Last updated on 28 September 2025
Important or Recent Updates
| Historic Updates | Date |
|---|---|
| New guide Published | 18/03/2023 |
| Swapped to using the version direct from Tailscale | 20/03/2023 |
| Fixed the Routes and Subnets command as seems to run differently depending on some configs | 27/03/2023 |
| Amended wording relating to exit nodes and DNS | 09/04/2023 |
| Changed the Tailscale Up command to use the DNS servers specified in the admin console – amended the DNS section accordingly (thanks Roy) | 10/12/2023 |
| Screenshot updates based on latest workflow confirmed still working correctly in live setup | 03/01/2024 |
| Added WireGuard Kernel Module Install steps | 02/02/2025 |
| Removed the WireGuard Kernel Module steps – Apologies I didn’t realise that Tailscale is Userspace only. | 24/04/2025 |
| Added steps on how to get TLS (HTTPS) certificate for your services! | 17/09/2025 |
Thanks to “danger-pig” for spotting an update needed for the Tailscale Serve command adding --bg to ensure it continues to run in the background | 28/09/2025 |
What is Tailscale?
Tailscale is very clever, it’s a VPN mesh network that allows you to use all your local network resources such as your NAS, all your Docker containers and even other devices on your network remotely.
This guide is based on the official documentation here which covers the basics however I received enough questions via Discord and email that I felt it warranted a step-by-step walkthrough.
This will take you through the steps to get Tailscale running on your NAS and then accessing via an Android mobile.
Note: For anyone who likes to follow along in video format this video recently released by Alex from Tailscale is great!
If you already have Tailscale running, and you are looking to enable TLS (HTTPS) for your containers see the steps at the end of the guide.
Let’s begin…
Installing Tailscale
The first step is to install the Tailscale Package (believe it or not we are not using Docker!!)
You have a couple of options here, either install the current version via the Package Centre or grab the latest version direct from Tailscale.
We are going to get the latest version in this guide, if you ever want to update either check back on newer versions via the link above or eventually the Package Centre version will catch up!
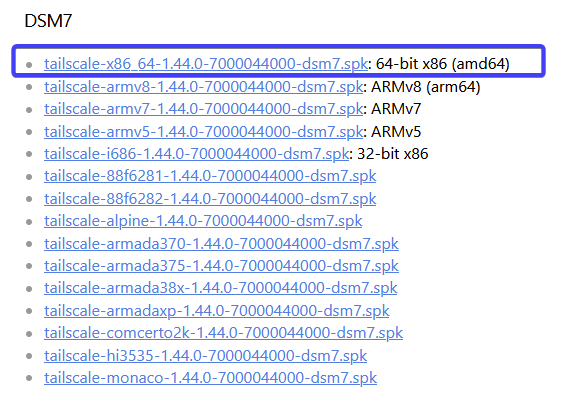
Open the link above and grab the version of the of package which works with your model of NAS. Most + models will use the version shown in the screenshot (you can find out of what type of CPU your NAS has here)
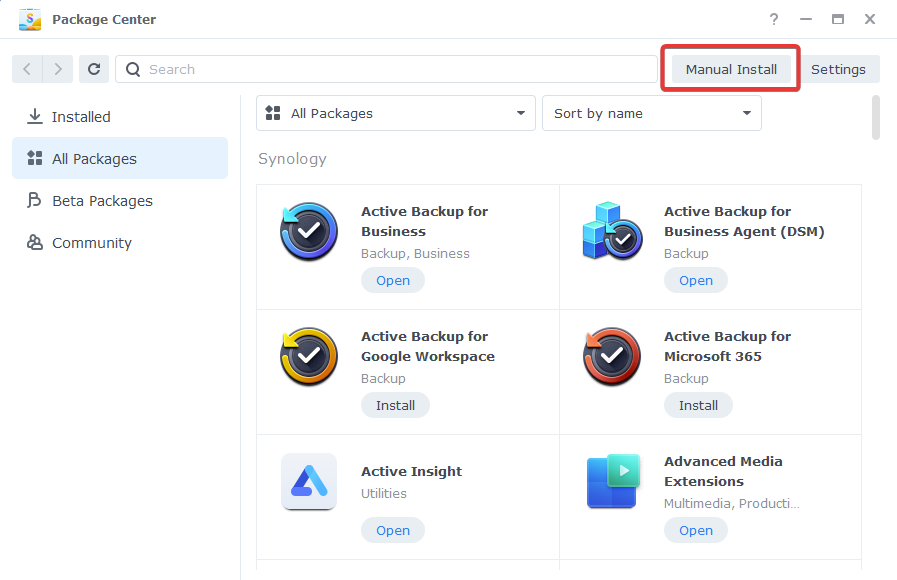
Once downloaded pen up the Package Centre and Click on ‘Manual Install’ on the top right. Then browse to your downloaded package and click Next.
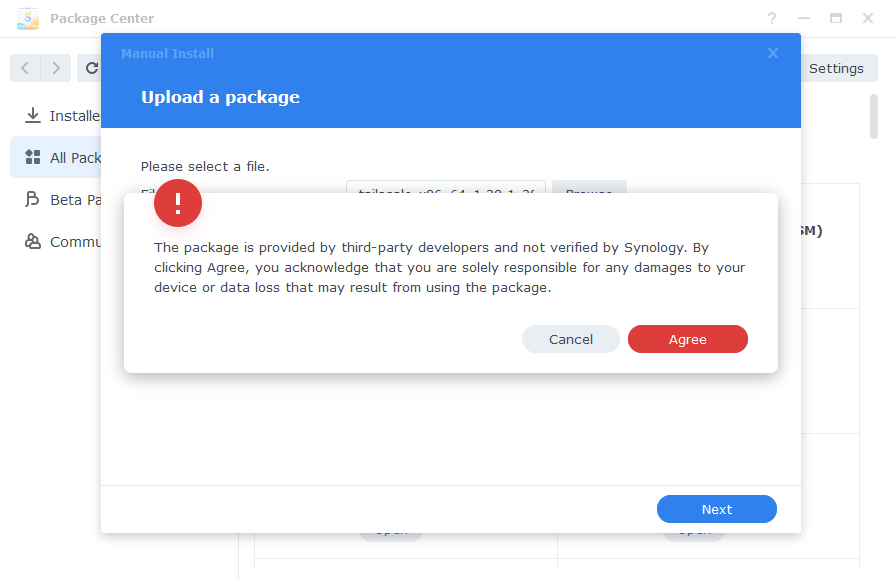
You will be asked to accept all responsibility by installing this package, of course we will agree!
Once the package has finished either find it in the list or search for it in the top bar and click Open.
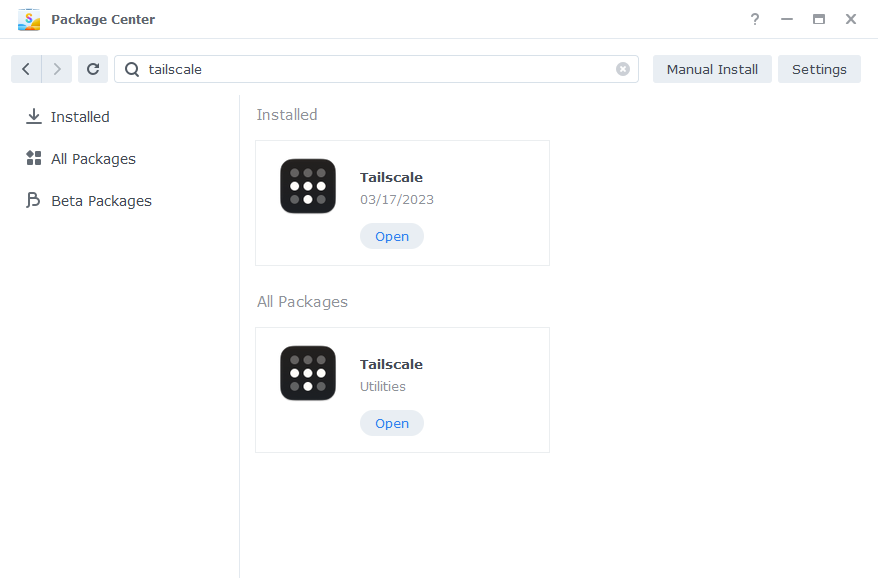
A new browser window will open, and it will ask you to Log In to your Tailscale account
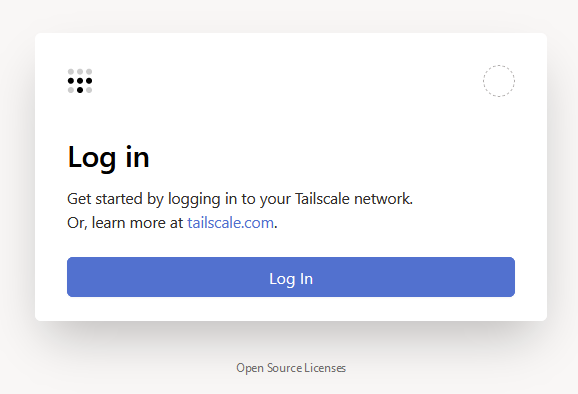
Click log in, and you will be taken to the next screen with different options to log in – Tailscale uses sign ins via a number of providers Google, Microsoft, GitHub etc select the one you prefer and login. You will use this to sign in on all devices going forward.
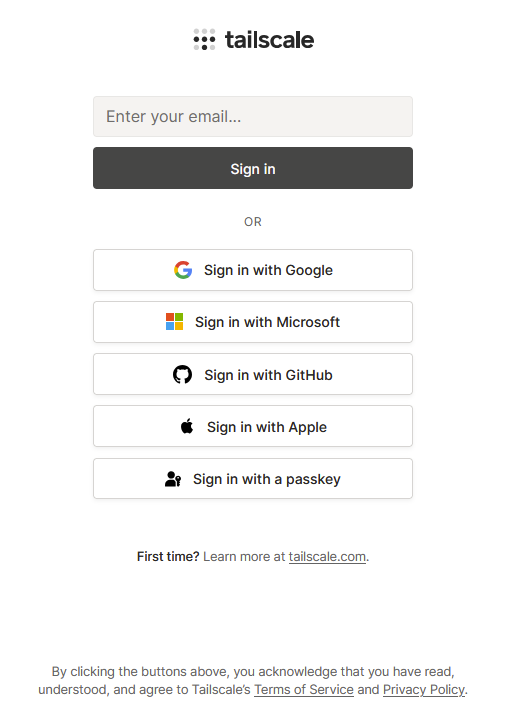
Once you have signed in you will see the screen below which is confirming the details of the device being added to your account. Click ‘Connect’.
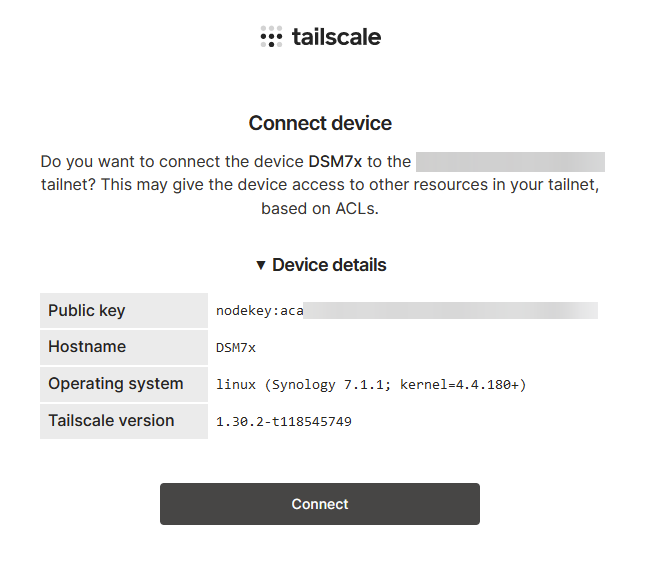
You can now visit https://login.tailscale.com/admin/, and you will see your NAS in the list of your devices – I have blurred out my other devices in the screenshot, but you can add up to 25 for free.
You will see that you NAS has been assigned an IP address on the Tailscale network. We want to be able to access all our services via their original IP and ports rather than having to remember a new IP address. So lets carry on…
Enabling Outbound Connections on DSM7 and up
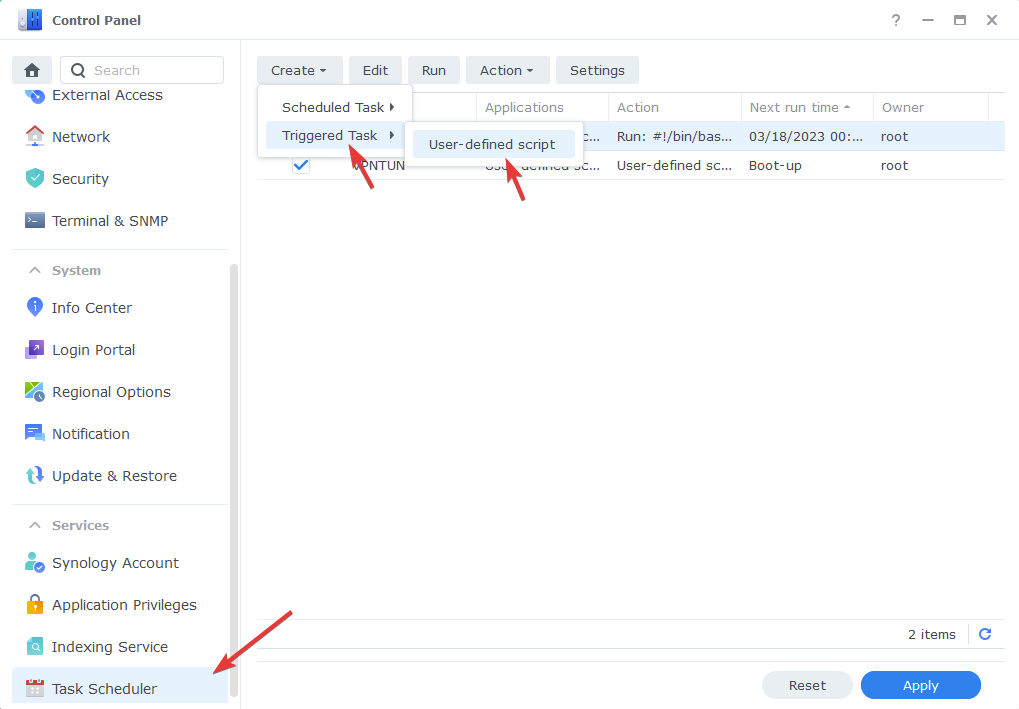
In order for our containers and apps running on DSM to have outbound access to the Tailscale network we need to enable this via a boot up command. This is nice and easy as we can use the Task Scheduler in the Control Panel.
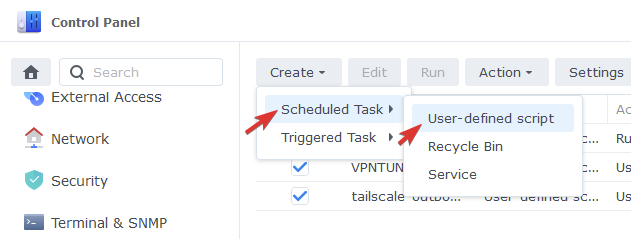
So open up Control Panel > Task Scheduler > Create Task > Triggered Task > User-Defined script
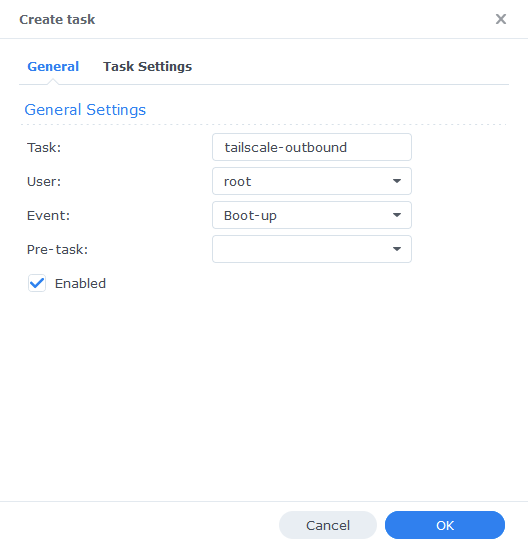
In the Create Task window that appears enter the following information.
| Section | Setting |
|---|---|
| Task Name: | tailscale-outbound |
| User: | root |
| Event: | Boot-up |
| Pre-task: | Leave this blank |
Now click the ‘Task Settings’ tab and enter the code below in the ‘User-defined Script’ section
/var/packages/Tailscale/target/bin/tailscale configure-host; synosystemctl restart pkgctl-Tailscale.service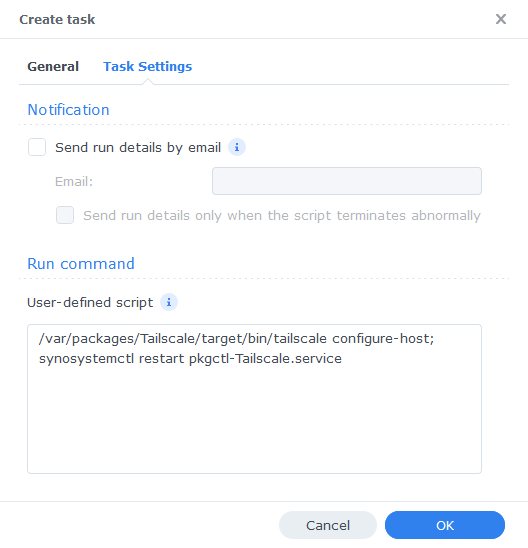
Now click ‘OK’ you will be warned about running scripts as a root user, you can safely click the scary Red OK button.
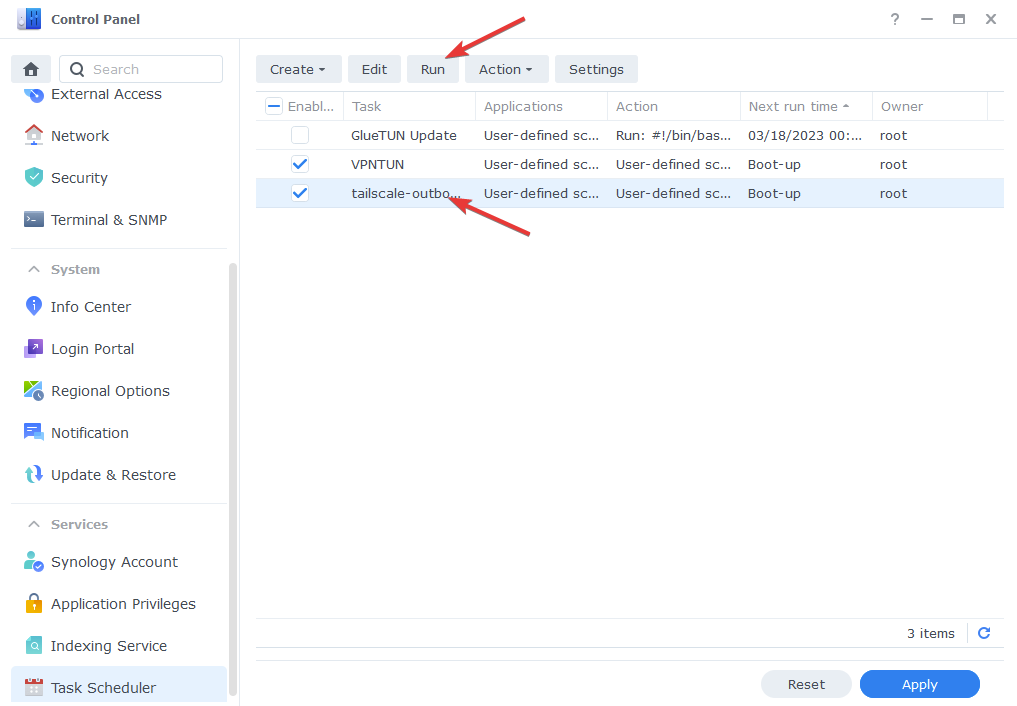
The final step for this section is to run the script, it will then run on each reboot automatically, just select the task from the list and then click ‘Run’ and a then say ‘Yes’ to the pop-up.
Subnets, Routes, and Exit Nodes
So one more step to set up on the NAS side of things, we now need to enable the following items:
- Subnets – (Advertise Routes) In order for us to access other devices on our network we will allow the Tailscale connection to look across the network
- Exit Node – By default your internet traffic will go via the connection on the device you are using. For example if you are using your mobile on 4g when you go to Google.com this is going directly from your mobile connection. However, if you enable the Exit Node feature you can route your traffic via your NAS and out of your home internet connection. If you have Ad-Guard or PiHole in place this also means your ad blocking works as well!
You can do this next part in two ways either via SSH or for simplicity I am going to show how via Task Scheduler.
Go back to the Task Scheduler in Control Panel and Click Create > Scheduled Task > User-defined script.
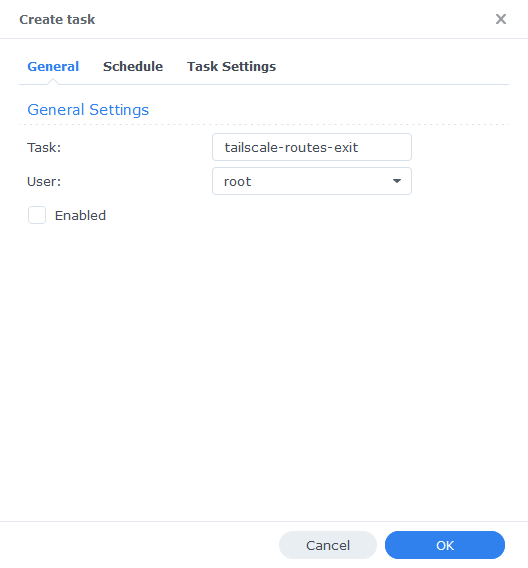
Next we set the following options:
| Section | Setting |
|---|---|
| Task Name: | tailscale-routes-exit |
| User: | root |
| Enabled: | Unticked |
Nothing need to be amended on the Schedule tab, then in the Task Settings tab enter the code below into the User-defined script section.
Before you do this though you need to edit the –advertise-routes=192.168.0.0/24, this must correspond to your own local subnet! The easiest way to figure out this is by taking your NAS IP address for example 192.168.0.79 and changing the final digit after the . to 0 ( 192.168.0.0)
Also, the –accept-dns=true will tell Tailscale to use the DNS servers set in the Admin Console we will visit this a bit later.
tailscale up --accept-dns=true --advertise-exit-node --advertise-routes=192.168.0.0/24 --reset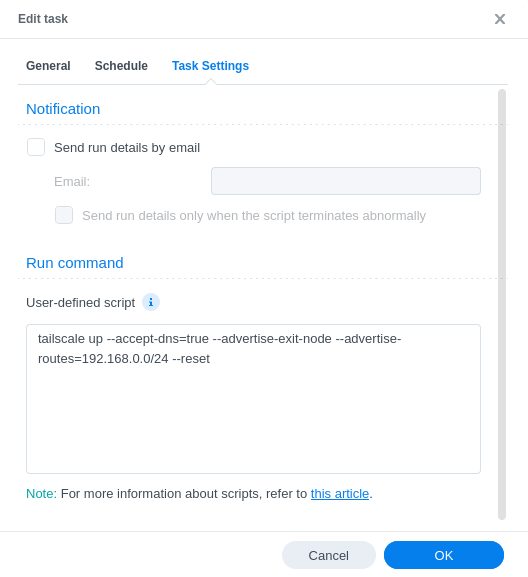
Now press OK and again as per the last section accept the warning. You will then need to run the command by selecting it from the list and pressing ‘Run’. This is everything completed on the NAS side of things!
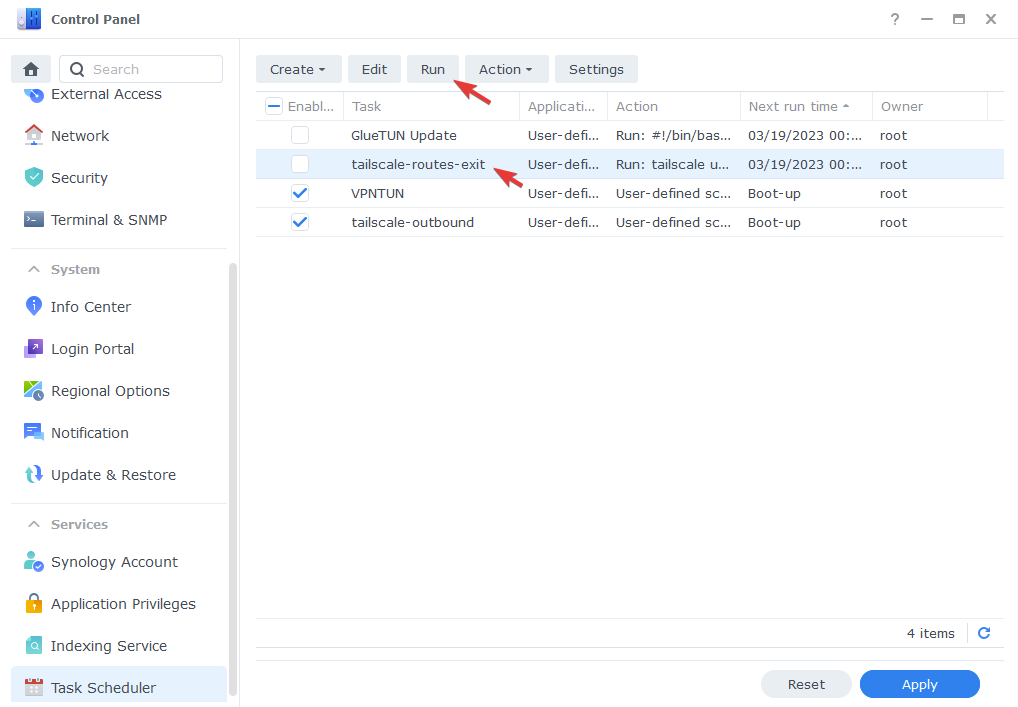
Some users have reported that these settings don’t immediately appear in the Admin Console – So a reboot may be required for them to appear.
Tailscale Admin Amendments
We are now going to make a couple of changes in the Tailscale admin panel. Head back to https://login.tailscale.com/admin/ you will notice our NAS shows the extra enabled features of Subnets and Exit node.
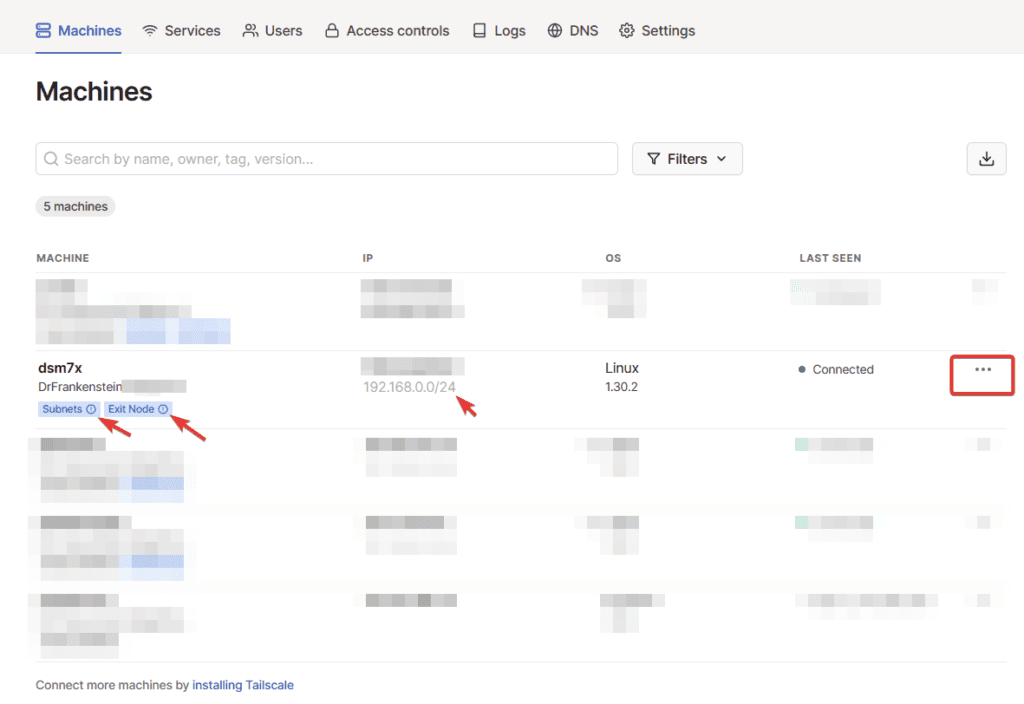
Click on the three dots next to your NAS and click on ‘Disable Key Expiry’ this will mean you don’t need to manually renew encryption keys every few months.
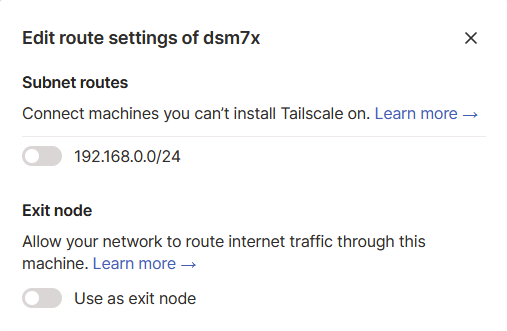
Then click the three dots again and select ‘Edit route settings..’ and you will see the screen below. Turn on both the ‘Subnet routes’ and ‘Exit Node.’ These will allow you to access devices and applications on your local network and enable the ability to route your internet traffic through the NAS.
Network wide ad-blocking / DNS
Our final step in the Admin Panel is to make sure we have some DNS servers in place, otherwise you will not have internet access via Tailscale.
In the video below I add local IPs for AdGuard or Pi-hole if you are not using those either add your preferred DNS provider(s) or select from the built-in ones.
In your Tailscale admin panel click DNS from the top section
Next scroll down to the Nameservers section and as per the video below click ‘Add Nameserver’ then select either from the drop-down list or Custom if you want to add the IP address of your Adguard or Pi-hole instance.
Mobile Setup
We are into the final stretch! Now the NAS is set up and our network running we can start adding more devices, I am using an Android phone as an example in this guide. However, adding an iPhone or Laptop, or any other device such as a remote NAS is pretty much the same.
The first step is to download the Tailscale app from the Google Play Store or you can install directly from Tailscale. I am not showing these steps as they should be self-explanatory.

Once installed open up the app, and it will ask you to sign in, use the same account you used earlier and follow the steps (not showing these as it varies slightly per account type)
Next you will see a screen to add the device to your account just press Connect.
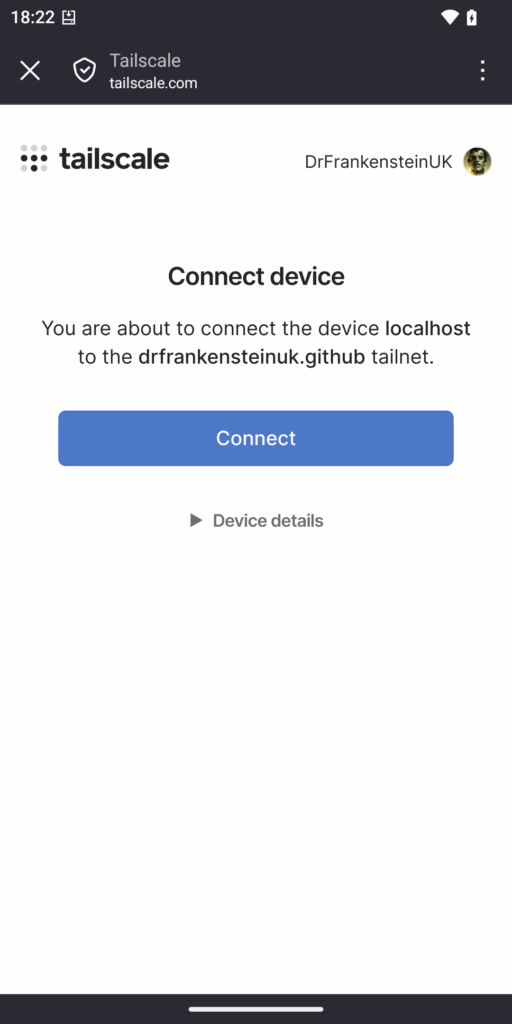
You will now see a list of your devices on the Tailscale network, you may already be connected if not turn on the connection on the top left of the screen.
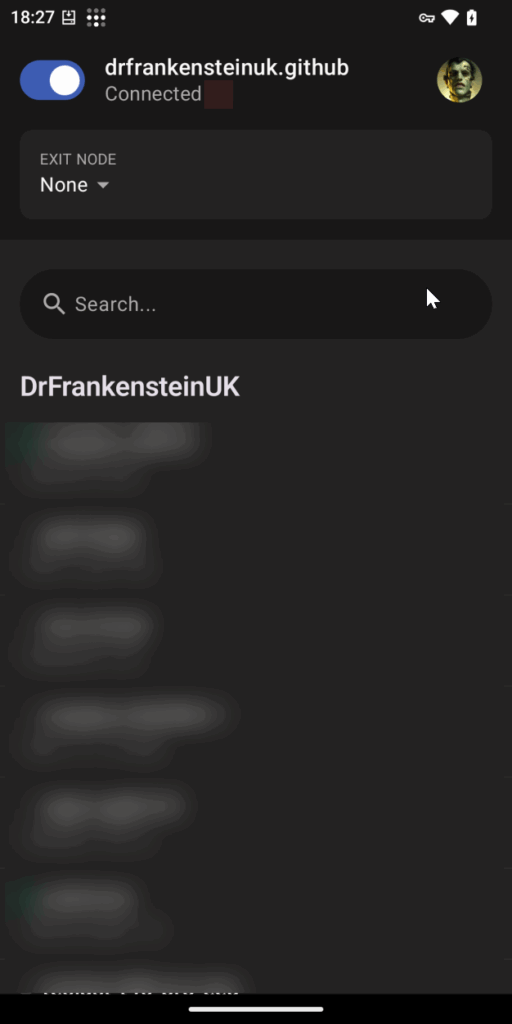
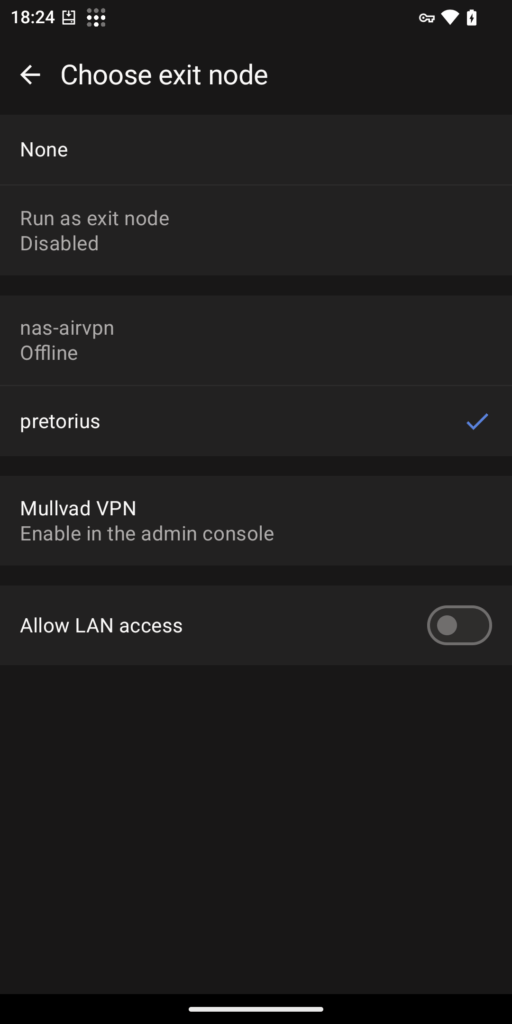
We need to select our exit node and turn on subnet access. Touch the Exit Node drop down at the top of the screen, you should see your NAS in the list of nodes and then turn on Allow LAN access at the bottom of the screen.
That’s it! You can now access all your services via a mobile connection or Wi-Fi on someone else’s network.
Enabling TLS (HTTPS) Certificates for your services
Thanks to Kevin for providing these steps and also the source FNL_KUJ on Reddit. This is generally best used with Vaultwarden as most other containers don’t require https://
We will be making use of Tailscale Serve in order to get a TLS Certificate for our Tailnet name.
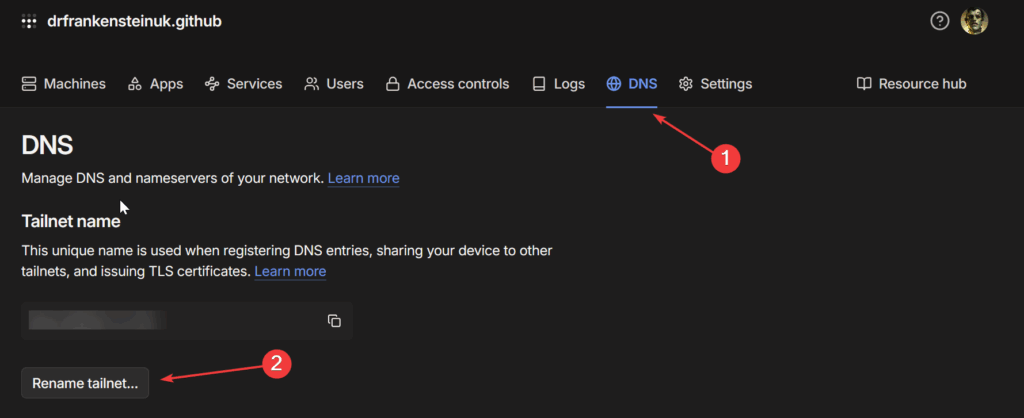
Firstly make sure you are happy with your Tailnet name this is found in your Admin Panel under DNS, essentially this is the domain name for your network. You can rename it but its rolling the dice on what names you receive.
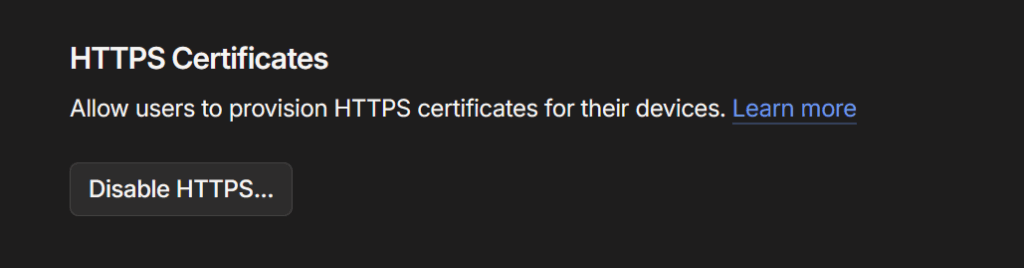
On the same page towards the bottom also enable HTTPS if it is not already turned on.
We are now going to run some commands via SSH to get our Certificate and then Proxy the connection.
SSH into your NAS which is covered in my Restricted Docker user Guide and then run this command. Replacing syno_name with the name of your NAS in your Machines list in you Tailscale admin panel and the tailnet-name to the one you saw earlier in the DNS settings. This will request the certificate for our NAS.
tailscale cert syno_name.tailnet-name.ts.netWe are then going to specify a proxy setting for the container we want the certificate to cover. This will redirect traffic sent to port 8443 (The port we will use for TLS Connections for Tailscale) to port 8122 which in this case is Vaultwarden.
tailscale serve --bg --https=8443 http://localhost:8122You can now check this is set up as specified by using the command below
tailscale serve statusYou will see the following output
$ tailscale serve status
https://syno_name.tailnet-name.ts.net:8443 (tailnet only)
|-- / proxy http://127.0.0.1:8122You have completed the steps required! – Things to note in this example we used Vaultwarden, you will use the full address as shown in the final output including the port number in your app and browser extension set up. And of course the device accessing this address must be connected to Tailscale.
GlueTUN as Exit Node
A few people have requested this in the comments and some on Discord already set this up. So here are the basic steps to add a Tailscale exit node that uses the VPN connection. You layer this compose below into your existing GlueTUN compose and then just generate a Auth Key.
Generate an Auth Key
– Name the key
– Set to 90 day expiry (You will have to renew this)
– Set as Pre-approved
– Leave other options un-ticked/defaults
Once added you need to turn on the Exit node Route in your Tailscale Admin Panel
tailscale:
image: tailscale/tailscale:latest
container_name: tailscaled-vpn
environment:
- TS_ACCEPT_DNS=true
- TS_AUTHKEY=tskey-auth-kucksj1CNTRL-
- TS_EXTRA_ARGS=--advertise-exit-node
- TS_HOSTNAME=nas-vpn
- TS_STATE_DIR=/volume1/docker/gluetun
cap_add:
- NET_ADMIN
- sys_module
volumes:
- /volume1/docker/gluetun:/volume1/docker/gluetun
- /dev/net/tun:/dev/net/tun
- /var/lib:/var/lib
network_mode: service:gluetun
restart: unless-stoppedLooking for some help, join our Discord community
If you are struggling with any steps in the guides or looking to branch out into other containers join our Discord community!

Buy me a beverage!
If you have found my site useful please consider pinging me a tip as it helps cover the cost of running things or just lets me stay hydrated. Plus 10% goes to the devs of the apps I do guides for every year.