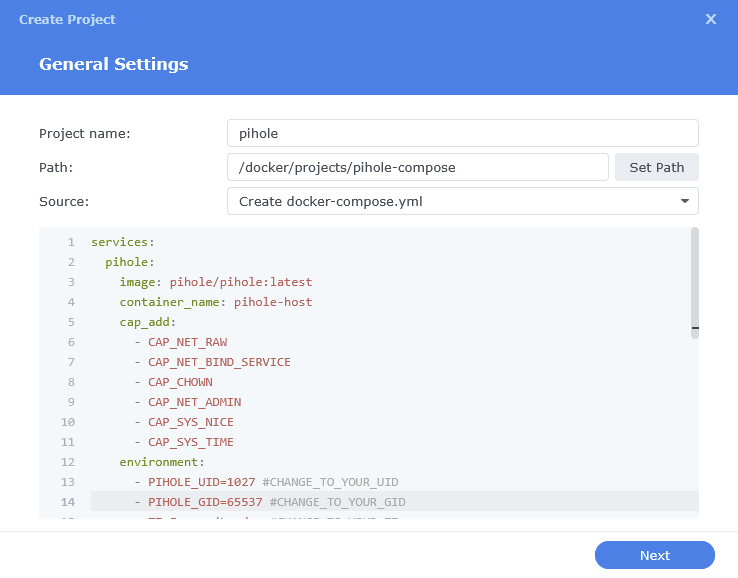
In the next screen we will set up our General Settings, enter the following:
| Section | Setting |
|---|---|
| Project Name: | pihole |
| Path: | /docker/projects/pihole-compose |
| Source: | Create docker-compose.yml |
The code section of the below will be blank until we move to the next step.
Next we are going to drop in our docker compose configuration. You now need to decide if you are going to go with Host, Bridge Mode or Macvlan. Jump to the appropriate page to follow the setup.
Host – Page 2
Bridge – Page 3
Macvlan – Page 4
hi, just discovered your site, it is amazing !
I ‘m using talescale with my synology, and I have the following message :
Code d’erreur : PR_END_OF_FILE_ERROR
I connect to : tailscaleIPAdress:8000/admin/login.php
Hey thanks 🙂
The machine you are on is it connected to Tailscale – Do you have subnetting enabled as you can then just use the NAS IP instead of the tailscale one
Have you tried using this with Unbound? Do you have one in the works that combines Pihole with Unbound?
I did have unbound running a few years ago on my original PiZero install – Let me check what it entails for Docker.
Thank you for this guide. I have followed the whole guide and when I click “done” I get the error “Start container pihole failed: {“message”: “driver failed programming external connectivity on endpoint pihole: error starting useland proxy: listen tcp4 0.0.0.0:53: bind: address already in use”}
I tried a “netstat” and it does not indicate any other open processes on port 53
Can you help me.
Thank you
Hey – can you try changing the network mode to host – you will need to review the ‘ports’ section.network_mode: host
Try changing the ports section to include ‘udp’
– 53:53/udp
Hello. It works!
Thank you Dr.
Hi, thanks for this guide.
I want to see the device names in the Pihole statistics. Your last sentence states “Also note as we are not using Pi-hole as the DHCP server you will not be able to see the names of the devices in the statistics just their IP addresses.”
Can you advise.
So there is an option within the UI Settings > DNS > Conditional Forwarding, you will need to set the IPs as described in the info, I never managed to get this to function on my own network.
Local network in CIDR notation = Basically take your NAS IP and change the last number to 0 (e.g 192.168.0.101 would be 192.168.0.0)
IP address of your DHCP server (router) = Your Router IP
Hello there, thanks for putting this together! The pihole container image downloads, it gets created with all my settings, but I can not load the pihole login page.
When I check the log (container manager>container>log), I see the following repeating error message:
lighttpd: no process found
Stopping lighttpd
pihole-FTL: no process found
Stopping pihole-FTL
(repeat, repeat, repeat)
I followed steps 1,2,3 from your “initial setup” pages before I created the container… not sure what I missed. I will try again later this week but I wonder if these error messages immediately show that I missed a specific step?
Check to make sure your PUID/PGID (UID/GID)are correct in case it is struggling to write the config into /docker/pihole
Hi Doctor, thanks for the fast response! I think my GUI and UID are correctly set (see below). I did a bunch of Googling of similar issues, and here’s what I changed in the YAML file to get it to work.
(change #1) I changed DNSMASQ user from pihole to root:
DNSMASQ_USER=root
(change #2) I commented out the 4 lines requiring UID/GID:
# – PIHOLE_UID=1033
# – PIHOLE_GID=100
# – WEB_UID=1033
# – WEB_GID=100
I don’t know what’s going on under the hood, but this is what worked for me. Do you think I’m doing something particularly stupid/insecure with these changes?
I suspect it’s a permission issue as removing those lines and changing to root means all the files are owned by the root user in the container. So has exclusive permissions to the mounted folder.
Hey Max,
I have run into this exact same issue. Were you able to fix the permissions issue at all? If so, are you able to share the resolution steps?
Thanks