Important or Recent Updates
| Historic Updates | Date |
|---|---|
| First version of the setup | 01/08/2021 |
| Added a note regarding the /data share Cleaned up the guide with LanguageTool General formatting updates | 14/03/2022 |
| Swapped out Putty for Terminal (Powershell) | 01/04/2023 |
| Further improvement to user and now group creation (thanks kalmiya) | 23/09/2023 |
It is good practice to set up a unique user and group with limited share and application access for your containers. We won’t ever be using this user to log into DSM it is purely for Docker.
Creating a Group
First up we will create a specific docker group that our docker user will belong, this allows us to segregate the permissions from the normal ‘users’ group from Docker. This is useful as you may have other users on your NAS that you don’t want to have access to certain folders by default.
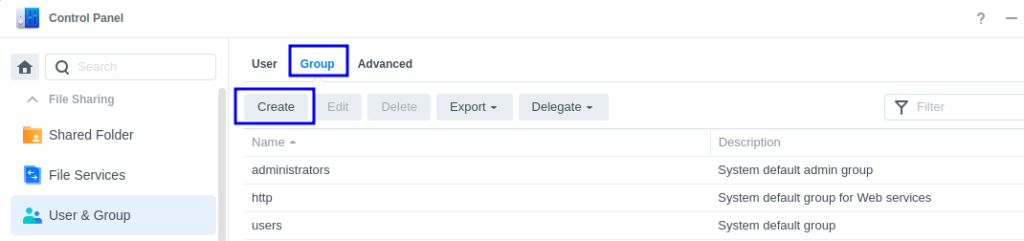
Navigate into the DSM control panel and open up ‘User & Group’ then click on Group and Create
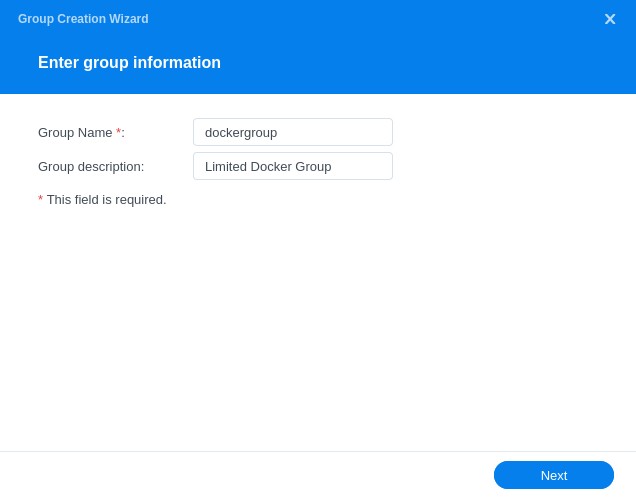
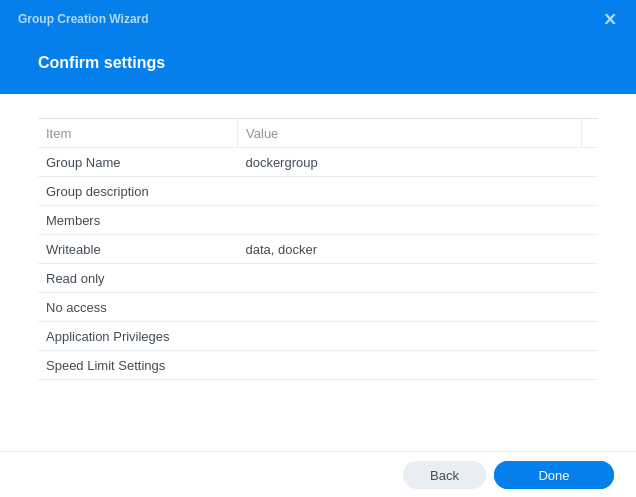
In the screen that appears we will name the group ‘dockergroup’ (imaginative right) and you can give it a description if you wish
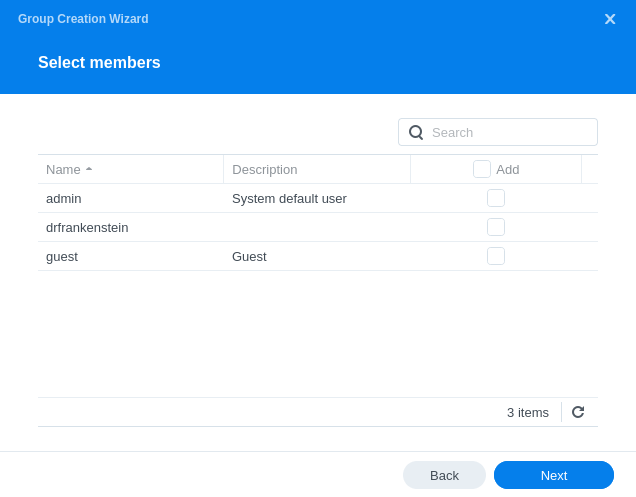
Click Next, we won’t be adding any users to the group yet (that’s the next section)
On the next screen we will grant the Group Read/Write permissions to the ‘data’ and ‘docker’ shares we created in the previous guide. Click Next. (Please note you may not have a ‘data’ share if you are following one of the guides that doesn’t require it!)
On the next screen you do not need to amend the groups Quotas so click Next
We will now deny all access to inbuilt apps as this group and any users within it do not need access.
On the final settings screen we don’t need to set any speed limits
On the final screen click Done.
Creating a User
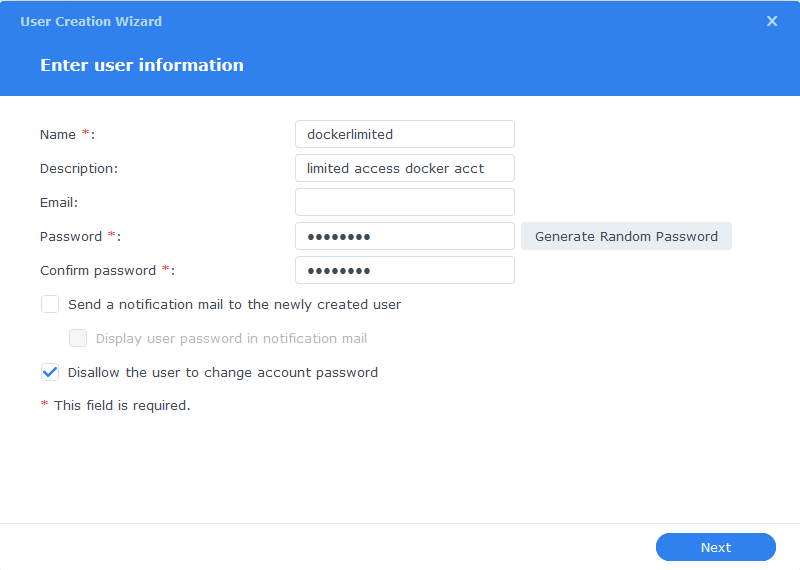
You can call the user whatever you want, I just kept mine simple and created one called ‘dockerlimited’
It’s also a good idea to generate a very strong random password for the user, while it will be a very limited account you don’t want to give it an easy to guess password. You will never need this password for what we are doing.
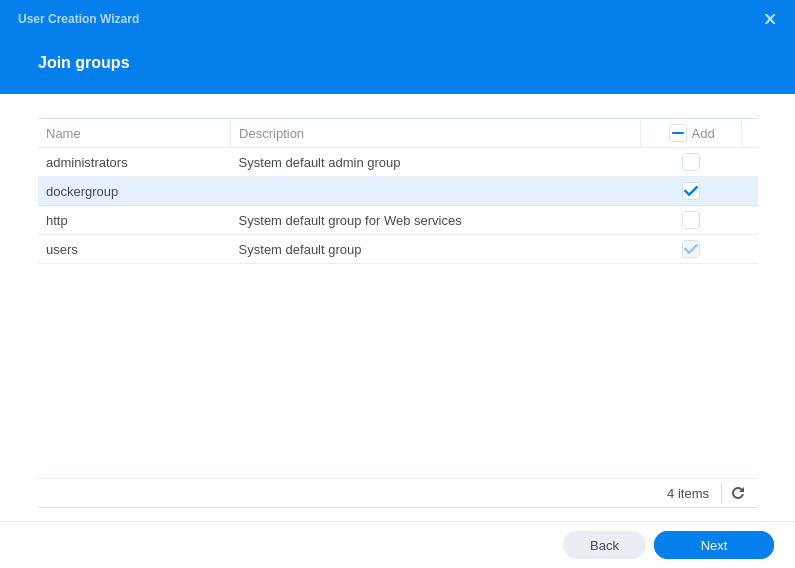
Next we are going to add this new user to the ‘dockergroup’ we just created as we don’t want it having any sort of admin access.
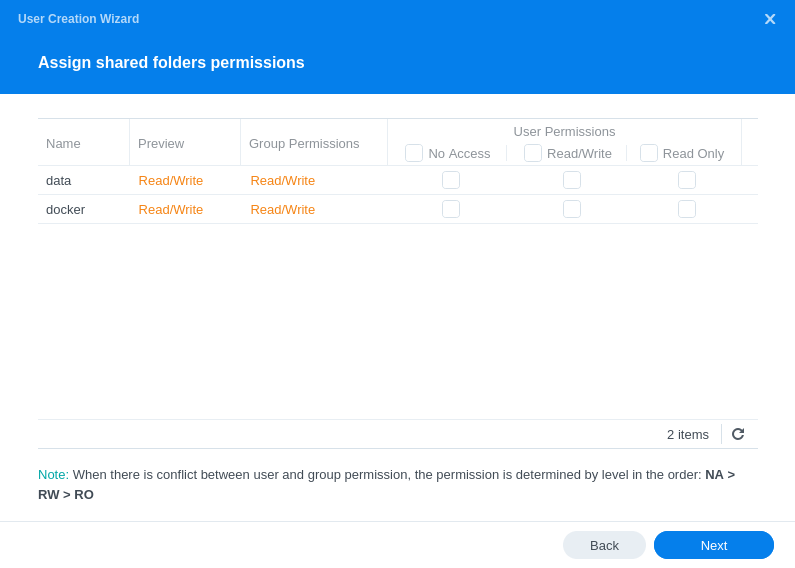
On the next screen you should see that the user already has Read/Write access to the two shares and no others.
*Please note if you are not following one of the media setup guides you will not have the /data share so don’t worry if it is missing.
Nothing to change on the User quota settings just click ‘Next’
You will see that our User already has restricted access to apps
Again we don’t need to set any speed limits for this user so click on ‘Next’
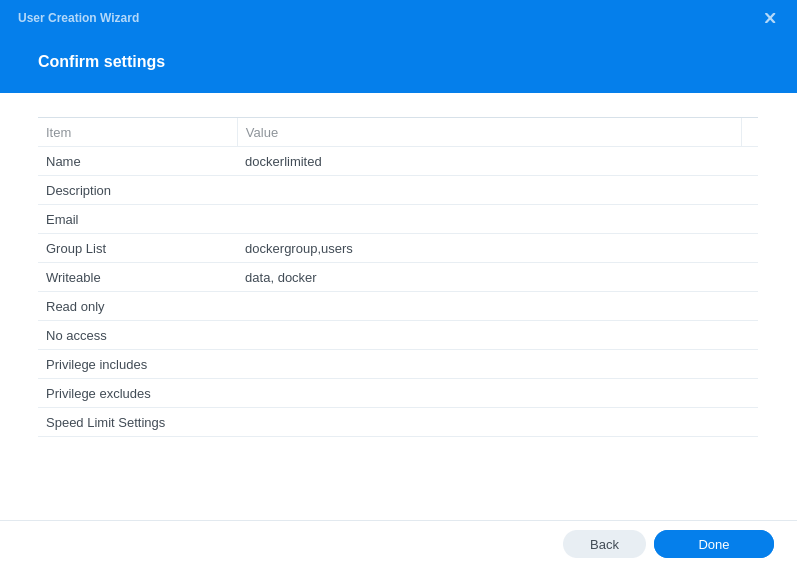
The final screen will just confirm your settings make sure the correct shares are in the ‘Writeable’ list, click on ‘Done’ and your user will be created.
Obtaining the new UID (User ID) & GID (Group ID)
Now we need to obtain the IDs for the new dockerlimited user and dockergroup These are used to pass file permissions through to our containers. They can also be known as PUID and PGID.
You will need to SSH into your Diskstation using ‘Terminal’ which is built in to modern versions of Windows, Linux, or Mac.
Go back into the Control Panel again and enable SSH within the Terminal & SNMP section.
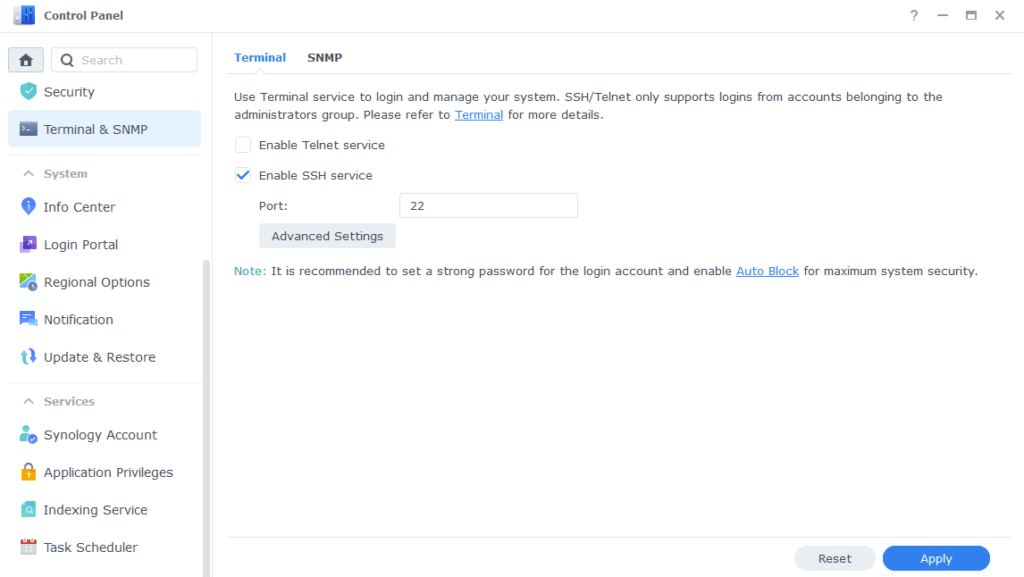
Open up ‘Terminal’
Now type ssh then your main admin account username @ your NAS IP Address and hit Enter (Not the docker user)
ssh drfrankenstein@192.168.0.101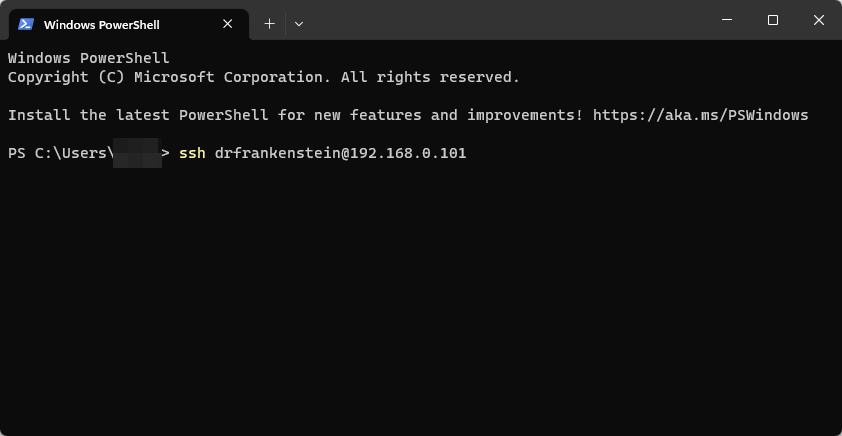
You will then be asked to enter the password for the user you used, you can either type this or right click in the window to paste (you won’t see it paste the info) then press enter.
Once logged in type the below replacing ‘dockerlimited’ with the name of the user you created if you changed it.
id dockerlimitedYou will now see a similar output as the below…
uid=1027(dockerlimited) gid=100(users)groups=100(users),65537(dockergroup)Let’s break this down!
uid=1027(dockerlimited) This is our UID write this down!
gid=100(users)groups=100(users) While this is a GID it is not the one we are interested in as it is for the standard users group so ignore this.
65537(dockergroup)This is our actual GID that we want to use for our containers so write this down as your GID.
You have now successfully set up your limited access user and obtained its IDs for use in Docker. Keep note of these somewhere as you will use them a lot with Docker.
You can now disable the SSH service as we won’t be using it.
You can now go back to the guide you were following.
Permission Fixes
Looking for some help, join our Discord community
If you are struggling with any steps in the guides or looking to branch out into other containers join our Discord community!
Buy me a beverage!
If you have found my site useful please consider pinging me a tip as it helps cover the cost of running things or just lets me stay hydrated. Plus 10% goes to the devs of the apps I do guides for every year.




Security can be hardened by limiting access to the /data/docker/projects folders.
Dockers with the current rights of dockerlimited user could change their own compose.yml and have higher rights after a restart /autoupdate
Hey, we never mount the Docker share to a container just paths above it. So for example all the arrs get.
/volume1/docker/radarr:/config so it can’t access files below this mount point and get across into the projects folder.
Unless I am missing something as happy to change it.
Hey question, do you use this user for all docker containers?
Some guides that for example Mariushosting, use root user or actual user info. I was just wondering if I am going to run into errors with certain containers like pi-hole, using this limited docker user.
I have followed your guides and set up my NAS with your tutorials so thank you so much for your help. I got my Plex server with transcoding working because of you. Thank you!
Hey J.D
Yes where possible we use this user for the containers. For security we want to avoid the root user for the main app inside the container.
Let’s say that a container is compromised by someone or a bot as it was exposed to the internet such as Overseerr. The attacker will be likely working on the basis the internal container user is ‘root’. The root user has complete access to containers’ system files it can remove/amend/delete whatever it wants, this is bad as they could install additional apps and say ransomware the shares that container has access to, while a restricted user only has the ability to run the app or make changes to files it owns. PiHole introduced the ability to run as a non-root user a couple of years ago so in my guide I use this restricted user without issue. I am currently making my way through the guides to add some additional security related changes and investigating if for example I can get AdGuard and Spotweb running as non-root.
Hope that helps.
Having a bit of trouble getting the GID? Like I can see the dockerlimited UID just fine but the GID with the docker group is not there. Link: https://imgur.com/a/b4chkYG
You may have skipped a step, see the one where we add the user to the group.
Next we are going to add this new user to the ‘dockergroup’ we just created as we don’t want it having any sort of admin access.
Yep, that was it! Just didn’t realize that DockerGroup wasn’t selected
Have you tried running the ID command?
I got eveything wotrk, thanks for the awesome guide, incredible work here.
What user are you logging in as? You should be able to login with your standard user account, ignore the error it relates to user homes.